August 12, 2025
Updated: August 12, 2025
The real price of ransomware goes far beyond the ransom. See the data, hidden costs, and strategies to cut millions from your recovery bill.
Mohammed Khalil

Let’s get straight to the point: the average cost of a data breach for a U.S. company has surged to an all time high of $10.22 million in 2025. This isn't just a business problem; it's part of a global cybercrime wave expected to inflict $10.5 trillion in damages annually by 2025.
Many people think the biggest line item in a ransomware attack is the ransom itself. But here’s the catch: that’s completely wrong.
While headlines might focus on multi million dollar ransom demands, the latest data shows that the median payment has actually been cut in half. So, if businesses are paying less to attackers, why is the total
ransomware damage cost exploding? Because the ransom is a tiny fraction of the real price. The true cost is buried in weeks of operational downtime, frantic system rebuilds, massive legal fees, and the long term loss of customer trust.
This guide breaks down the real numbers behind the cost to recover from a ransomware attack in 2025. We’ll dig into the latest data from industry titans like IBM, Sophos, and Verizon, and give you a practical, no fluff playbook based on guidance from CISA and NIST to help you avoid becoming another statistic.
To understand the true financial threat of ransomware, you have to look past the payment demand. The 2025 data reveals a strange paradox: attackers are getting less money in ransoms, but the overall financial damage is worse than ever.
It might sound like good news, but the reasons are complex. The median ransom payment was halved, falling from $2 million to just $1 million. Here’s why:
But don’t celebrate just yet. While direct payouts are down, the total average cost of a ransomware specific incident remains incredibly high at $5.08 million. This proves that the real financial battle isn’t won at the negotiation table, it's won in your preparation.
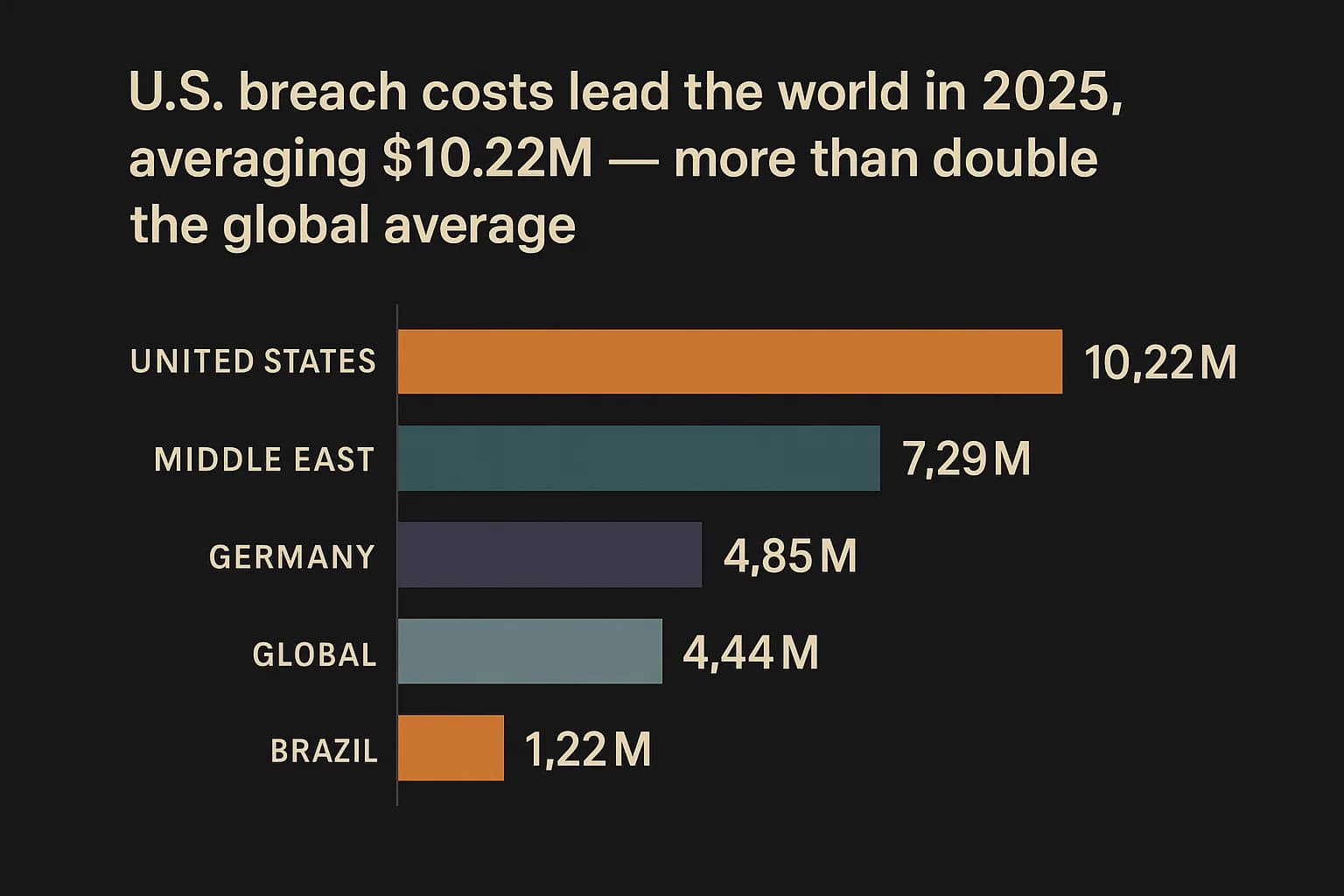
The cost of a breach varies significantly depending on where you operate. The U.S. remains the most expensive place in the world to suffer a data breach, by a wide margin.
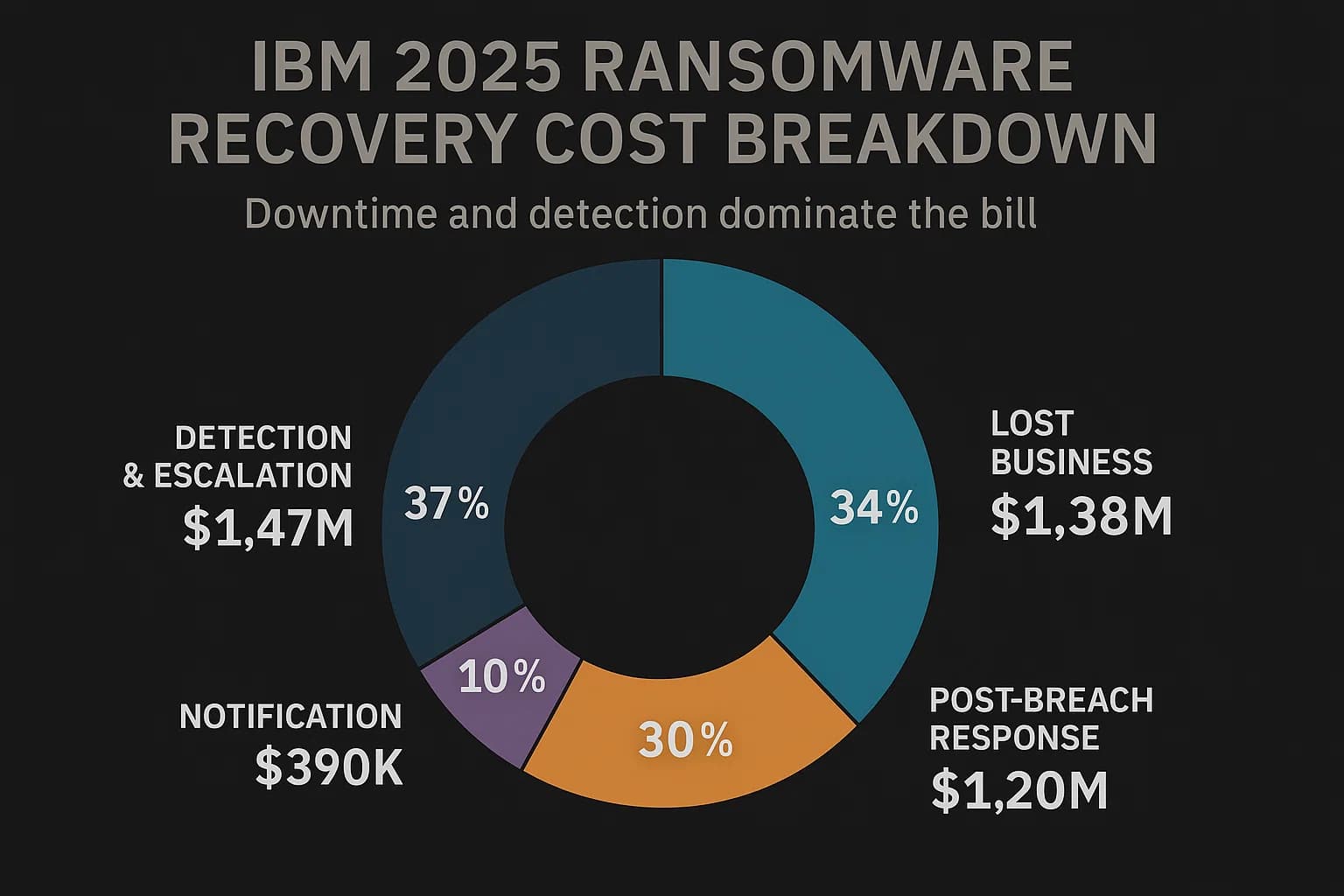
