August 14, 2025
Updated: August 14, 2025
Meet the four ransomware gangs dominating 2025 Cl0p, Qilin, Akira, and RansomHub and learn how to stop their attacks.
Mohammed Khalil

How We Gather This Data: This report is based on threat intelligence from our incident response engagements, analysis of dark web leak sites, and public advisories from cybersecurity authorities including CISA, the FBI, and NIST. We also incorporate data from leading threat research firms like CrowdStrike, Palo Alto Networks, and Check Point to provide a comprehensive and verifiable analysis. All data is current as of the last updated date.
If you're trying to understand how ransomware groups operate in 2025, you're in the right place. These aren't lone hackers anymore; they are organized, professional, and run like criminal enterprises.
Ransomware has evolved from a simple malware threat into a systemic risk capable of shutting down hospitals, halting national supply chains, and exposing the data of millions.
The threat is accelerating. The first quarter of 2025 saw a staggering 126% surge in reported ransomware incidents compared to the previous year, according to a report from Check Point.
This report breaks down the modern ransomware ecosystem. We'll cover the business model that fuels these gangs, profile the key players, detail their attack methods, and give you an actionable guide to building a resilient defense.
A ransomware group is a team of cybercriminals that uses malware to encrypt your files and demand payment to restore access. But today, they are much more than that. They are structured criminal organizations focused on one thing: extortion.
Their primary tactic is a devastating one two punch. First, they use powerful encryption to make your systems and data completely unusable. Second, they steal a copy of your most sensitive data before the encryption and threaten to leak it on the dark web if you don't pay.
This is double extortion, and it puts victims in an impossible position: a simultaneous business shutdown and a public data breach crisis.
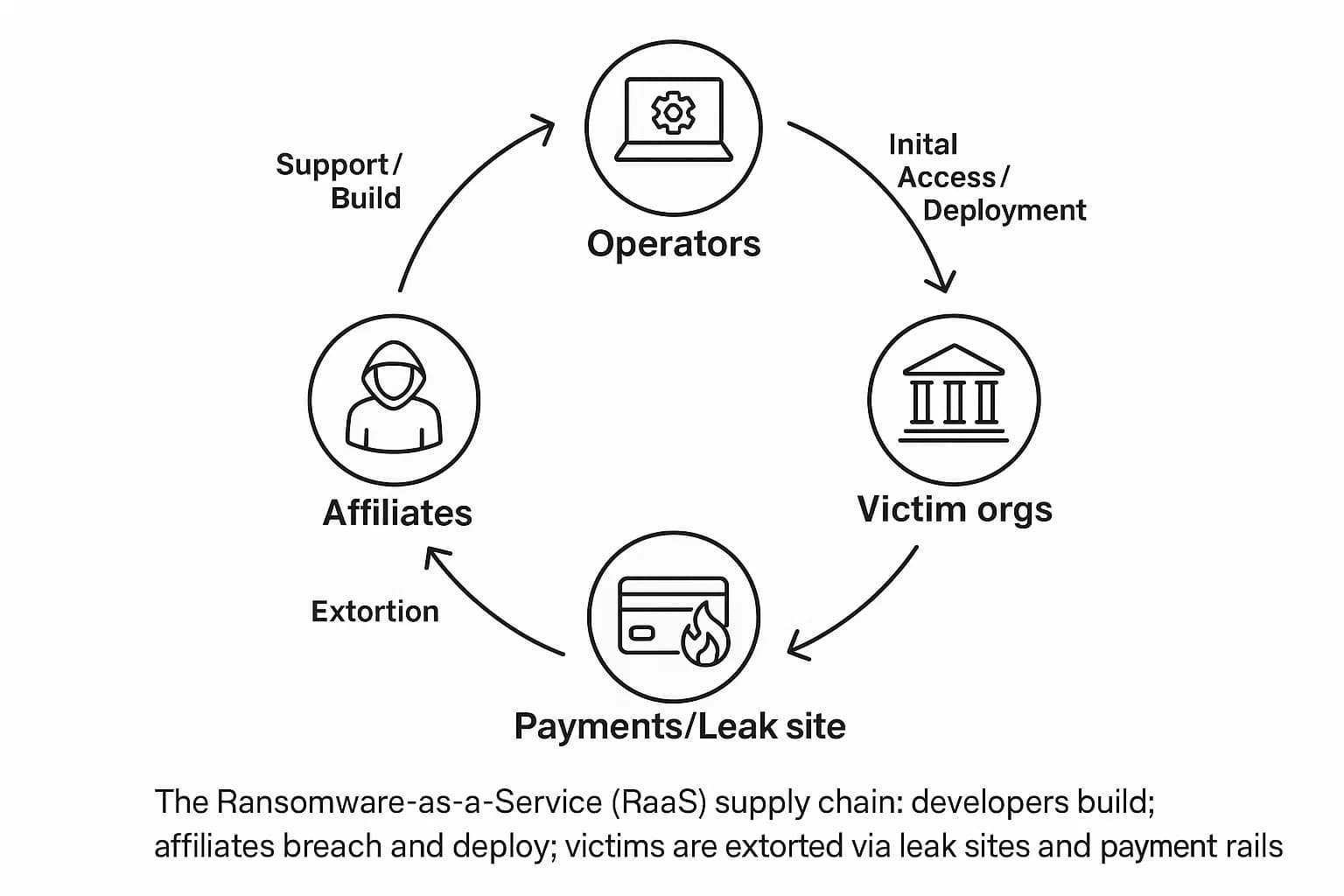
The engine driving this criminal industry is the Ransomware as a Service (RaaS) model. It mirrors the legitimate Software as a Service (SaaS) world, allowing skilled developers to lease their malicious tools to other criminals, known as affiliates.
The RaaS ecosystem has two main roles:
RaaS Pricing Models 2025
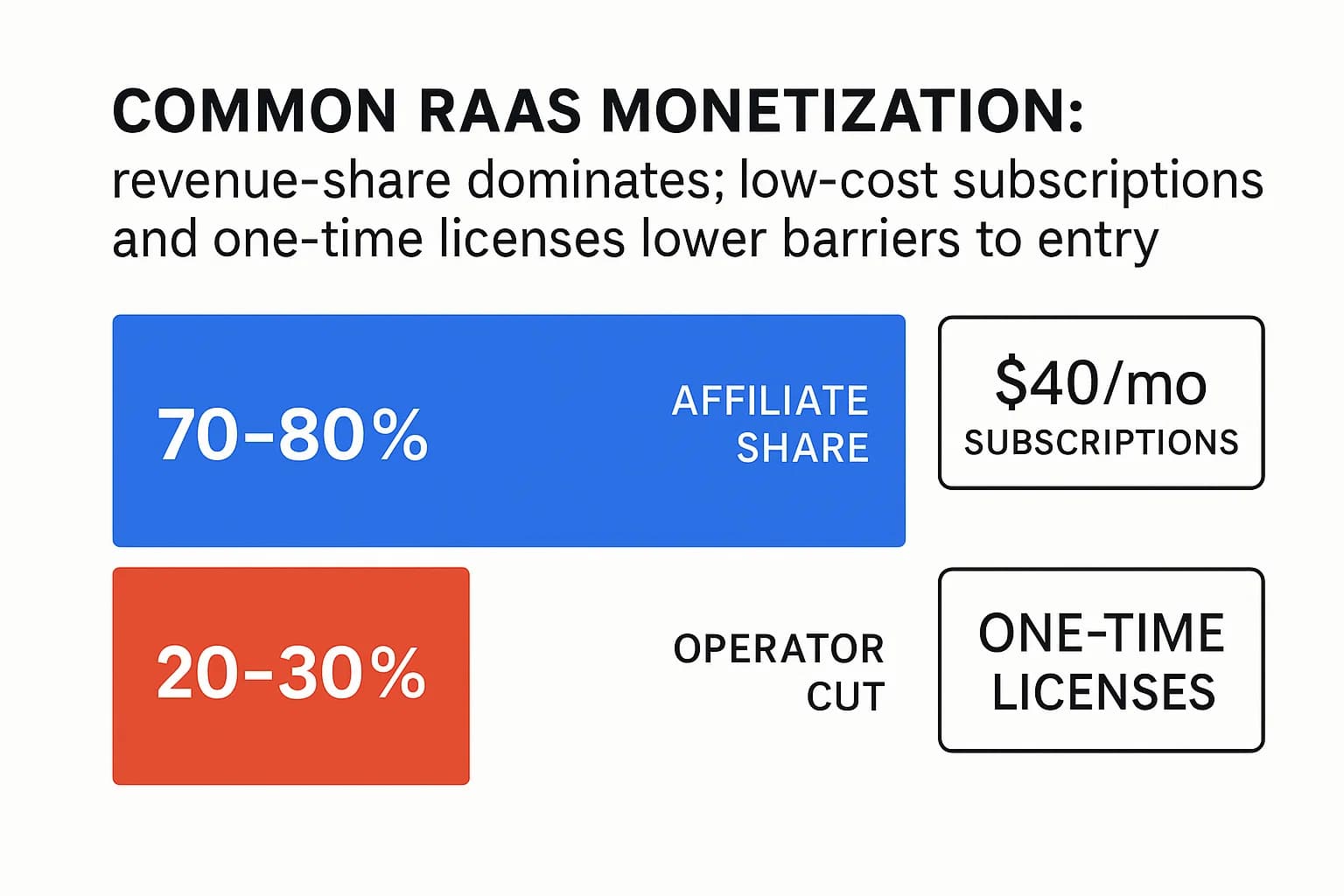
RaaS pricing models are designed for accessibility and profit. The most common is a profit sharing model, where the affiliate keeps 70-80% of the ransom and the operator takes a 20-30% cut. Other models include monthly subscriptions sometimes as low as $40 or one time license fees.
