October 31, 2025
Updated: October 31, 2025
FISMA mandates annual penetration testing under NIST SP 800-53 CA-8. Learn how to scope, execute, and document compliant pentests that secure federal systems and meet audit expectations.
Mohammed Khalil


FISMA penetration testing is the mandatory security testing of U.S. federal systems under the Federal Information Security Modernization Act FISMA. In practice, it means hiring skilled pentesters to simulate real attacks on all in scope assets networks, applications, cloud services, etc.. This goes beyond automated scanning, aiming to exploit vulnerabilities in depth. The results feed directly into compliance each finding is documented against NIST controls in the system’s Authority to Operate package. Need a pentesting refresher? See our What is Penetration Testing? overview.
This matters now because federal cyber threats are on the rise. In FY2023, agencies reported 11 major incidents including breaches and ransomware. Penetration testing helps catch gaps before attackers exploit them. Scans alone can’t prove exploitability, whereas pentests demonstrate real attack paths. For example, a scan might flag an open port or missing patch, but only a pentest will attempt to exploit it and show if it truly leads to a compromise. And by law, FISMA requires it: for instance, GSA policy mandates annual ATO pentests for all FISMA designated High Value Assets, and FedRAMP for cloud services requires accredited 3PAOs to perform yearly pentests on Moderate/High systems. In short, regulatory compliance and good security hygiene demand thorough pentesting now. In summary, FISMA penetration testing is essential to verify your security posture beyond basic scanning.

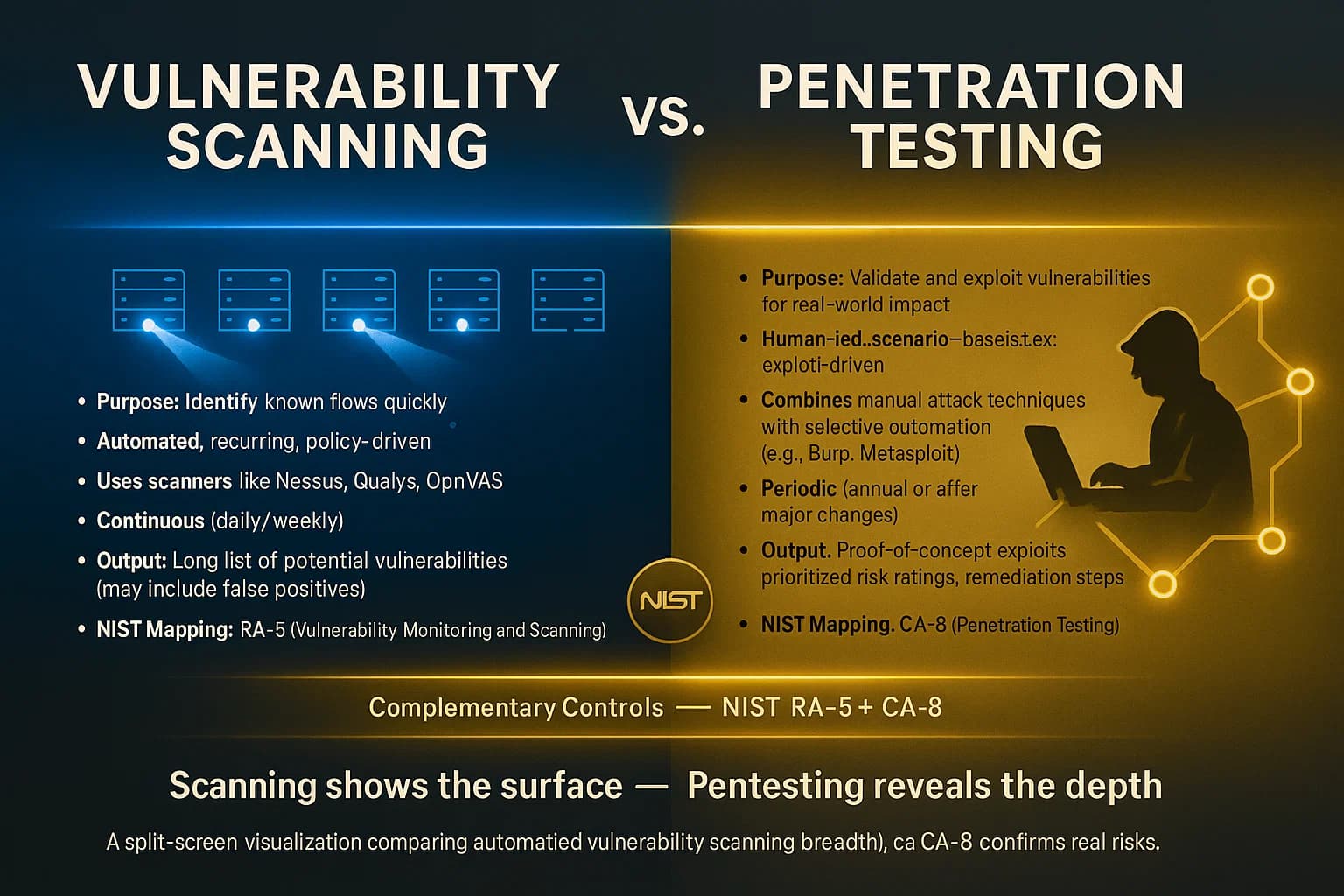
Penetration tests and vulnerability scans complement each other under FISMA compliance. Scans NIST control RA 5 find known flaws quickly, whereas pentests NIST CA 8 validate which flaws can actually be chained into a breach. Consider this: a scan may list dozens of missing patches or open ports, but a pentester will try exploiting them to see if they truly give an attacker a foothold. The table below highlights key differences:
| Aspect | Vulnerability Scan Automated | Penetration Test Manual |
|---|---|---|
| Purpose | Identify known flaws across systems meets NIST RA 5 | Exploit vulnerabilities to prove actual risk required by NIST CA 8 |
| Method | Automated tools scans, scripts | Manual techniques simulating real attackers |
| Coverage | Broad but shallow all hosts/services | Focused depth critical systems/apps with full exploit attempts |
| Frequency | Continuous e.g. weekly/daily monitoring | Periodic e.g. annual for HVAs |
| Outcome | Reports of potential issues many false positives | Proof of concept exploits and prioritized findings with remediation guidance |