So, if the ransom isn't the main expense, where does all that money go? The multi million dollar bill is a sum of many painful, and often hidden, costs. IBM breaks it down into four main buckets.
Here’s a look at what you’re really paying for:
Quick tip: The cost of a breach is so high that nearly half of all victims end up raising the prices of their own products and services to cover the losses. The financial pain gets passed on to everyone.
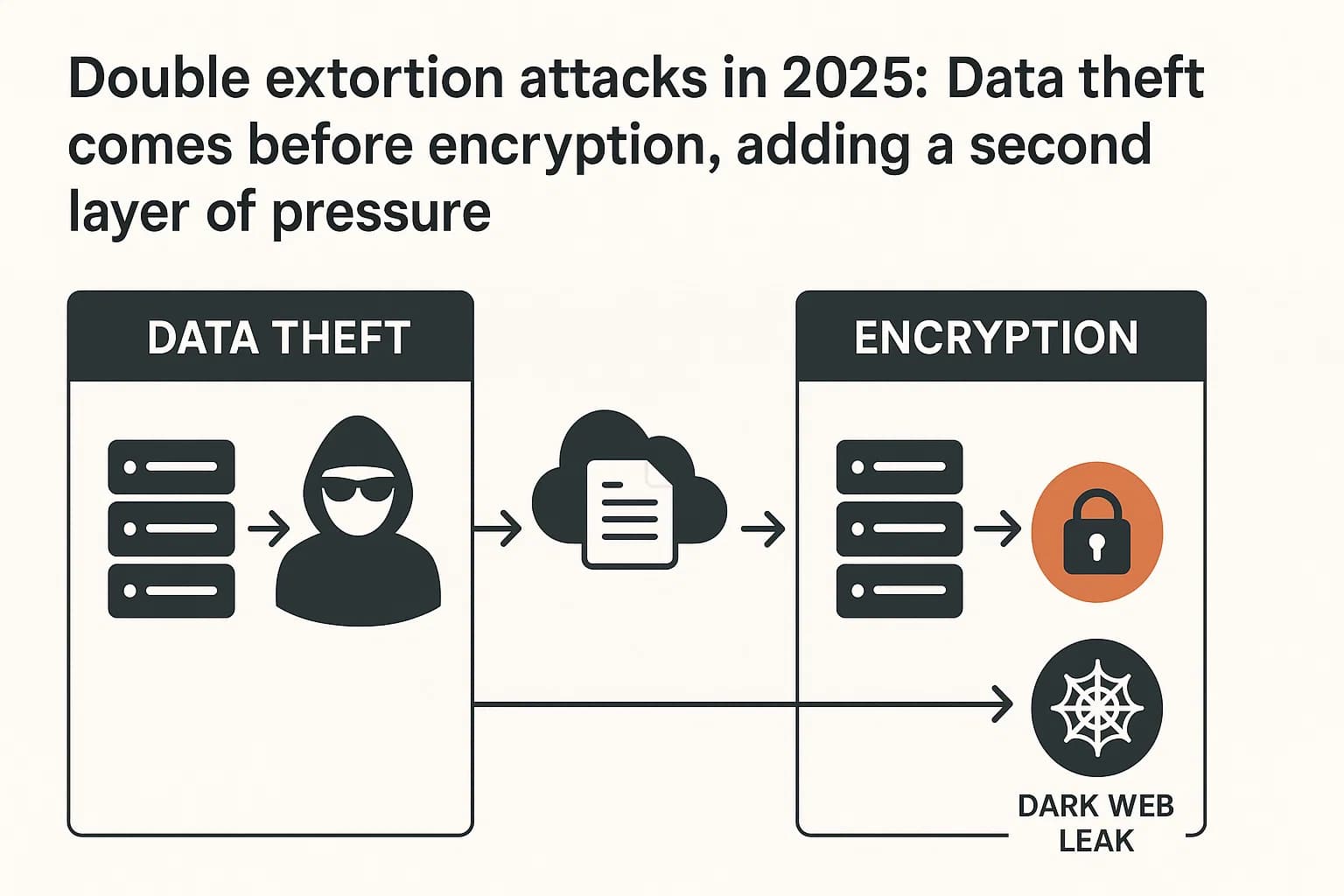
Modern ransomware attacks have evolved beyond simply locking your files. The most dangerous trend today is double extortion, a tactic now used in the vast majority of attacks.
What is double extortion ransomware? It’s a two pronged attack. First, cybercriminals quietly steal copies of your most sensitive data. Then, they encrypt your systems. This gives them two ways to force a payment:
This tactic was created to defeat backups. Even if you can restore your systems, the threat of a massive data leak creates immense pressure to pay up to avoid devastating reputational damage, regulatory fines, and customer lawsuits. Nearly all major ransomware groups now use this method, making data exfiltration prevention a critical part of any defense strategy.
