November 28, 2025
Last updated: November 28, 2025
A complete breakdown of the top cybersecurity vendors in 2025 across network, cloud, endpoint, and offensive security.
Mohammed Khalil

Choosing the right cybersecurity partner is more critical than ever in 2025. Cyber threats are escalating with AI powered attacks and increasingly sophisticated tactics, while businesses face stringent compliance pressures. Cybercrime damages are projected to reach $10.5 trillion annually in 2025, and the average cost of a data breach has climbed to around $4.8 million. In contrast, the cost of a thorough penetration test of a simulated cyberattack by ethical hackers might range from ~$5,000 to $50,000, illustrating how proactive testing can pay for itself many times over by preventing breaches. Moreover, new regulations like PCI DSS 4.0, GDPR, and the EU’s NIS2 directive now explicitly expect regular security testing and proof of robust defenses. The market for security providers has matured in response: organizations can choose from traditional consultancies, automated Pentest as a Service PTaaS platforms, and hybrid AI driven solutions.
This independent, research driven ranking examines the top cybersecurity companies worldwide in 2025 that offer penetration testing and related security assessment services. Our goal is to provide a neutral, expert analysis to help you compare vendors, understand their differences, and shortlist the best fit for your needs. We evaluated each provider using a rigorous methodology explained below to ensure the list remains unbiased and focused on providers that deliver true security value not just marketing hype. Whether you’re a global enterprise or a tech startup, the right partner can help you identify vulnerabilities faster, meet compliance goals, and bolster customer trust. Let’s dive into how we evaluated the companies and then the top picks.
Below we list the top ranked cybersecurity/penetration testing companies, each with a profile of key facts, strengths, weaknesses, and ideal fit. These providers represent the best in class across various categories, from all around excellence to niche specializations. Note: Company details like headquarters, size, etc., are as of 2025.
Headquarters: Newark, DE, USA serving globalFounded: 2016Company
Size: ~50–200 employees mid sized specialist
Primary Services: Penetration testing network, web/mobile app, Red Teaming, Continuous Attack Surface Monitoring
Industries Served: Tech startups, SaaS platforms, fintech and financial services, critical infrastructure, and high growth enterprises globally
Why They Stand Out: DeepStrike is a global cybersecurity firm specializing in human powered penetration testing and adversary simulations, with a mission to help organizations find and fix vulnerabilities before adversaries exploit them. Unlike many competitors, DeepStrike heavily emphasizes advanced manual testing conducted by senior ethical hackers all with robust credentials like OSCP, OSWE, CISSP. This manual first approach allows them to uncover complex vulnerabilities that automated tools might miss, a strength highlighted in client reviews noting DeepStrike’s ability to find deep, logic flaws through hands-on techniquesclutch.co. They combine this expertise with targeted coverage of modern attack surfaces cloud infrastructure, APIs, IoT, and mobile and even integrate testing into DevOps pipelines for continuous security. In short, DeepStrike offers an agile but comprehensive service that can scale from boutique style engagements to enterprise wide programs, making it our top overall pick.
Key Strengths:
Potential Limitations:
Best For: DeepStrike is best for organizations that want top tier penetration testing expertise with flexibility. Enterprise and mid market companies especially in tech, finance, and cloud native sectors that seek a high assurance test without going to a Big Four consultancy will find DeepStrike a strong partner. It’s also suitable for cloud first startups and SaaS firms that need continuous testing integrated into their dev cycle. In particular, companies that value hands-on expertise, actionable results, and a provider that can adapt to their needs will appreciate DeepStrike. DeepStrike serves both SMBs and large enterprises, but very small companies with extremely limited budgets might opt for an automated solution instead.
