August 4, 2025
Updated: August 4, 2025
Why global ransomware payments dropped but average victim costs surged to record highs.
Mohammed Khalil

The question on every business leader's and security professional's mind in 2025 is no longer if they will face a ransomware threat, but what that threat will look like and what it will cost. The statistics on ransomware payouts paint a complex and often contradictory picture. On one hand, the total amount of money flowing to cybercriminals saw a significant drop in 2024. On the other, the cost for an individual victim who feels forced to pay has never been higher. This report unpacks that paradox.
This isn't just another collection of statistics; it's a strategic analysis of the forces reshaping the ransomware battlefield. We'll dissect the global payment trends, explore why some industries are paying multi million dollar ransoms while others hold the line, and examine the fallout from law enforcement's unprecedented success in disrupting the world's most notorious ransomware gangs.
Understanding these dynamics is critical right now because the adversary has evolved. The era of monolithic ransomware as a service (RaaS) empires is giving way to a more fragmented, unpredictable ecosystem. Attackers are shifting from purely technical exploits to sophisticated social engineering, targeting the human element with chilling precision. They are no longer just encrypting data; they are weaponizing it through double, triple, and even quadruple extortion tactics designed to maximize business disruption and force a payment.
This report provides the definitive ransomware payout statistics for 2024 2025, offering the data driven context you need to build a resilient defense against the threats of today and tomorrow.
For those who need the bottom line upfront, here are the most critical ransomware payout statistics shaping the current landscape:
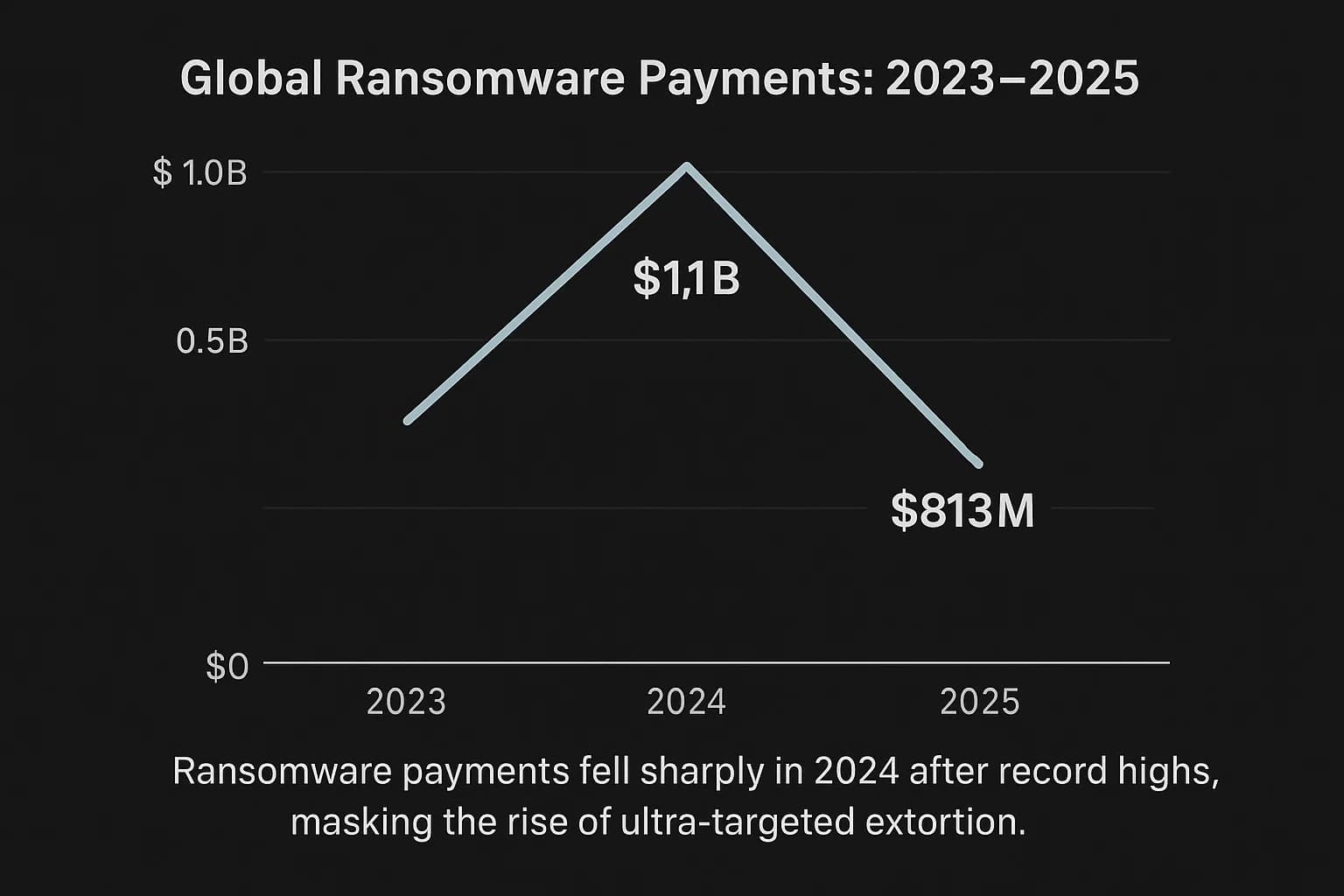
The top line figures of the ransomware economy tell a story of extreme volatility. After a landmark year in 2023 where payouts breached the billion dollar threshold for the first time, 2024 saw a dramatic reversal. However, these aggregate numbers conceal the granular trends that reveal the true nature of the modern ransomware threat: a shrinking overall market where the stakes for individual, high value targets have become dangerously high.
The ransomware economy experienced a significant contraction in 2024 after reaching an unprecedented peak the year before. In 2023, total global payments made by victims to ransomware gangs soared to an estimated $1.1 billion, a record breaking figure that marked the first time the billion dollar line had been crossed. This surge was not an anomaly but the culmination of several powerful trends, most notably the success of hyper prolific supply chain attacks like the one orchestrated by the Cl0p gang against the MOVEit file transfer service, which compromised data from thousands of organizations in a single campaign.
However, 2024 witnessed a sharp downturn. According to blockchain analysis from firms like Chainalysis, total payments fell by approximately 35% to around $813.6 million. This decline was not a steady slide but a tale of two halves. The first half of 2024 was on track to surpass 2023's record, with payments reaching nearly $460 million by June. The drop was concentrated in the second half of the year, a direct consequence of escalating pressure from law enforcement and a fundamental shift in victim behavior.