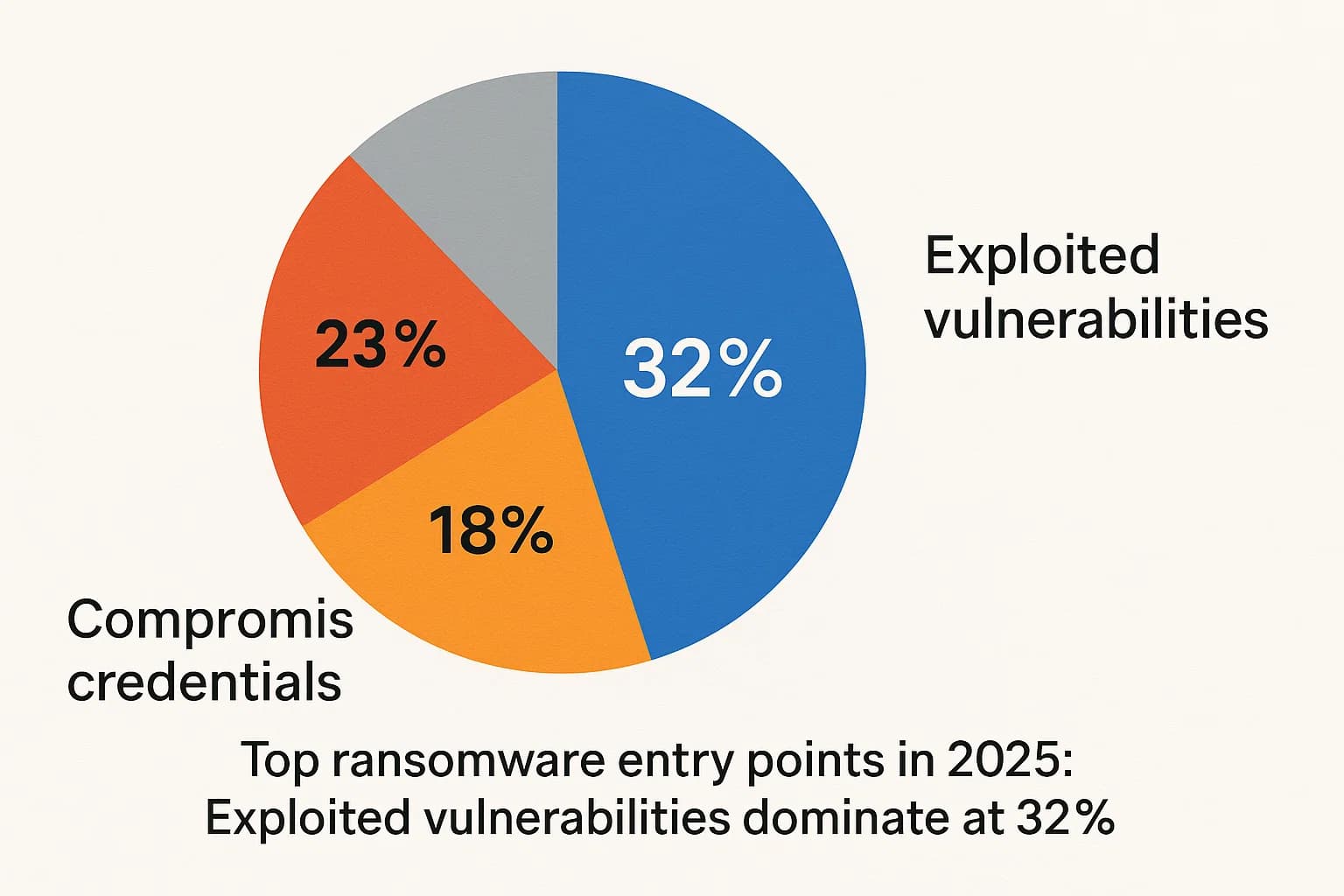
Ransomware attacks don't happen in a vacuum. They succeed because of specific, and often preventable, security failures. The 2025 data is crystal clear about how attackers are getting in.
Underpinning all of this is a critical resource gap. A staggering 63% of organizations admitted that a lack of skilled staff or proper security tools contributed to them getting hit. This is especially true for cyber attacks on small businesses, which are disproportionately affected by ransomware.
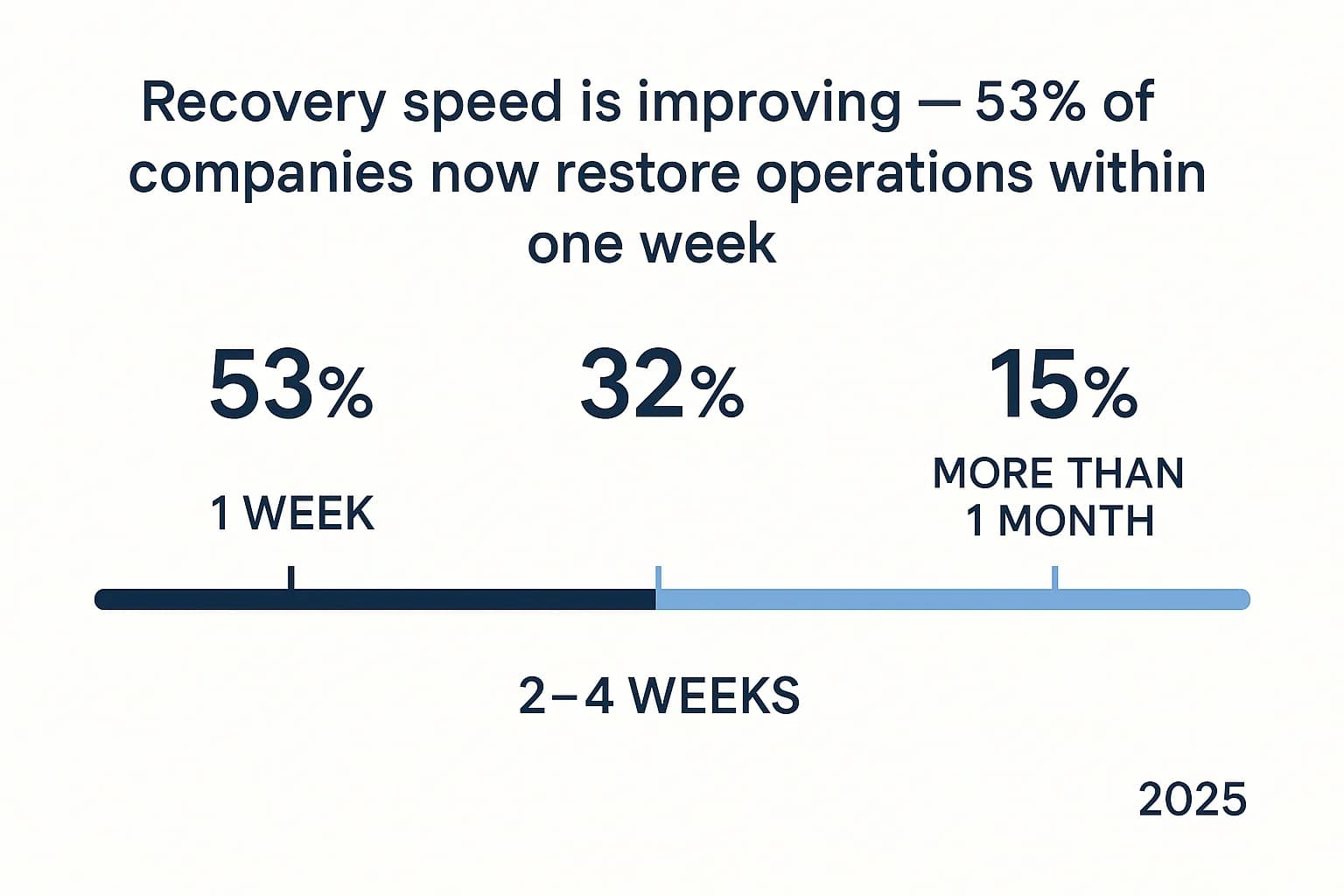
How quickly you can recover determines how much an attack will ultimately cost you. The 2025 data shows some improvements, but also some serious red flags.
Organizations are getting better at responding. 53% of companies were able to fully recover within one week, a big jump from 35% the previous year. This suggests that incident response plans are maturing.