Headquarters: Manchester, UK global offices across Europe, North America, APAC
Founded: 1999
Company Size: 2,000+ employees large public cybersecurity firmPrimary
Services: Penetration testing applications, networks, cloud, Secure design reviews, Hardware/IoT testing, Crypto assessments, Incident response and broader cyber advisory
Industries Served: Finance and banking, Government and public sector, Healthcare, Telecom, Industrial/IoT, and other large enterprises requiring high assurance testing
Why They Stand Out: NCC Group is one of the heavyweights in cybersecurity consulting, with a worldwide presence and one of the largest dedicated pentesting teams. With over two decades in the industry, NCC has built a formidable reputation for technical excellence and comprehensive service. They offer deep manual penetration testing across virtually every domain from web/mobile apps to internal networks, cloud configurations, and even niche areas like hardware device security. NCC Group’s global team of professionals includes CREST certified testers, and the firm itself is CREST accredited and often engaged for high security projects in banking and government. They bring a rich experience and formal methodology that appeals to organizations needing absolute thoroughness and credibility.
Key Strengths:
Potential Limitations:
Best For: NCC Group is best suited for large enterprises and public sector organizations that require a top tier, globally recognized security testing partner. If you operate in a heavily regulated industry banking, healthcare, government and need exhaustive testing with all the supporting assurance certifications, compliance reports, NCC is an excellent choice. It’s also ideal if you need a provider with the capacity to handle very large scopes or multiple projects simultaneously across different regions. Companies that value an established track record and one of the most technically comprehensive teams in the world will appreciate NCC Group. Smaller companies with straightforward needs might find NCC’s size and pricing beyond their scope, in which case a smaller firm could suffice.
Headquarters: New York, USA with EU office in Amsterdam, NL
Founded: 2019
Company Size: ~50–100 employees growth stage company
Primary Services: Penetration Testing as a Service PTaaS on demand web, mobile & network pentesting; Vulnerability scanning; Cloud configuration assessments; Compliance oriented testing PCI, SOC 2, HIPAA
Industries Served: SMEs and mid market companies across tech, fintech, healthcare, and cloud services; any organizations seeking rapid pentest cycles and compliance reporting
Why They Stand Out: BreachLock is a newer entrant that has quickly gained attention for its Pentest as a Service platform. They combine automated scanning tools with manual testing by certified experts on an on demand basis. This hybrid approach, delivered through a cloud platform, allows clients to initiate tests quickly and see real time results via a dashboard. BreachLock’s services are tailored to be continuous and scalable, which is attractive for organizations that deploy frequently or need regular retesting. They also emphasize compliance ready outputs offering specific testing packages aligned with PCI DSS, SOC 2, HIPAA, and other standards softwareecured.com. In short, BreachLock stands out by making professional penetration testing more accessible and efficient, especially for smaller teams or those with frequent testing needs.
Key Strengths:
Potential Limitations:
Best For: BreachLock is best for small to mid sized businesses and agile teams that need reliable penetration testing with quick turnaround and frequent testing cycles. It’s ideal for DevSecOps oriented organizations e.g. SaaS companies pushing updates who want to integrate pentesting into each release. Companies that must meet compliance requirements on a budget like startups prepping for SOC 2 or healthcare firms under HIPAA will find BreachLock’s ready to go compliance testing very useful. If you value a convenient platform experience and the ability to scale testing as needed, BreachLock is a great choice. Large enterprises can also use BreachLock for supplemental testing especially for quick re-tests or incremental checks, though for very complex, high security scenarios, they might pair it with a more specialized firm.