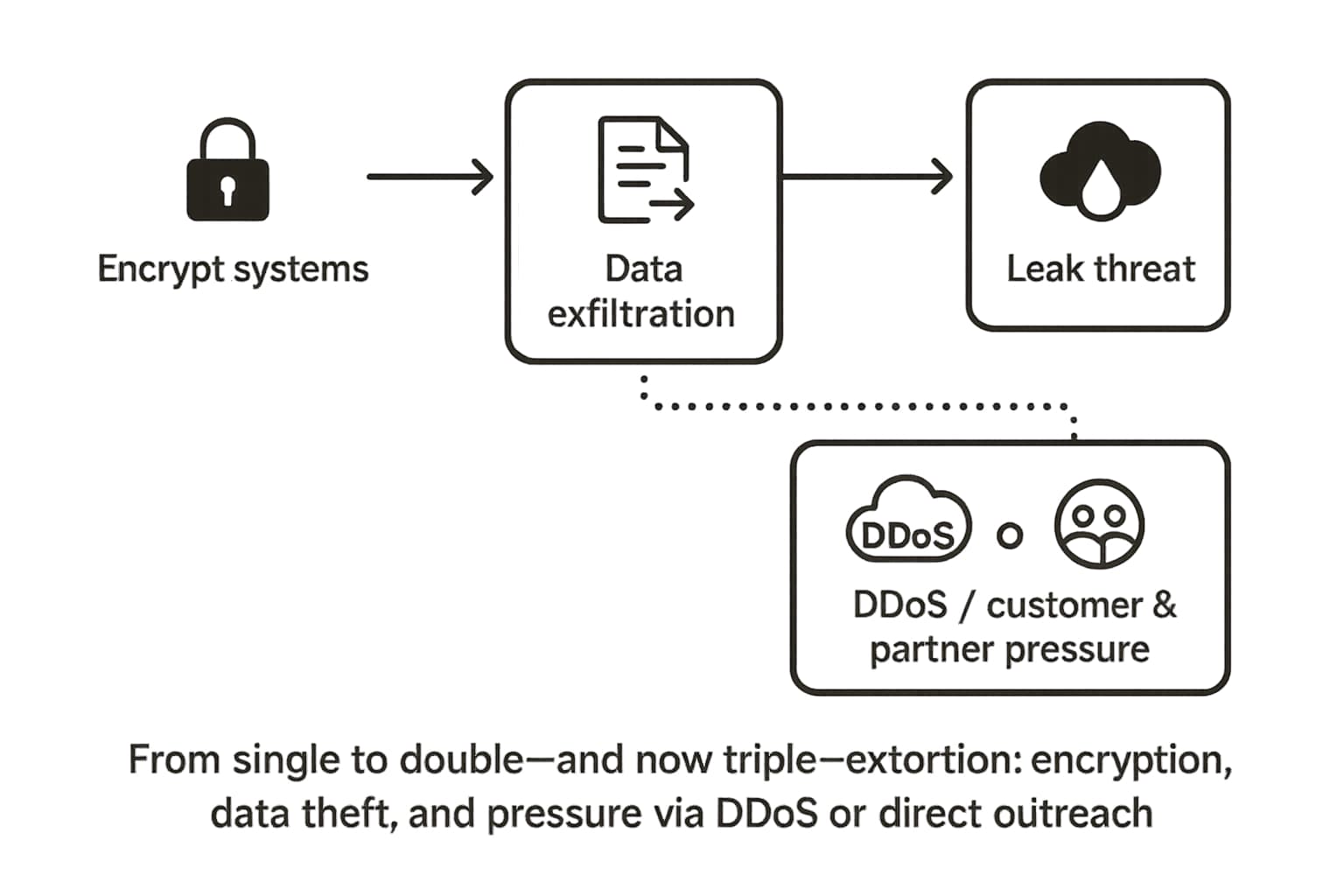
Initially, ransomware was simple: attackers encrypted files and demanded a ransom for the key. But as organizations got better at making backups, they could often recover without paying.