This up and down pattern, a dip in 2022 often attributed to the disruption of Russian speaking gangs like Conti following the invasion of Ukraine, a massive rebound in 2023, and a sharp fall in late 2024 highlights the fragile and reactive nature of the cybercrime landscape. The 2024 decline was not driven by a decrease in attacks; in fact, the number of publicly reported ransomware incidents reached an all time high that year. Instead, the fall in revenue points to a disruption in the attackers' business model. The two primary drivers, which we'll explore in greater detail, were aggressive and coordinated international law enforcement operations that dismantled top tier gangs and a growing, hardened resolve among victims who are now better equipped and more willing to recover without paying the ransom. The result is a criminal market in flux, where launching attacks is still easy, but successfully monetizing them has become significantly harder.
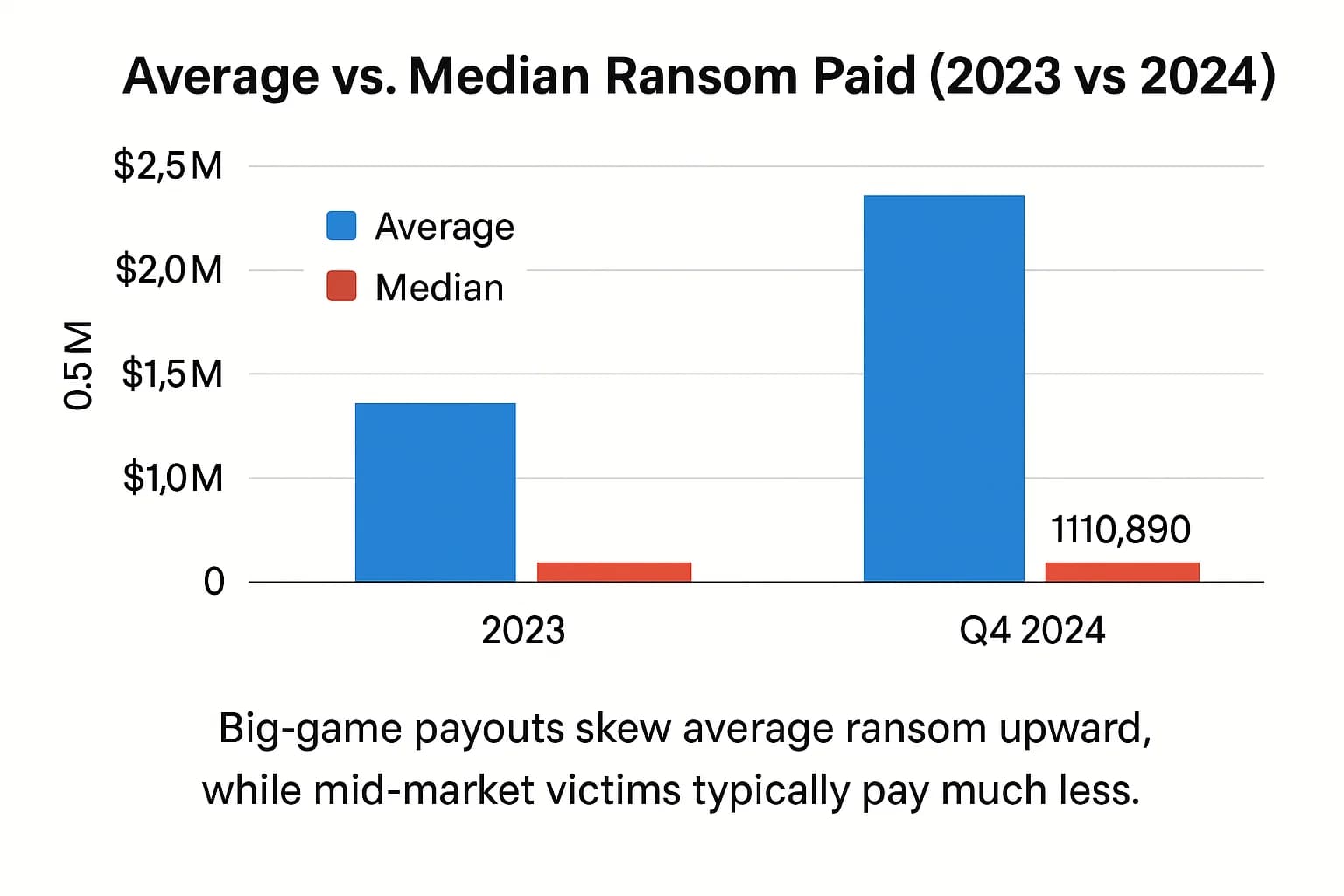
Beneath the surface of the shrinking global payout total lies a critical and alarming trend: the cost for an organization that does pay a ransom has exploded. This divergence is best understood by comparing the average and median payment amounts, which reveals a clear split in the ransomware market between "big game" targets and everyone else.
According to a global survey by news sophos, the average ransom payment surged by an astonishing 500%, climbing from approximately $400,000 in 2023 to $2.0 million in 2024. This figure is heavily skewed by the increasing prevalence of multi million dollar extortion events. In 2024, 63% of all ransom demands were for $1 million or more, signaling a definitive shift by attackers toward high value targets. A single record breaking payment of $75 million was made in 2024, which alone can dramatically pull up the average.
The median ransom payment, which represents the typical "middle of the road" victim experience and is less affected by extreme outliers, tells a more nuanced story. Data from incident response firm Coveware shows significant volatility. The median payment hit an all time high of $250,000 in the first quarter of 2024 before plummeting by 45% to $110,890 in the fourth quarter. This Q4 drop suggests a flurry of attacks against smaller organizations or a higher rate of non payment toward the end of the year. Meanwhile, Sophos's latest 2025 report, which surveyed victims from the previous 12 months, found a median payment of $1 million, down from $2 million in their prior report.
This widening gap between average and median figures is the statistical footprint of a bifurcated ransomware strategy. The "average" is being dragged upward by a small number of massive enterprises paying eight figure ransoms, while the "median" reflects the more common, yet still crippling, six figure reality for the mid market. This stratification is a direct result of the RaaS ecosystem's fragmentation. With large, efficient syndicates like LockBit disrupted, highly skilled affiliates are now operating more independently. They may be launching fewer attacks, but they are focusing their considerable talent on targets where the potential payout justifies the effort and risk, fundamentally changing the risk calculus for large corporations.
It's also crucial to note that the initial demand is rarely the final price. Victims have become more adept at negotiation, with data showing that fewer than a quarter of organizations pay the full asking price. Sophos found that 53% of victims paid less than the initial demand, while Chainalysis notes that the gap between the amount demanded and the amount paid grew to 53% in the second half of 2024.
The decision to pay a ransom is one of the most difficult a leadership team can face. It's a complex calculation involving operational downtime, financial cost, reputational damage, and ethical considerations. In recent years, a clear trend has emerged: while the pressure tactics from attackers have intensified, victim resilience has grown even faster, leading to a historic shift in who pays and why.