Headquarters: Westminster, CO, USA offices across the US and UK
Founded: 2001
Company Size: ~1,000+ employees mid large size firm
Primary Services: Penetration testing app, network, cloud, Red Team operations, Cloud security assessments, Compliance advisory PCI, FedRAMP, ISO 27001, Security consulting and 3PAO assessments for FedRAMP
Industries Served: U.S. federal agencies and contractors, Cloud service providers SaaS/IaaS companies, Finance & fintech, Healthcare, Retail, and other regulated enterprises requiring offensive security tied to compliance
Why They Stand Out: Coalfire is a leading cybersecurity firm known for bridging the gap between offensive security testing and compliance requirements. Their Coalfire Labs division conducts manual pentesting and red teaming, but always with an eye on helping clients meet or exceed regulatory and audit standards. In fact, Coalfire is one of the few penetration testing providers that is also a certified FedRAMP Third Party Assessment Organization 3PAO for cloud security, underscoring their credibility in high stakes compliance scenarios. They have extensive experience in industries like finance, healthcare, and government where testing isn’t just about finding vulnerabilities but also about satisfying examiners. Coalfire stands out for its ability to deliver high quality pentests that align with frameworks essentially offering compliance aligned offensive security. They help organizations reduce real risk while also accelerating audit and certification milestones, a dual value not all providers can offer.
Key Strengths:
Potential Limitations:
Best For: Coalfire is an excellent choice for organizations that are highly compliance driven but also want robust security testing. If you are a cloud service provider aiming for FedRAMP authorization, a healthcare company under HIPAA security rules, a bank dealing with FDIC/GLBA, or any enterprise that must check certain regulatory boxes while truly improving security, Coalfire is tailored for you. It’s also a top pick for U.S. federal contractors and agencies themselves, given its experience in the public sector. Large enterprises undergoing digital transformation migrating to cloud, etc. will benefit from Coalfire’s dual perspective on secure architecture and compliance. In summary, choose Coalfire if you need a trusted, experienced partner to navigate both security threats and compliance audits hand in hand.
Headquarters: Phoenix, AZ, USA operations across North America, Europe, Asia Pacific
Founded: 2005
Company Size: ~400+ employees offensive security specialists
Primary Services: Advanced penetration testing apps, networks, cloud, Red Team and Adversary Simulation, Continuous Attack Surface Management Cast/Cosmos platform, Application code reviews, Security consulting
Industries Served: Fortune 500 and large enterprises across tech, financial services, media, retail, healthcare, critical infrastructure particularly those with complex, dynamic IT environments
Why They Stand Out: Bishop Fox is widely regarded as a global leader in offensive security, known for its elite team and cutting edge techniques. Unlike some large firms, Bishop Fox’s sole focus is on offensive and adversarial testing; this singular focus has allowed them to build a deep bench of talent; many are top researchers and former DEF CON Black Badge winners and a reputation for tackling the hardest challenges. They work with major enterprises to simulate sophisticated attacks, often uncovering issues that others miss. Additionally, Bishop Fox offers a continuous attack surface management platform formerly called Cosmos that combines automation with human validation to monitor clients’ external exposures on an ongoing basis. This blend of project based red teaming and continuous testing makes them a formidable partner for organizations that want constant vigilance and top tier expertise. Clients with high stakes environments often choose Bishop Fox for their most critical tests.
Key Strengths:
Potential Limitations:
Best For: Bishop Fox is the top choice for large enterprises and organizations with advanced security programs that want to truly challenge themselves. If you have a mature defense and Blue Team and you want a no holds barred test of your security short of a real incident, Bishop Fox will deliver that. They are ideal for tech companies, financial institutions, and others who consider security a competitive priority and are willing to invest in the best. Companies undergoing major events like M&A where hidden vulnerabilities are a risk, or those in the spotlight for attackers would benefit from Bishop Fox’s continuous monitoring and testing to stay ahead of threats. In summary, for organizations where only the most elite offensive expertise will suffice, Bishop Fox is a clear leader.