In response, the Maze ransomware group pioneered double extortion around 2019. This tactic adds a second layer of leverage:
Even if your business can restore from backups, you now face regulatory fines, reputational damage, and legal action from the data leak. Some groups have even escalated to
triple extortion, adding DDoS attacks or directly contacting a victim's customers and partners to maximize pressure.
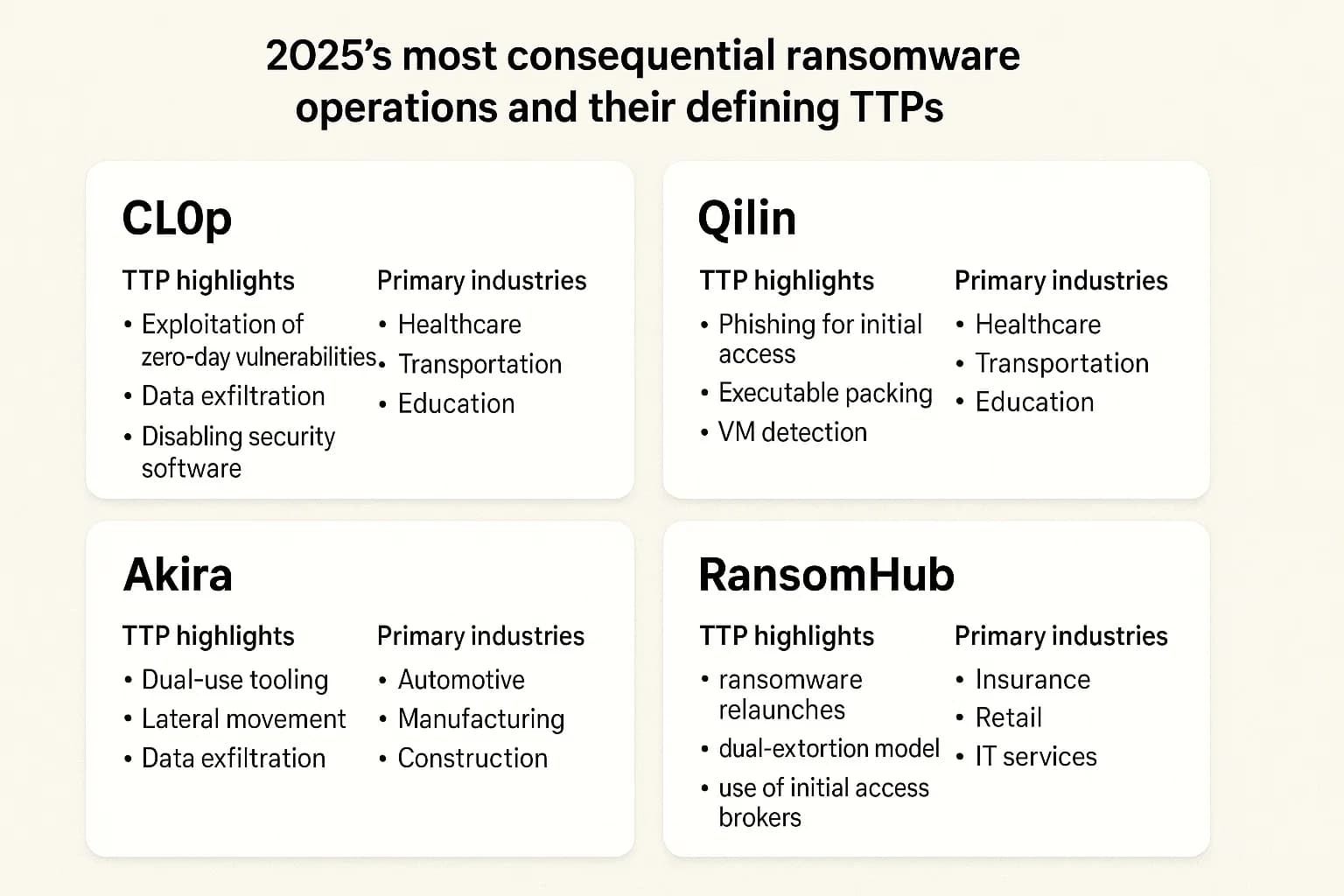
The ransomware landscape is constantly shifting, but several key players have defined the threat in 2025.