Only pentesting confirms which issues an attacker can actually exploit. Scans may list potential vulnerabilities, but pentesters prove which ones pose real risk by chaining them.
Continuous Testing PTaaS Some modern platforms offer Penetration Testing as a Service PTaaS for ongoing automated tests. These can catch issues in real time, but remember FISMA compliance still requires formal, scheduled pentests with full reports.
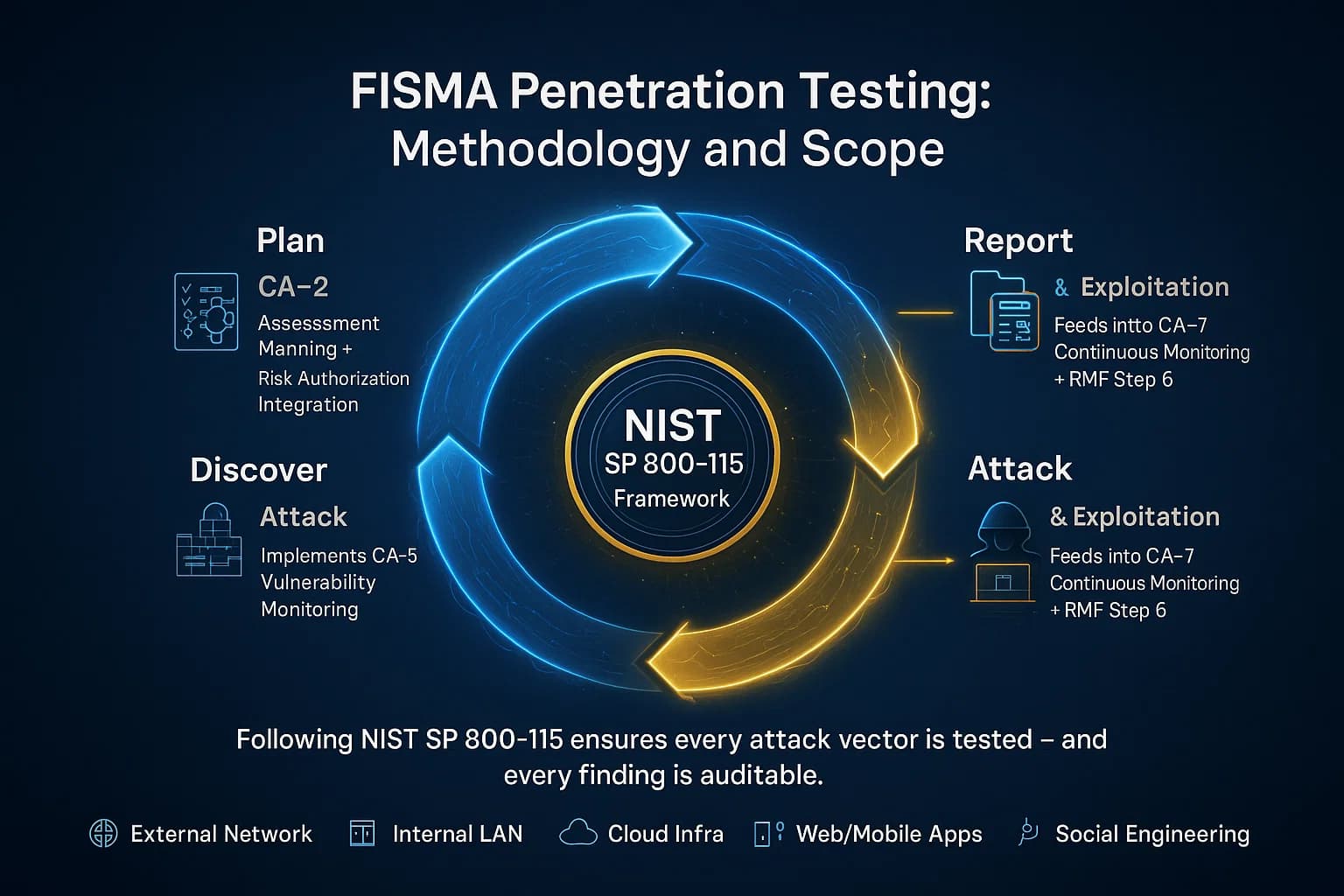
Scoping a FISMA pentest means testing both external and internal assets: internet facing systems, on premises networks, cloud environments, web/mobile applications, authentication systems, and even social engineering or physical attempts if allowed see the difference between internal and external penetration tests. You can choose a black box approach no insider info or white box full documentation often testers use a grey box mix. Some pentests become full red team exercises sustained adversary simulations to rigorously test an organization’s defenses.
Pentests generally follow NIST SP 800 115’s four phase process:
This structured approach ensures thorough coverage. For example, if a tester gains low level access, they loop back into Discovery with those new credentials to find further vulnerabilities.
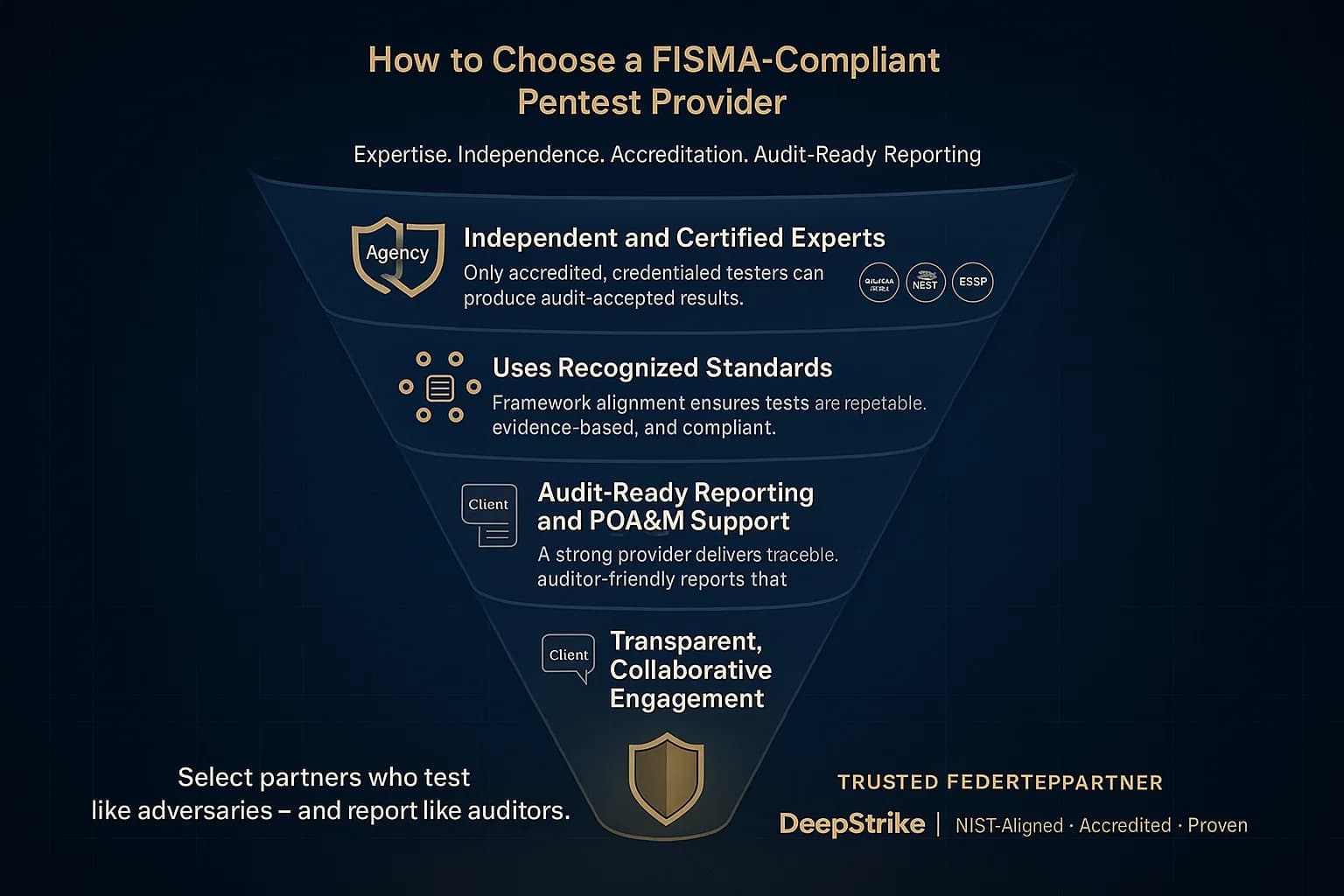
Not just any test will do. FISMA requires independent, qualified testers. Key criteria:
Penetration tests require skilled labor, so budget accordingly. Think of it as cyber insurance: the cost of expert testing is small compared to a major breach.
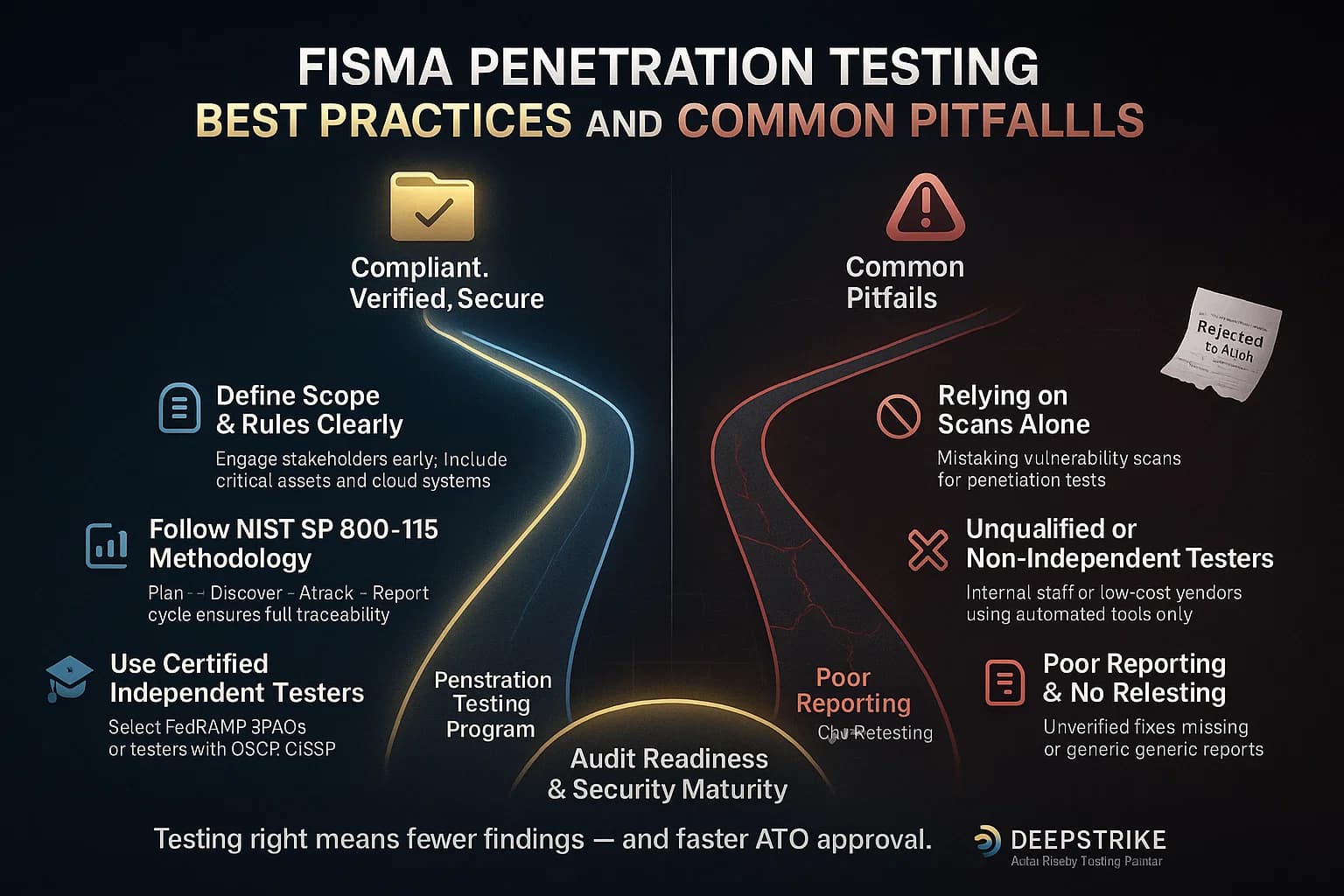
From experience, these guidelines help ensure effective FISMA pentesting:
Common mistakes include skipping scoping, missing critical systems and thinking automated tools alone satisfy FISMA. Remember: automated scans identify potential issues, but penetration tests confirm exploitable issues. In real assessments, testers often uncover critical chains of exploits that scanners missed.
FISMA penetration testing isn’t just a compliance checkbox, it's a proactive defense measure. By thoroughly testing your federal systems against NIST’s CA 8 control and following established methodologies, you reduce the risk of future breaches. The latest FISMA reports and FedRAMP rules make it clear regular, well scoped pentests by qualified experts are mandatory.
Ready to Strengthen Your Defenses? DeepStrike’s team is here to help. We specialize in FISMA/FedRAMP aligned penetration testing and can guide you through scoping, execution, and remediation.

Explore our penetration testing services to see how we can uncover vulnerabilities before attackers do. Drop us a line we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security. With certifications such as CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies. Mohammed focuses on cloud security, application vulnerabilities, and adversary emulation, helping clients in finance, healthcare, and technology sectors build resilient defenses.
It means performing penetration tests specifically to comply with FISMA/NIST requirements. Federal agencies must simulate real attacks on in scope systems to validate security controls.
Regulations require at least annual tests for critical systems. For example, GSA policy mandates yearly ATO pentests for FISMA High Value Assets. FedRAMP Moderate/High cloud services also require annual 3PAO pentests.
No. Automated vulnerability scans NIST RA 5 are helpful, but FISMA’s CA 8 control specifically requires manual penetration tests. Scanners may find issues, but only pentests prove those issues can be exploited in sequence.
Qualified third party security professionals or accredited 3PAOs should conduct the tests. NIST even recommends independent testers to avoid conflicts. Look for providers experienced with federal standards and certifications.
FISMA covers on premises agency systems, while FedRAMP applies to cloud services used by agencies. FedRAMP’s pentesting requirements annual tests by accredited assessors are essentially FISMA/NIST rules for the cloud.
Agencies document findings in the ATO package and track them in the Plan of Action & Milestones POA&M. High risk issues are remediated quickly and re-tested. In this way, the pentest drives continuous improvement of the security posture.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us