The single most optimistic trend in the fight against ransomware is the growing refusal of victims to pay. This isn't based on hope, but on hard data from incident response firms on the front lines. Coveware reported that in the fourth quarter of 2024, the percentage of victims who paid a ransom fell to an all time low of 25%. This landmark figure means that three out of every four organizations they assisted were able to restore operations and manage the incident without funding the criminals. This represents a sea change from just a few years ago when payment rates were often above 50%.
This trend is not an accident; it is the result of three powerful forces converging:
This decline in the payment rate is the most significant existential threat to the ransomware business model. Ransomware is a crime of profit, calculated on a simple ROI. When the "conversion rate" , the percentage of attacks that result in a payout plummets, the entire economic model begins to fail. It forces attackers to work exponentially harder for each dollar, creating a powerful market driven deterrent.
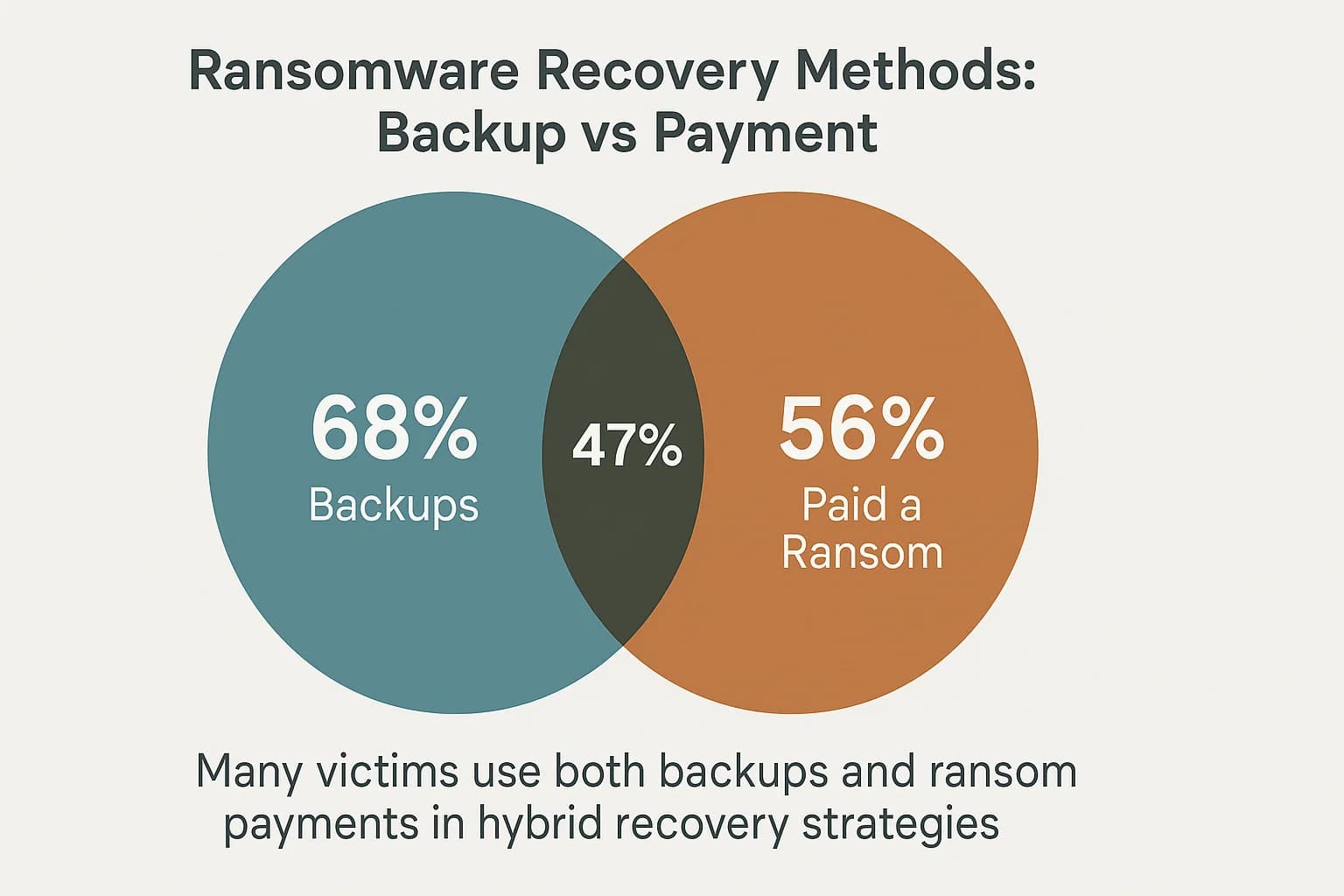
Here’s the deal: while robust backups are the cornerstone of ransomware resilience, the idea that they are a complete silver bullet is a dangerous myth in the modern threat landscape. The evolution of attacker tactics, specifically the rise of "double extortion," has complicated the recovery calculus for many victims.
This is the key to understanding the statistical discrepancy between different reports. While a frontline incident response firm like Coveware, which is often engaged when a company is determined to recover without paying, sees a 25% payment rate, a broader survey from Sophos finds a much higher 49% payment rate among victims whose data was encrypted.
The reason for this gap is data exfiltration. Modern ransomware attacks are rarely just about encryption anymore. The standard playbook now involves a preliminary step where attackers silently steal massive volumes of sensitive data before they deploy the ransomware to encrypt systems. This creates a second layer of extortion: even if the victim can restore their operations from backups, the attackers still hold their most sensitive data hostage, threatening to leak it publicly on the dark web.
This tactic is incredibly effective. The Verizon found that ransomware was a component in 44% of all data breaches, a dramatic increase from the previous year, highlighting how intertwined encryption and data theft have become. This leads to what is now a common "hybrid response" scenario. An organization may use its backups to restore servers and get the business running again, but it will simultaneously negotiate and pay a ransom, often a smaller amount, solely to receive a "promise" that the stolen data will be deleted. Sophos's data clearly illustrates this overlap: while 68% of organizations were able to restore data from backups, 56% still ended up paying a ransom. A full 47% of victims used multiple recovery methods, meaning they paid a ransom and used backups.
This dynamic explains why the payment rate for pure data extortion attacks (where no encryption occurs) is often higher than for traditional ransomware attacks. When backups are irrelevant to the threat, the attacker's leverage is purely about the sensitivity of the stolen data and the victim's fear of reputational damage, regulatory fines, and customer lawsuits. This highlights why proactive measures like a robust vulnerability assessment vs penetration testing program are critical to prevent initial access in the first place.