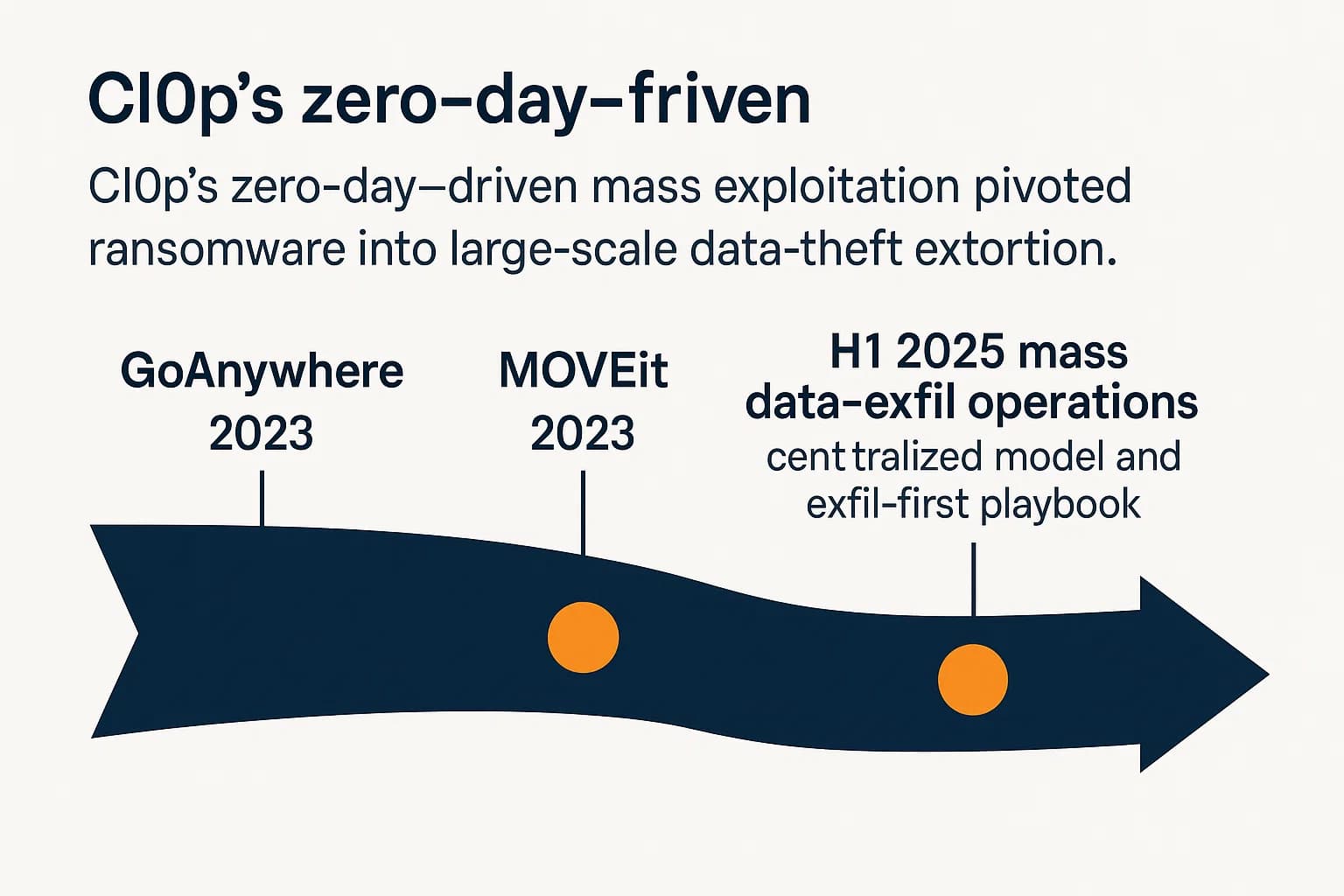