| Company | Specialization | Best For | Region | Compliance | Ideal Org Size |
|---|---|---|---|---|---|
| DeepStrike | Manual Pentesting, Cloud/API Security | Flexible, all around security partner for tech focused firms | Global HQ USA | Reports align to SOC 2, ISO 27001, PCI DSS | Startups to Large Enterprise |
| NCC Group | Comprehensive Consulting Apps, Network, Hardware | Large enterprises needing broad, deep expertise | Global HQ UK | CREST accredited; PCI DSS & global standards | Large Enterprise |
| BreachLock | PTaaS Automated + Manual Pentesting | Quick, affordable testing for frequent releases SMBs | Global USA/NL | PCI, HIPAA, SOC 2 test packages | Small to Mid sized |
| Coalfire | Compliance aligned Pentesting & Red Team | Regulated orgs needing security + audit prep | Global HQ UK | FedRAMP 3PAO; PCI QSA; ISO 27001 advisory | Mid size to Enterprise |
| Bishop Fox | Elite Red Team & Continuous Attack Surface | Advanced offensive security for high stakes enterprise | Global USA/NL | CREST certified; helps meet PCI, NIST, etc. reports for audit | Large Enterprise |
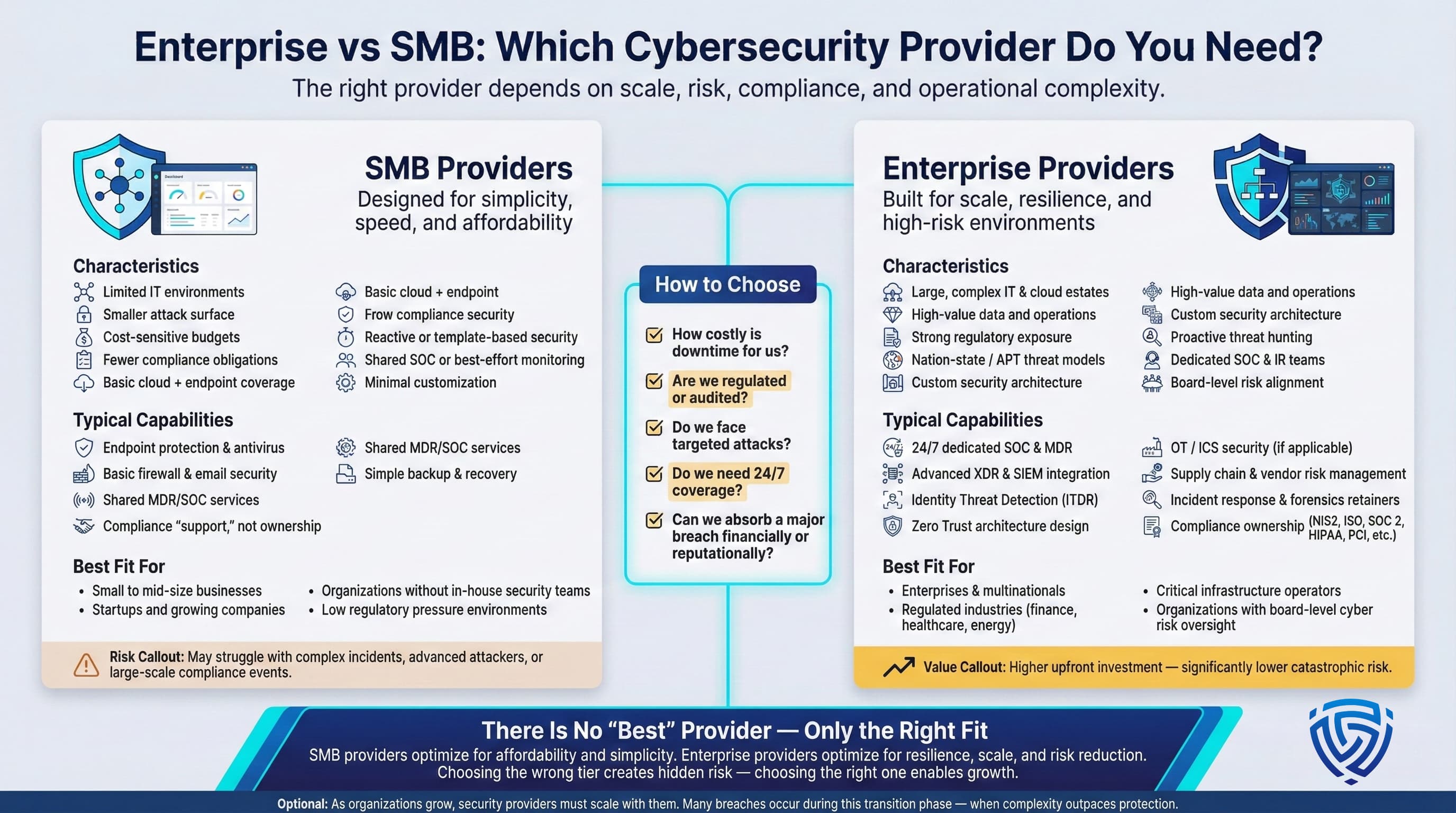
When deciding between a large scale provider and a boutique firm, consider your organization’s size, culture, and security maturity. Bigger isn’t always better and vice versa it truly depends on fit:

Finding the best cybersecurity/pentesting providers required a comprehensive evaluation. We developed a transparent methodology to rank the top companies, focusing on criteria that matter most to buyers seeking effective and trustworthy services. Our evaluation factors included:
Using these criteria, we identified the leading companies that met our high standards. Next, we provide a brief guide on choosing the right type of provider for your needs, and then we present the top cybersecurity companies Global in 2025, including why each stands out, key strengths and limitations, and ideal use cases.
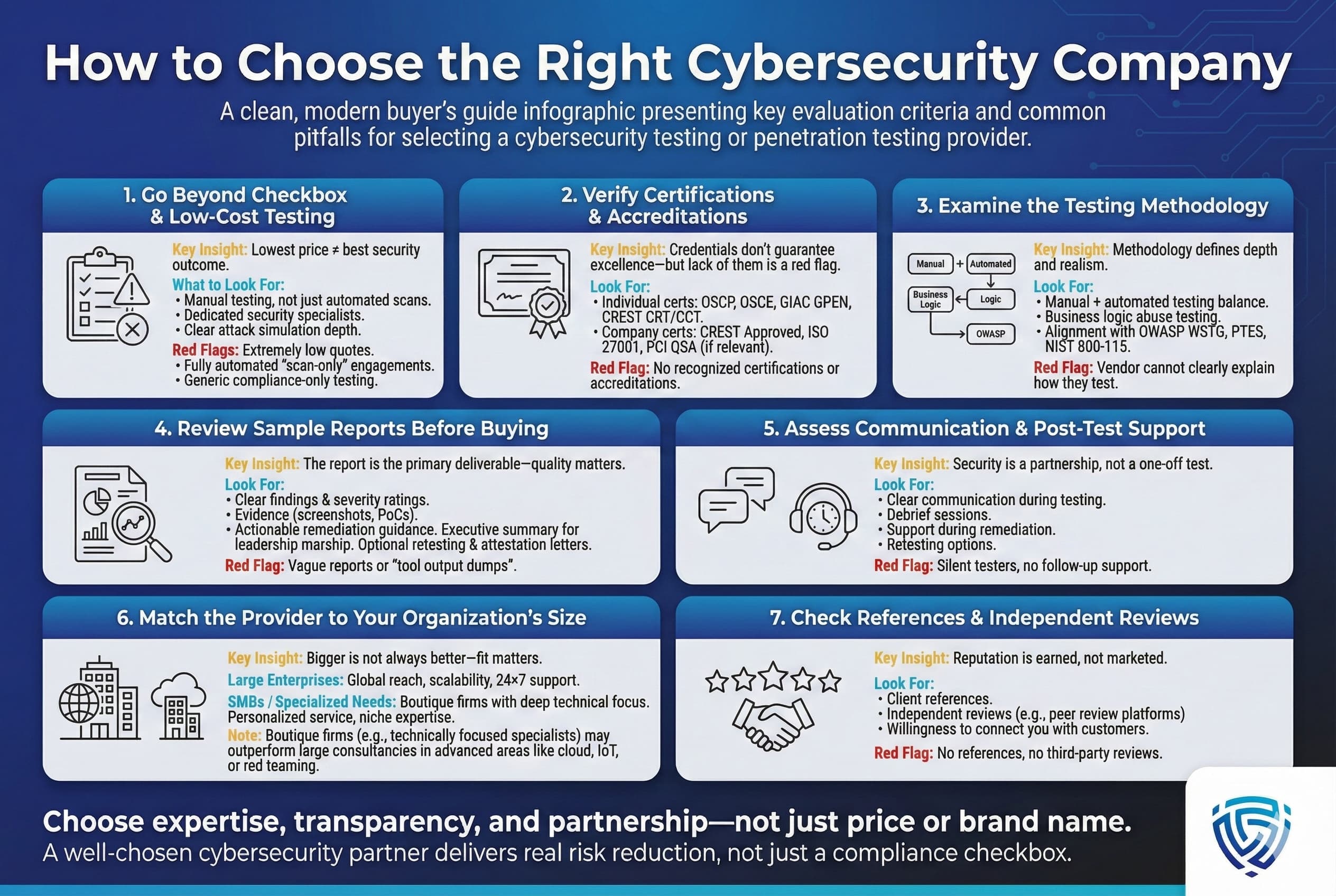
Selecting a security testing provider is a critical decision. Here are some key considerations and common pitfalls to help you make an informed choice:
In summary, don’t be swayed by flashy marketing alone. Take a balanced look at each provider’s real qualifications and fit for your use case. The next section applies this lens to highlight the top cybersecurity companies Global in 2025 for penetration testing and related services.
In summary, assess your own context. If you have a small team and need more guidance, a big provider with lots of support might hold your hand through the process. If you have an advanced security team and just need the best hackers to pit them against, a boutique or offensive specialist is ideal. The goal is to find a partner that matches your organization’s pace, technical depth, and business goals.
The cost of penetration testing varies widely based on scope, complexity, and provider. A basic one time test for a small web application might be a few thousand dollars, whereas a full scope enterprise network and application test could be tens of thousands. Generally, reputable firms charge by the effort and expertise required, often in the range of $200–$300 per hour or $1,600–$2,500 per day per tester in the US. As a rough benchmark, many small to mid size pentests fall in the $10,000–$50,000 range. Remember that higher cost usually reflects more thorough manual testing by experienced professionals. Be cautious of quotes that seem too low; as experts warn, extremely low priced offers might indicate