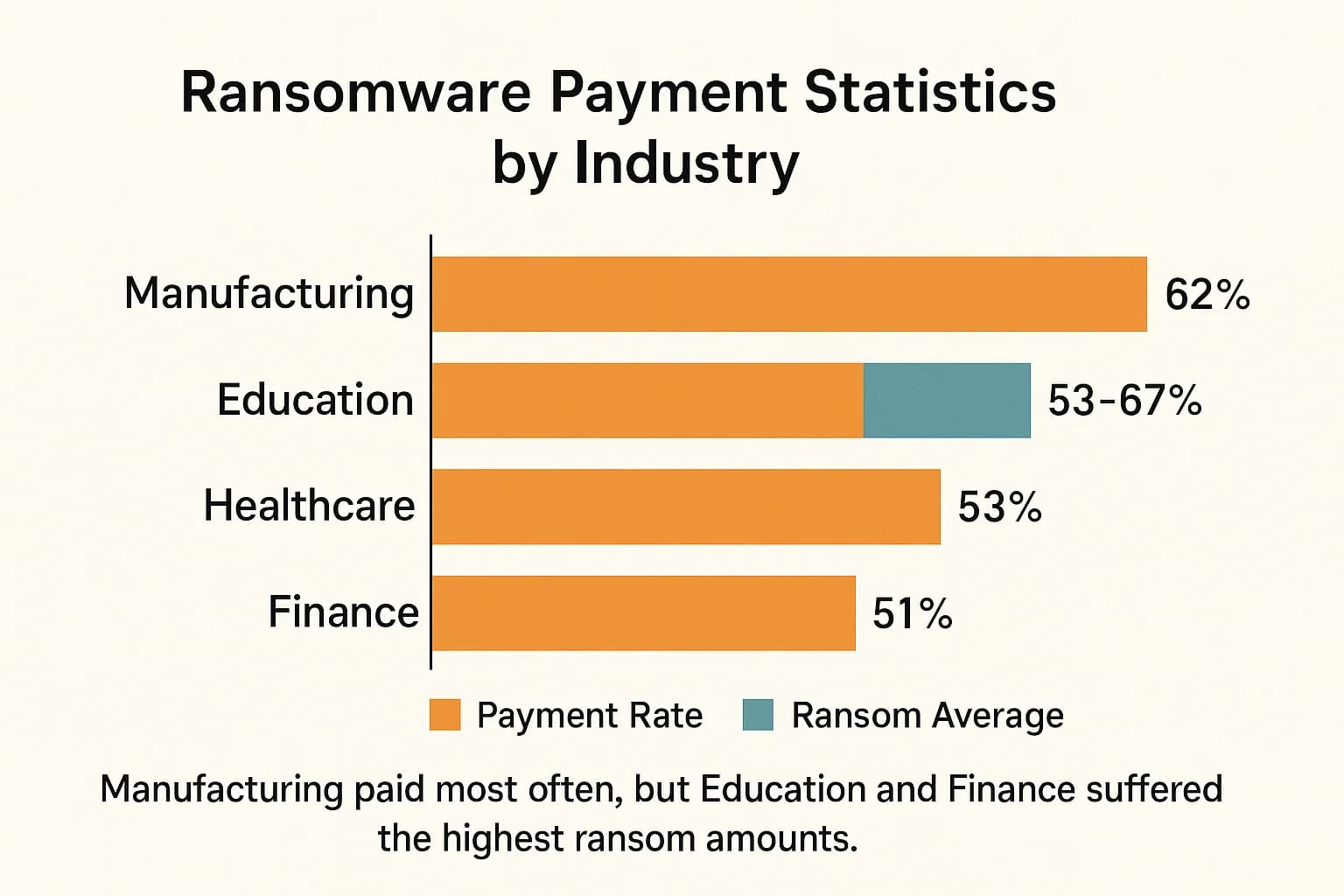
Ransomware is not a monolithic threat; it impacts different industries in vastly different ways. Attackers tailor their targets and tactics based on a sector's operational pressures, regulatory environment, and perceived ability to pay. The following analysis breaks down the unique challenges and payment trends across key industries, revealing a diverse battlefield where the cost of an attack is measured not just in dollars, but in public safety, economic stability, and institutional trust.
The healthcare sector remains one of the most embattled fronts in the war on ransomware. Attackers target hospitals and providers with the cynical understanding that the life or death urgency to restore patient care creates immense pressure to pay. With an attack rate of 67% in the past year, it is one of the most frequently targeted sectors.
The data reveals a sector struggling to cope. The propensity of healthcare victims to pay a ransom jumped significantly in 2024, with 53% of attacked organizations paying to recover data. When they do pay, the sums are substantial: the median ransom payment was $1.5 million, while the average soared to $4.4 million, skewed by several massive incidents. Attackers are particularly successful in this sector at neutralizing a victim's primary defense, with a 66% success rate in compromising or destroying backups, effectively forcing the victim's hand.
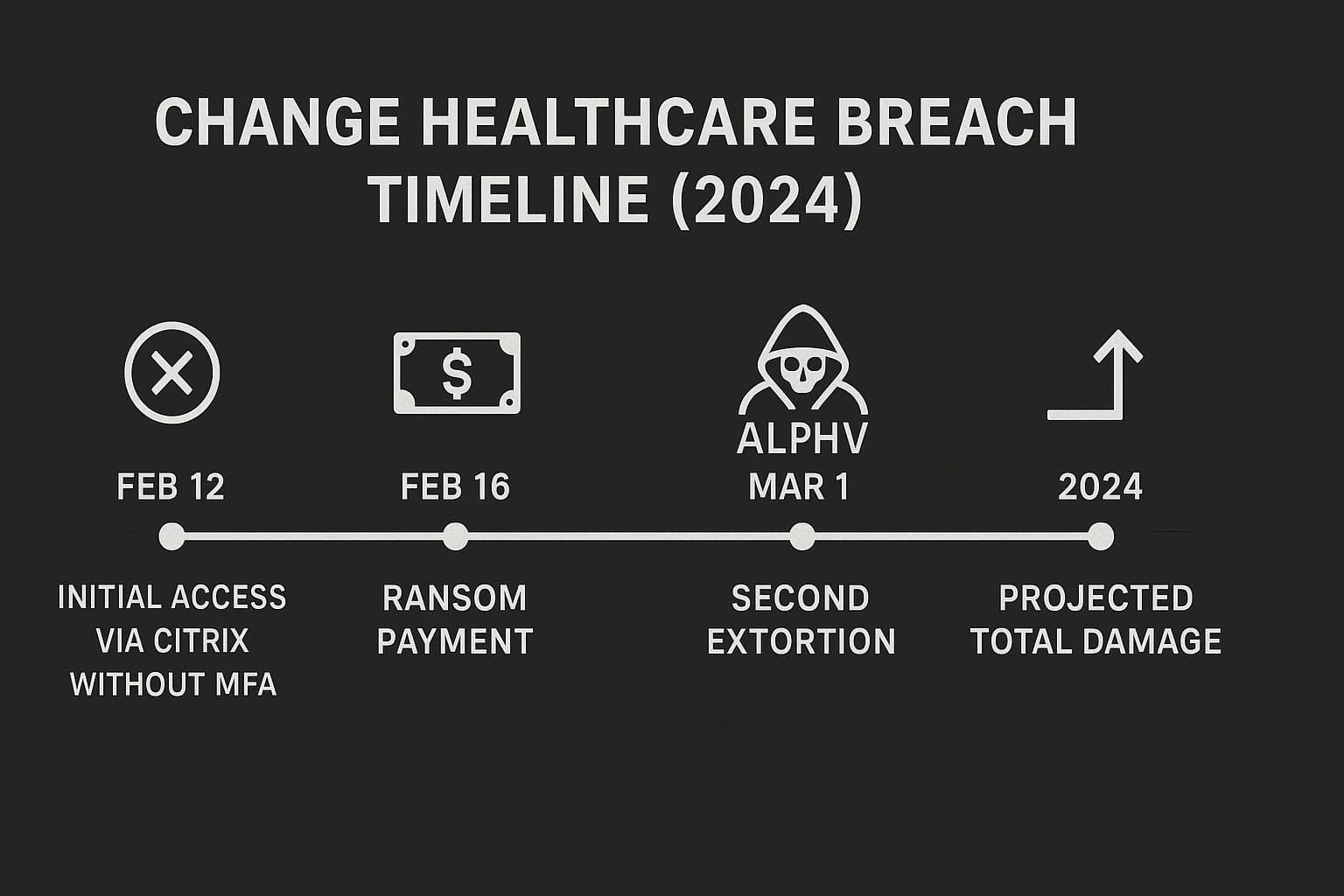
The catastrophic Change Healthcare attack in February 2024 serves as a defining case study for the entire industry. Attackers from the ALPHV/BlackCat ransomware group gained access through a Citrix remote access portal that tragically lacked multi factor authentication (MFA). The resulting system wide encryption paralyzed the U.S. healthcare payment infrastructure, disrupting pharmacies, hospitals, and clinics nationwide. UnitedHealth Group, Change's parent company, ultimately confirmed it paid a $22 million ransom. In a devastating twist that underscores the futility of trusting criminals, a second ransomware group later emerged, claiming to possess the same stolen data and demanding another payment. The total financial fallout from the incident for UnitedHealth Group is projected to exceed a staggering $2.4 billion, a figure that includes recovery costs and financial assistance to providers, dwarfing the ransom itself. For providers, validating defenses against these tactics is non negotiable, making a HIPAA penetration testing checklist an essential part of their risk management strategy.
The financial services sector presents a paradox for attackers. On one hand, it is a bastion of mature security programs and robust defenses. On the other, the sheer value of its data and the critical importance of maintaining customer trust mean that when an attack does succeed, the stakes are astronomical.
The sector's defensive strength is evident in the data: it boasts the lowest encryption rate of any industry. In 2024, only 49% of ransomware attacks on financial firms resulted in data encryption, a sharp fall from 81% the previous year, indicating that their incident response teams are highly effective at stopping attacks in progress.
However, when extortionists do gain leverage, financial firms are often willing to pay to mitigate the damage. About 51% of financial services victims paid a ransom in 2024. These payouts are among the highest of any sector, with a median payment of $2.0 million. This reflects the high value of the data at risk and the catastrophic potential of a major data leak. Despite the high payouts, these firms are also skilled negotiators, with only 18% paying the full initial demand, demonstrating a calculated approach to managing the crisis. For these organizations, adhering to stringent security frameworks is paramount, and validating compliance through assessments like those outlined in the PCI DSS penetration testing guide is a routine part of their defense in depth strategy.