Here’s the paradox. Despite faster recovery, the use of backups to restore data has fallen to a six year low, with only 54% of companies using them. This is deeply concerning because offline, tested backups are the single most important tool for a successful recovery, according to CISA.
So why the disconnect? It seems more attacks are being stopped before data gets encrypted (a six year high of 44%). In these cases, there’s nothing to restore. While that’s a positive trend, relying on detection alone without a solid backup plan is a high stakes gamble.

In June 2024, a massive ransomware attack on CDK Global, a key software provider for the automotive industry, paralyzed operations at over 15,000 car dealerships. The total direct losses for dealers were estimated to be over
$1 billion, stemming from lost sales, service disruption, and extra staffing costs. This incident is a stark reminder of how a single supply chain attack can cause widespread, catastrophic financial damage.
The cost and pain of recovery aren't the same for everyone.

For small and medium-sized businesses (SMBs), a ransomware attack isn't just a costly inconvenience it can be a death sentence.
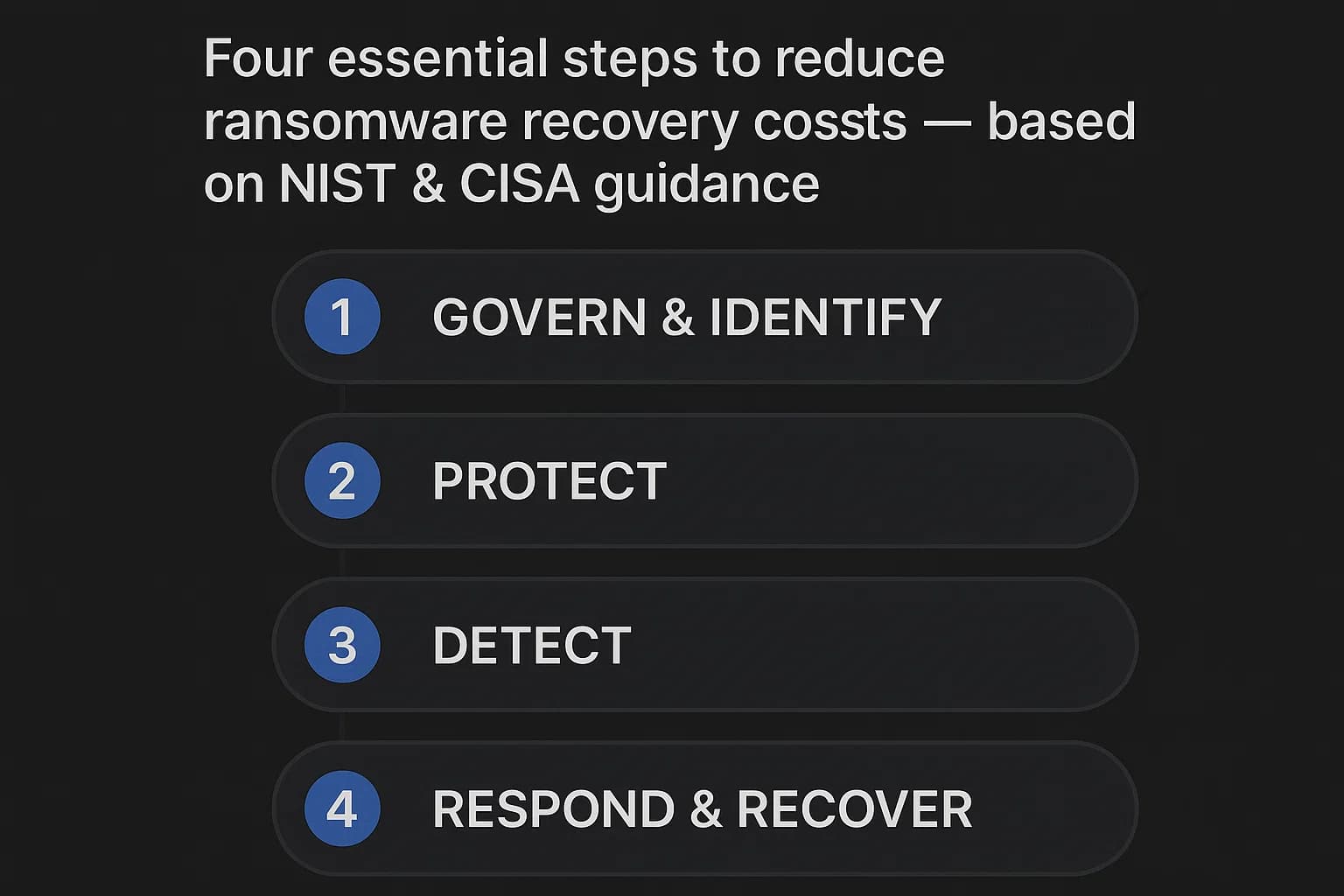