mostly automated scanning instead of a real in depth pentest. Also consider the value: a quality pentest that finds critical issues can save you millions by preventing breaches. In fact, one study noted a genuine pentest costing ~$20k can mitigate breach risks averaging $4–5M, yielding an ROI of over 12,000% if those vulnerabilities are fixed. Always scope out the work with the provider and most will offer a custom quote once they understand your environment.
Both matter, but in different ways. Strong certifications on a provider’s team OSCP, OSCE, CREST, GIAC, etc. are a good indicator of their expertise and commitment. Certifications ensure the testers have proven baseline skills and up to date knowledge essentially a proxy for quality. However, certifications alone are not everything; there are excellent testers without certs and conversely certified individuals who might lack creativity. What’s most important is the provider’s methodology and the skill of their people in practice. Tools both commercial and custom are indeed important for efficiency and coverage, but tools are widely available. It's the human using the tool that finds the serious holes. A balanced perspective: certifications demonstrate dedication and knowledge, and you should expect top firms to have them, but also look for evidence of real world skill like published research, open source tools they’ve developed, or client testimonials of their work. In short, prioritize providers with excellent people. Those people will choose and operate the right tools. As one guide put it, the best measure of a pen tester is skill and dedication, and certifications are one way to verify that, but practical experience and ingenuity often shine through in actual engagements.