The manufacturing and production sector has rapidly become a top target for ransomware gangs, who have identified its operational model as uniquely vulnerable to extortion. The industry's reliance on just in time production, complex operational technology (OT) environments, and interconnected supply chains means that any downtime can have immediate and cascading financial consequences.
This vulnerability is reflected in the statistics. The sector saw a significant increase in attacks, with 65% of manufacturing organizations hit in 2024. More alarmingly, it reported the highest rate of ransom payment of any industry, with a staggering 62% of victims paying to recover their data. This figure is nearly double the rate from the previous year, indicating that attackers' tactics are proving highly effective.
The median payment in manufacturing was $1.2 million, a substantial sum that highlights the financial pain these attacks inflict. The high payment rate persists even when companies have viable backups (58% were able to restore from them). This suggests that the pressure to avoid costly production stoppages and supply chain disruptions is so intense that many firms view paying the ransom as the fastest, albeit most painful, path back to operational normalcy. This makes understanding and mitigating common network vulnerabilities in 2025 a critical priority for the entire sector.
Cybercriminals perceive the education sector from K 12 school districts to large universities as an ideal target: often under resourced in cybersecurity, yet under immense public pressure to maintain operations for students and communities. This combination has led to some of the most shocking ransom payment statistics of any industry.
While attack rates dipped slightly in 2024, they remain incredibly high, with around 63% of lower education and 66% of higher education institutions reporting attacks. When these attacks succeed, the payouts are astronomical. The median ransom payment in 2024 was a staggering $6.6 million for K 12 schools and $4.4 million for higher education.
These enormous figures are driven by the attackers' ruthless extortion tactics. The education sector is highly susceptible to paying more than the initial ransom demand; 55% of K 12 schools and 67% of universities that paid ended up exceeding the first ask. This happens because attackers are exceptionally successful at compromising this sector's backups (a 71% success rate), leaving the institution with no other recovery option. Once the attackers know the victim is trapped, they raise the price. The consequences are devastating, with the average total cost to remediate an incident in lower education more than doubling in one year to $3.76 million, even before the ransom is paid.
Government agencies, from local municipalities to federal bodies, are targeted by ransomware more frequently than any other sector, with a reported attack rate of 68%. Comparitech data shows a 65% surge in attacks against government entities in the first half of 2025 compared to the same period in 2024, with the United States being the most heavily targeted nation.
The response from this sector, however, is complicated by a growing movement toward policies that ban ransom payments. Governments in the UK and some U.S. states are advancing legislation to prohibit public sector entities from paying ransoms, a strategy aimed at removing the financial incentive for attackers. This makes payout statistics for the government sector difficult to interpret. While some reports have noted a very high median payment of around $6.6 million for central government victims, this is likely skewed by a few major outliers or incidents where cyber insurance policies covered the payment.
More often, government entities are forced to absorb massive recovery costs rather than pay. The demands themselves can be enormous, such as the $12 million ransom demanded from Slovakia's national mapping agency, which the government refused to pay. This policy dilemma places an even greater emphasis on resilience and adherence to rigorous security standards, making frameworks like the one for federal contractors critical. For these entities, understanding the requirements of FedRAMP penetration testing is a key component of their defensive strategy.