Hoping you won't get hit is not a strategy. Building financial resilience requires a proactive, framework driven approach. Here’s a practical checklist based on guidance from the NIST Cybersecurity Framework for Ransomware Risk Management and the CISA Ransomware Prevention and Response Guide to protect your business.
Step 1: Get Your House in Order (Govern & Identify)
Step 2: Build Your Defenses (Protect)
Step 3: Sharpen Your Senses (Detect)
Step 4: Plan Your Counter Attack (Respond & Recover)
1. What is the average ransomware recovery cost in 2025?
The average cost to recover from a ransomware attack is $1.53 million, not including the ransom. However, the total cost of a data breach in the U.S. is much higher, averaging a record $10.22 million.
2. Is paying the ransom the biggest part of the cost?
No, not even close. The ransom is a small fraction of the total cost. The biggest expenses come from business downtime, system restoration, legal fees, and reputational damage.
3. How can a company reduce ransomware costs?
Proactive defense is key. This includes timely patching, using phishing resistant MFA, maintaining and testing offline backups, and having a well rehearsed incident response plan. Investing in security AI and automation can save an average of $1.9 million.
4. How long does ransomware recovery typically take?
Recovery is getting faster. 53% of organizations now recover within one week. However, the full breach lifecycle, from initial compromise to full containment, still takes an average of 241 days.
5. Which industry has the highest ransomware recovery costs?
Healthcare has the highest overall data breach costs, averaging $7.42 million per incident. This is driven by strict regulatory penalties (HIPAA) and the high cost of operational disruption to patient care.
6. What is double extortion ransomware?
It's when attackers steal your data before encrypting it. They then demand two ransoms: one to unlock your files and another to prevent them from leaking your sensitive data online. This is now a standard tactic.
The threats of 2025 demand more than just awareness; they require readiness. The latest data on ransomware payout statistics and trends for 2025 and overall cybercrime trends and costs 2025 show that if you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us