The duration of a pentest depends on its scope and depth. A test of a single simple web application might be done in 1 week, whereas a comprehensive test of a large corporate network, multiple apps, and cloud infrastructure could span 4–6 weeks. In general, most penetration testing engagements last about 2–4 weeks of active testing, plus additional time for planning and reporting. For example, a moderately complex web application often gets 1-2 weeks of testing time. Add a week or two for initial scoping and final report writing, and many projects from kickoff to report delivery are in the 4-6 week total timeframe. Larger or more complex engagements can certainly go longer multi month red team operations, for instance. It’s worth noting that some providers offer continuous testing or retainer models where testing is broken into smaller pieces over a longer period e.g. test a bit each quarter. Always clarify the timeline in the proposal stage. If you have a deadline, say, needing results before a compliance audit, communicate that upfront. The average case though: 2 3 weeks of testing effort for a typical medium scope pentest, but plan for ~4 weeks including coordination and reporting.
A professional penetration test should produce a detailed report documenting the findings. At minimum, this typically includes: an Executive Summary high level overview of risks and overall security posture, in business terms, a Technical Findings section for each vulnerability with descriptions, severity rating, impact, evidence such as screenshots or command output, and remediation recommendations, and often an Appendix with details like raw scan results or tool output if relevant. Many providers will also include a Priority Matrix or Ranking of issues so you know what to fix first. The best reports turn the findings into a clear action plan rather than just listing bug. Additionally, some deliverables to look for: Remediation Guidance good reports have not just the problem but how to fix it, possibly with reference links. Some vendors provide a slide deck for executive debriefs, or a certificate/letter of attestation that you can show to customers or auditors proving a pentest was done common for SOC 2 or ISO compliance. It’s also important to clarify if re testing is included many providers will do a follow up test on the fixed issues to confirm they’re resolved, and update the report. As one checklist advises, confirm whether you’ll get a summary report or certificate for stakeholders, and if post test support like answering developers’ questions or a re test is included. In summary: expect a thorough written report and ask for a sample to ensure the format and depth meet your needs.
At minimum, annually. Most standards, PCI DSS, etc. and industry best practices suggest a full scope pentest at least once per year. In fact, 43% of organizations test one to two times a year according to a 2024 industry survey, making it the most common cadence. However, there are many cases where more frequent testing is warranted. If your environment changes often say you release new software features monthly you might do targeted pentests quarterly or with each major release. Some high security organizations even engage in continuous testing. 17% of companies in that survey do pen tests daily or weekly on some scope. Compliance requirements can also drive frequency: for example, PCI DSS requires annual testing and after any significant change to the cardholder data environment. Similarly, if you had a security incident or major system upgrade, a pentest afterward is wise. Risk level is a key factor a bank or healthcare provider might opt for bi annual or quarterly tests due to handling sensitive data. Smaller businesses with static infrastructure might be fine with annual testing. In summary: annual testing is the baseline must, but consider semi-annual or quarterly tests if you are in a high risk industry or rapidly changing environment. And remember, even with annual big tests, employing continuous vulnerability scanning or smaller interim pentests can help cover the 11 months between tests. It’s about balancing resources with risk but err on the side of more frequent if you can, given the threat landscape.