The character of the ransomware threat is defined by the criminals who perpetrate it. The period from 2024 to 2025 will be remembered as a time of unprecedented upheaval in the cybercrime underworld. The dominant, seemingly untouchable empires of the past have crumbled under the weight of global law enforcement action and internal strife, giving rise to a new, more chaotic landscape of smaller, faster, and more diverse adversaries.
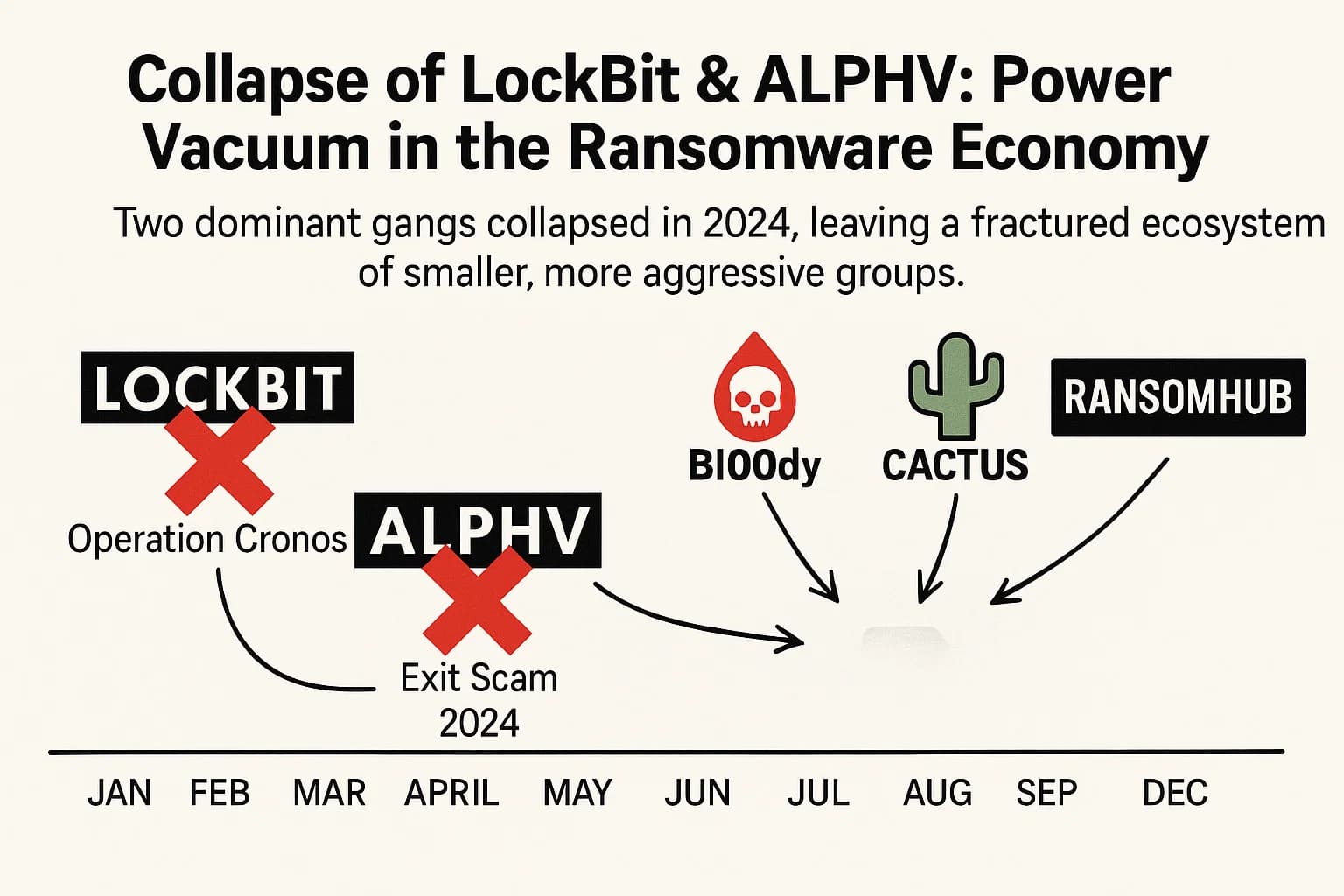
For years, the ransomware as a service (RaaS) market was dominated by a few major brands that operated like criminal franchises, providing malware, infrastructure, and negotiation platforms to a vast network of affiliates. In early 2024, law enforcement delivered a devastating one two punch that decapitated the two most powerful groups: LockBit and ALPHV/BlackCat.
Operation Cronos, a coordinated international effort led by the U.S. FBI and the U.K.'s National Crime Agency in February 2024, systematically dismantled the LockBit operation. Authorities seized critical infrastructure, made arrests of key developers and affiliates, and, in a significant victory for victims, obtained over 1,000 decryption keys that could be used to restore data without a ransom. The operation didn't stop there; law enforcement maintained pressure on the group throughout the year, degrading its ability to operate and eroding its reputation in the criminal underground.
At around the same time, the ALPHV/BlackCat gang, another market leader, imploded from within. In a stunning act of self sabotage, the gang's administrators executed an "exit scam," shutting down their infrastructure and absconding with millions of dollars in ransom payments that were owed to their own affiliates. This act of betrayal sent shockwaves through the RaaS ecosystem, shattering the fragile trust that underpins the affiliate based business model.
The combined effect of these two events created a massive power vacuum. More importantly, they sowed deep distrust and paranoia among cybercriminals, making it exceedingly difficult for any single new RaaS brand to achieve the scale, efficiency, and "brand loyalty" that LockBit and ALPHV once commanded.
With the old guard dethroned, the ransomware landscape has fragmented. In place of a few dominant players, there is now a churning, volatile ecosystem of dozens of mid tier groups, rebranded operations, and new entrants all competing for a piece of the market. By mid 2024, no single ransomware variant accounted for more than about 11% of attacks, a stark contrast to the days when LockBit alone was responsible for a huge share of incidents.
Several groups have risen to prominence in this new era:
Another significant development is the rise of the "lone wolf" attacker. Following the collapse of major syndicates like Conti and LockBit, many experienced affiliates have chosen to go independent rather than join another RaaS program. These skilled individuals now operate solo, carrying out a significant portion of attacks without affiliation to a major brand. This further complicates attribution and defense, as defenders face a more diverse array of individual adversaries rather than a few monolithic groups. To gain a broader perspective on the threats these groups pose, it's useful to understand the different malware attack types and infection trends.
The most sophisticated ransomware actors of 2025 are moving beyond purely technical exploits and are increasingly targeting the weakest link in any organization's security chain: its people. While exploiting unpatched software vulnerabilities remains a primary entry point, the latest trends show a marked shift toward identity based attacks and advanced social engineering.
The playbook of the group known as Scattered Spider (also tracked as UNC3944) epitomizes this evolution. This group specializes in bypassing technical controls by manipulating human trust. Their tactics include:
This focus on identity compromise is a direct response to improved technical defenses. When attackers can't find a vulnerability to exploit, they simply "log in" using stolen credentials. This is why a comprehensive understanding of threats must include not just ransomware, but also the methods used to facilitate it, as detailed in this real world account takeover case study and analysis of phishing attack trends and statistics (2025).
In addition to targeting people, advanced groups are also shifting their focus to core infrastructure. A particularly devastating tactic gaining popularity is the direct targeting of virtualization platforms like VMware's vSphere and ESXi hypervisors. By gaining administrative access to vCenter, attackers can deploy ransomware across dozens or even hundreds of servers simultaneously, causing maximum operational disruption with a single stroke.
Finally, the emergence of generative AI is beginning to act as a force multiplier for criminals. Attackers are using AI tools like ChatGPT to craft highly convincing, grammatically perfect phishing emails at scale, and even to assist in writing malicious code. This lowers the barrier to entry, allowing less skilled actors to execute more sophisticated attacks.
The role of cyber insurance in the ransomware crisis is one of the most debated topics in cybersecurity. Once seen by some as a passive backstop that inadvertently fueled ransom payments, the insurance industry has evolved into an active and powerful force that is fundamentally reshaping how organizations prepare for and respond to attacks.
The cyber insurance market of 2025 is a world away from that of just a few years ago. After a period of intense volatility and skyrocketing premiums, the market has entered a period of relative stability. Rates began to soften in 2024 and have remained flat or even decreased for many policyholders into 2025.
This newfound stability, however, has come with a significant trade off: drastically stricter underwriting requirements. To secure coverage today, organizations can no longer simply fill out a form. They must affirmatively demonstrate a mature security posture. Insurers are now mandating a specific baseline of technical and procedural controls as a prerequisite for eligibility. While the exact requirements vary by carrier, a common set of non negotiable controls has emerged :
This shift has had a profound effect on the market. The cyber insurance industry is now, in effect, setting a de facto cybersecurity standard for businesses. The financial incentive to obtain affordable coverage has become a powerful lever for CISOs and IT leaders to justify security budgets and drive the adoption of best practices. This market driven mechanism is proving to be a highly effective way to raise the collective security posture across industries, transforming insurance from a reactive financial instrument into a proactive catalyst for cyber resilience. Meeting these stringent new requirements often involves demonstrating a mature security program, where services like penetration testing for cyber insurance eligibility become a critical part of the application process.
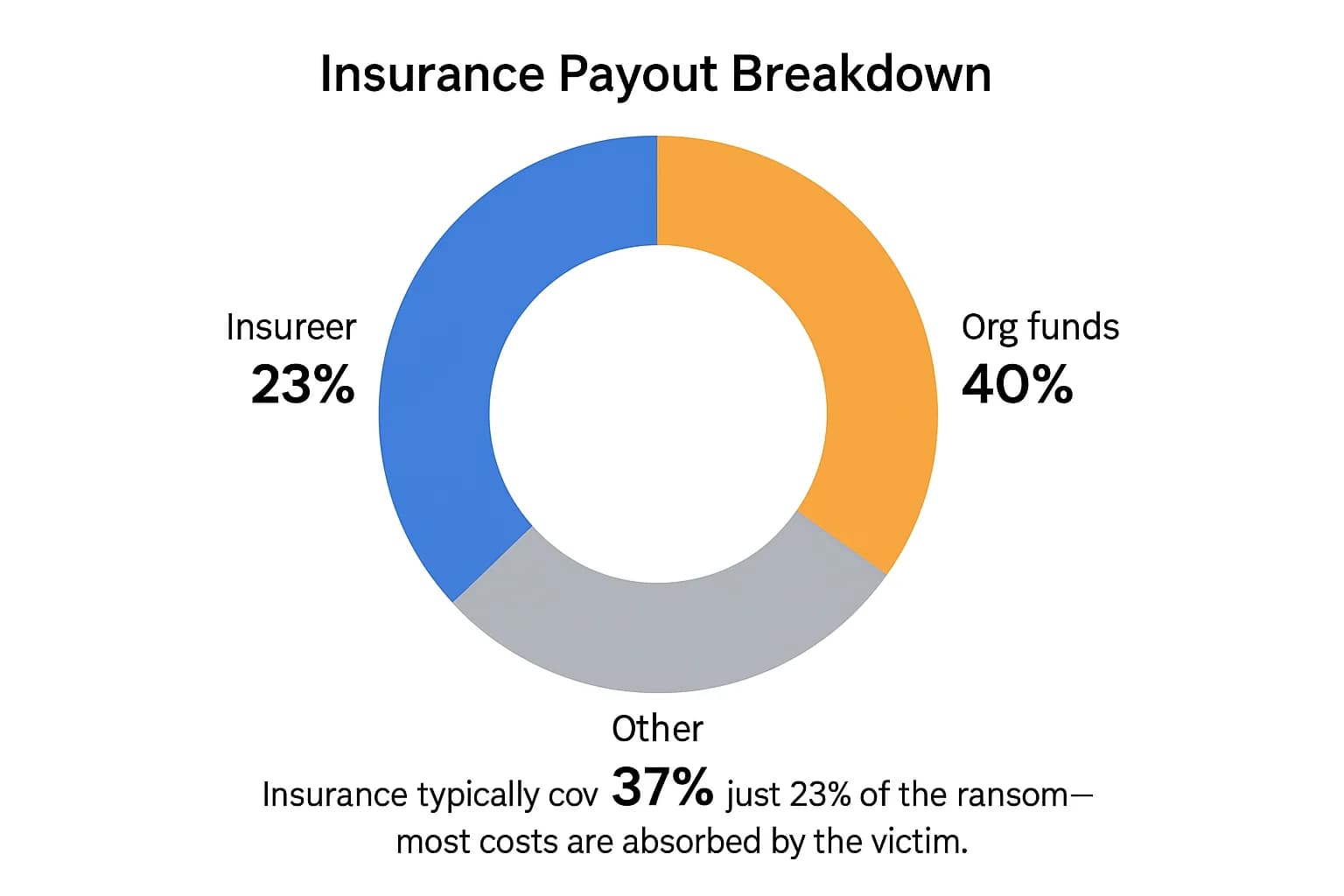
A common criticism leveled against the cyber insurance industry is that it fuels the ransomware economy by making it easy for victims to pay. The argument is that if an organization knows its ransom payment will be covered, it has less incentive to invest in strong defenses. However, the data from 2024 and 2025 paints a much more nuanced picture, suggesting that the role of insurance has become more complex and, in many ways, more beneficial to the defender.