A penetration test is typically a goal oriented but scoped security assessment where the testers look for as many vulnerabilities as possible in the given scope e.g. a set of IPs or an application and report them. It’s often done with the knowledge and consent of the IT team, and within a fixed time window. A red team exercise, on the other hand, is more like a full blown simulation of a real attack. Red teamers have a broader goal e.g. access sensitive data or achieve domain admin in the network and can use any methods to get there, often over a longer period, while evading detection. The key differences: Scope and Visibility. Red team engagements are usually covert; the organization’s defenders may not know it’s happening and can include social engineering, physical breaches, etc., not just technical exploits. Penetration tests are more overt and focused e.g. just test the web app for flaws. Another way to put it: pentesting finds as many vulnerabilities as possible in a scope, whereas red teaming tests the organization’s detection and response by attempting to achieve a specific impact without being caught. Red teaming is typically for companies that have already done multiple pentests and want to take it to the next level essentially a way to test the testers and see how well your security team and controls fare against a skilled adversary. Not every company needs a red team exercise; if you’re still finding lots of basic issues in pentests, tackle those first. But if your perimeter seems strong and you want to simulate an advanced threat APT, a red team will provide invaluable insight. In practice, many providers offer both; you might start with pentests to shore up known weaknesses, then use a red team annually to probe deeper and exercise your defense in depth. They are complementary, with pentesting being more targeted and find and fix, and red teaming being more holistic and resilience testing.
Penetration Testing as a Service PTaaS is a modern delivery model for pentesting that leverages a software platform to provide ongoing, on demand testing. Instead of the traditional approach of a one off test and PDF report, PTaaS platforms offered by companies like Cobalt, BreachLock, HackerOne, etc. give clients access to a dashboard where they can request tests, see live results, collaborate with testers, and even retest fixes in real time. Essentially, PTaaS turns pentesting into a more agile, continuous service rather than a point in time project. The advantages are speed and integration. For instance, you can schedule a test for every new app release and get results quickly, or integrate findings into your ticketing system instantly. Some PTaaS solutions also incorporate automated scanning for quick feedback, supplemented by human testers for deeper validation. Do you need it? If your organization has embraced DevOps/DevSecOps and pushes updates frequently, PTaaS can be a great way to ensure security keeps up with development. It’s also useful for companies that might not have a lot of internal security resources, as the PTaaS provider’s platform can serve as a central hub for managing vulnerabilities. However, PTaaS is not a magic bullet; the quality still depends on the experts behind the scenes. Also, certain types of tests like extensive red teaming or very custom scenarios might not fit neatly into a platform model and are better handled as bespoke engagements. Many organizations use a hybrid approach: use PTaaS for continuous scanning and quick tests on incremental changes, and still do an annual or semi annual full scope test possibly with the same provider or a specialist firm for a comprehensive security check. In summary, PTaaS is about making pentesting more continuous and convenient. It can greatly benefit fast moving companies, but you should ensure the service includes skilled human testers and not just automated scans. If you’re unsure, you could pilot a PTaaS on a small app to see how it integrates into your workflow.
In closing, choosing a cybersecurity partner for penetration testing is a significant decision, but arming yourself with the right knowledge makes it much easier. We have reviewed the top global companies in this space for 2025, each with their own strengths: from DeepStrike’s flexible, expert driven approach, to giants like NCC Group for broad enterprise needs, and niche leaders like Bishop Fox for advanced adversary simulations. Our rankings and analysis have been conducted with neutrality and an emphasis on real capabilities. We have no sales agenda, only the goal of helping you make an informed choice.
As you consider these options, keep in mind your organization’s unique requirements. Evaluate the methodology and cultural fit as much as the service offerings. A trustworthy provider should be transparent, willing to answer tough questions, and focused on your security outcomes rather than just selling services. Also remember that no list is one size fits all; all the companies here are excellent in their domains, but the best for you is the one that fits your context and objectives the most closely.
Cyber threats will continue to evolve, and so will the security testing industry with trends like AI driven testing and continuous services coming to the fore. However, the core need remains the same: independent, expert validation of your security. By selecting a provider that embodies expertise, integrity, and alignment with your needs, you are taking a confident step toward a more secure future for your organization. We hope this guide has equipped you with insights to proceed on that journey with assurance. Here’s to making a well informed, effective, and neutral decision that strengthens your cybersecurity posture for the days ahead.
About the Author
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us