First, it's a misconception that insurance covers 100% of the ransom. Policies come with significant retentions (deductibles), and payments are often subject to co insurance clauses. One Sophos survey found that, on average, insurance covered only 23% of the ransom cost, with the victim organization covering 40% from its own funds and the rest coming from other sources.
Second, the data shows that having insurance does not automatically lead to higher or more frequent payments. In fact, Aon, one of the world's largest insurance brokers, reported that for its clients, the average ransom payment amount declined by a staggering 77% in 2024, even as the number of ransomware claims increased. This indicates that the involvement of experienced breach coaches and negotiators, who are provided as part of the insurance policy, is leading to better outcomes for victims. These experts are skilled at managing crises and negotiating with attackers, often resulting in significantly lower payouts. Coalition, a leading cyber insurer, reported that its incident response team was able to negotiate ransom payments down by an average of 60%.
Finally, insurers are actively creating policies that incentivize good security behavior and rapid response. For example, Coalition introduced a policy feature that offers lower retentions to clients who report a funds transfer fraud incident within 72 hours, as prompt reporting dramatically increases the chances of recovering the stolen money. Rather than simply encouraging payments, the modern cyber insurance market is rewarding preparedness and resilience.
Understanding the statistics and trends is only the first step. The ultimate goal is to translate that knowledge into a robust defensive strategy that can withstand the sophisticated and multifaceted threats of 2025. Building this resilience requires a strategic approach grounded in authoritative frameworks and a practical focus on the controls that matter most.
Rather than chasing every new threat, a durable security strategy is built on established, risk based frameworks from trusted authorities like the National Institute of Standards and Technology (NIST) and CISA.
The CSRC provides a comprehensive roadmap for organizations to manage ransomware risk. It is built upon the widely adopted NIST Cybersecurity Framework (CSF) and organizes security objectives into six core functions: Govern, Identify, Protect, Detect, Respond, and Recover. By using this profile, an organization can gauge its readiness, identify gaps in its defenses, and prioritize improvements based on a strategic understanding of its unique risks, rather than reacting tactically to every new headline.
CISA's ongoing initiative provides more tactical, immediate guidance based on real world incident investigations. Across dozens of joint advisories issued with the FBI and international partners, a consistent set of critical mitigations emerges as the most effective defenses against the vast majority of ransomware attacks :

Translating these principles into action, here is a practical checklist for security leaders to harden their organizations against the specific tactics, techniques, and procedures (TTPs) observed in 2025.
The ransomware landscape of 2025 presents a stark paradox. By one measure the total amount of money flowing into criminal coffers it appears defenders are gaining ground. A 35% drop in global payments is a significant victory and a direct result of improved resilience and aggressive law enforcement action. Yet, for the organizations that still find themselves in the crosshairs, the threat has never been more severe. Skyrocketing average payouts, highly targeted social engineering, and the specter of catastrophic operational disruption from attacks on core infrastructure paint a much darker picture.
So, are we winning? The answer is a qualified "yes," but the nature of the war has changed. We are winning the battle against the commoditized, high volume ransomware of the past. We are losing ground in the new, more focused fight against elite attackers targeting our most critical and valuable enterprises.
The key takeaway from the data is this: resilience is the new metric for success. The organizations that will thrive in this environment are not those that believe they can prevent every attack, but those that have built the capacity to withstand an attack, restore operations from trusted backups, and confidently refuse to pay the ransom. This is the strategy that starves the criminal ecosystem of its profits and ultimately breaks its business model. The path forward is not about finding a single silver bullet technology, but about the disciplined, continuous process of hardening defenses, planning for failure, and fostering a culture of security that can endure the inevitable crisis.
Ready to Strengthen Your Defenses?
The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business. Explore our penetration testing services to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
1. What is the average ransomware payment in 2025?
The average ransom payment has become highly variable. Sophos reported an average payment of $2.0 million for attacks in 2024, a 500% increase from the previous year, heavily skewed by multi million dollar "big game" attacks. However, the median payment, which represents a more typical victim, has been more volatile, with Coveware reporting a Q4 2024 median of $110,890, while Sophos's 2025 report cites a median of $1 million.
2. Are companies paying ransoms more or less often now?
Significantly less often. The percentage of victims paying a ransom has been steadily declining. Incident response firm Coveware reported that the payment rate fell to an all time low of 25% in the fourth quarter of 2024. This is primarily due to organizations having better, more reliable backups and a growing distrust that attackers will honor their promises.
3. Which industry pays the most in ransoms?
The Manufacturing sector had the highest rate of payment in 2024, with 62% of victims paying, due to the intense pressure to avoid operational downtime. In terms of the amount paid, Financial Services and Education have reported some of the highest median payments, often in the multi million dollar range.
4. Is it ever worth paying the ransom?
While law enforcement agencies like the FBI strongly advise against paying, the decision remains complex. Paying does not guarantee you will get your data back; in many cases, decryption tools are faulty or the data is corrupted. Furthermore, paying a ransom marks you as a willing target and may lead to repeat attacks. However, in "double extortion" scenarios where sensitive data has been stolen, some companies pay to prevent a public leak, even if they can restore systems from backups. The best strategy is to build resilience so that paying is never your only option.
5. Does paying a ransom guarantee you get your data back?
No. Paying a ransom carries significant risk. While many victims do receive a working decryption key, there is no guarantee. In some cases, the decryption tool is faulty and corrupts the data. In double extortion scenarios, where data is stolen, there is no way to verify that the attackers have actually deleted their copy of your data after you pay. The high profile Change Healthcare attack is a prime example where a $22 million ransom was paid, but it did not prevent a second group from later claiming to have the stolen data.
6. How has law enforcement action impacted ransomware gangs?
International law enforcement actions in 2024 were highly impactful. Operations like "Cronos" against the LockBit gang and the internal collapse of the ALPHV/BlackCat group successfully dismantled the two largest RaaS franchises. This has fractured the ransomware ecosystem, creating a power vacuum and sowing distrust among criminals, making it harder for any single group to dominate the market.
7. What is the difference between double and triple extortion?
Double extortion, the current standard, involves two threats:
encrypting the victim's data and stealing the victim's data and threatening to leak it publicly. Triple extortion adds a third layer of pressure, such as launching a Distributed Denial of Service (DDoS) attack against the victim's public websites to cause further disruption, or directly contacting the victim's customers, shareholders, or patients to harass them into pressuring the victim to pay.
8. How is cyber insurance affecting ransomware payment decisions?
Cyber insurance is playing an increasingly complex role. Rather than just funding payments, insurers are now driving security improvements by mandating controls like MFA and EDR for coverage eligibility. When an attack occurs, the expert breach coaches and negotiators provided by the insurer often lead to better outcomes, including significantly lower ransom payments. Data from major brokers shows that their clients are paying less on average, suggesting the involvement of insurance is helping to manage, rather than inflate, ransom costs.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors, and this article draws on insights from those frontline experiences.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us