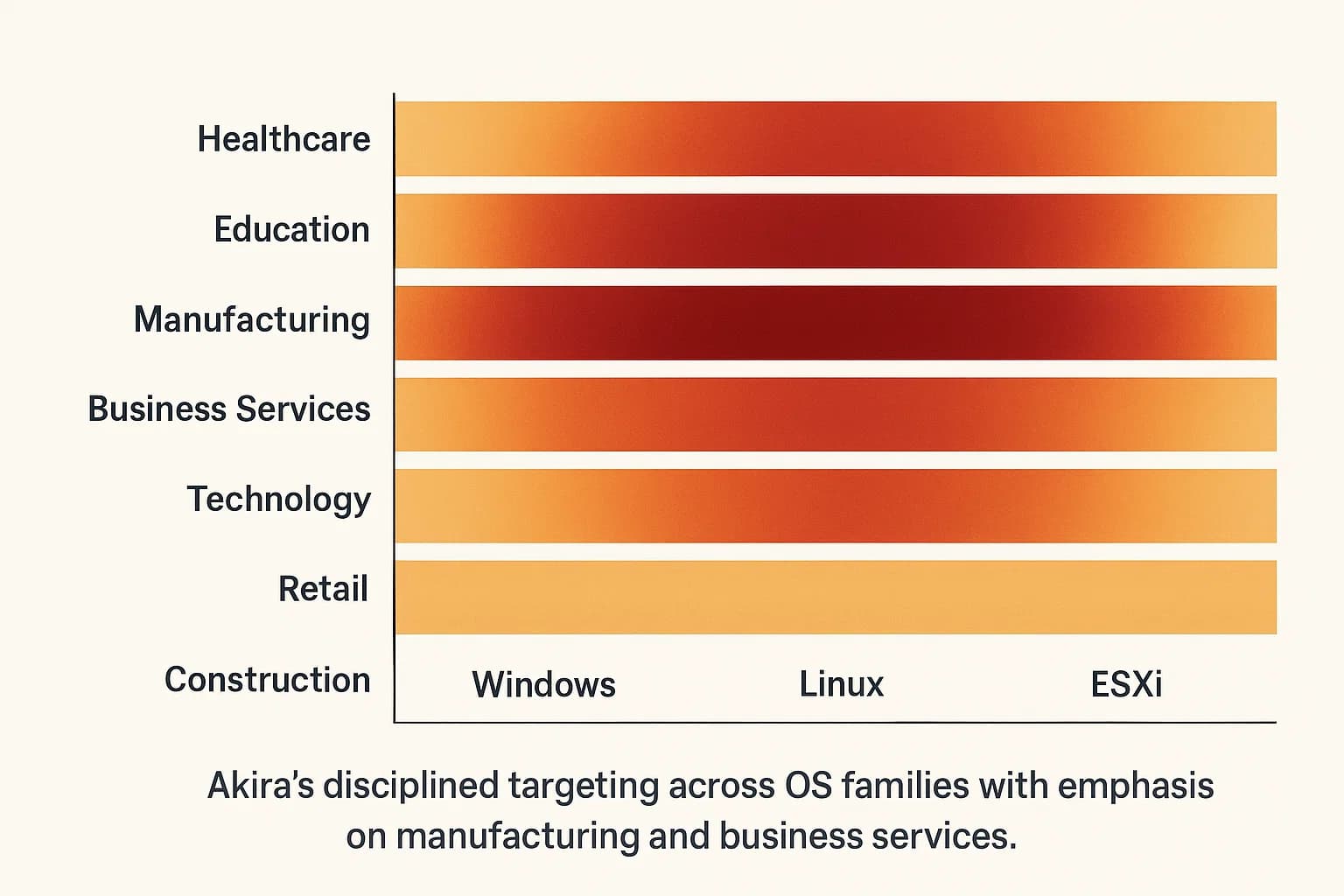
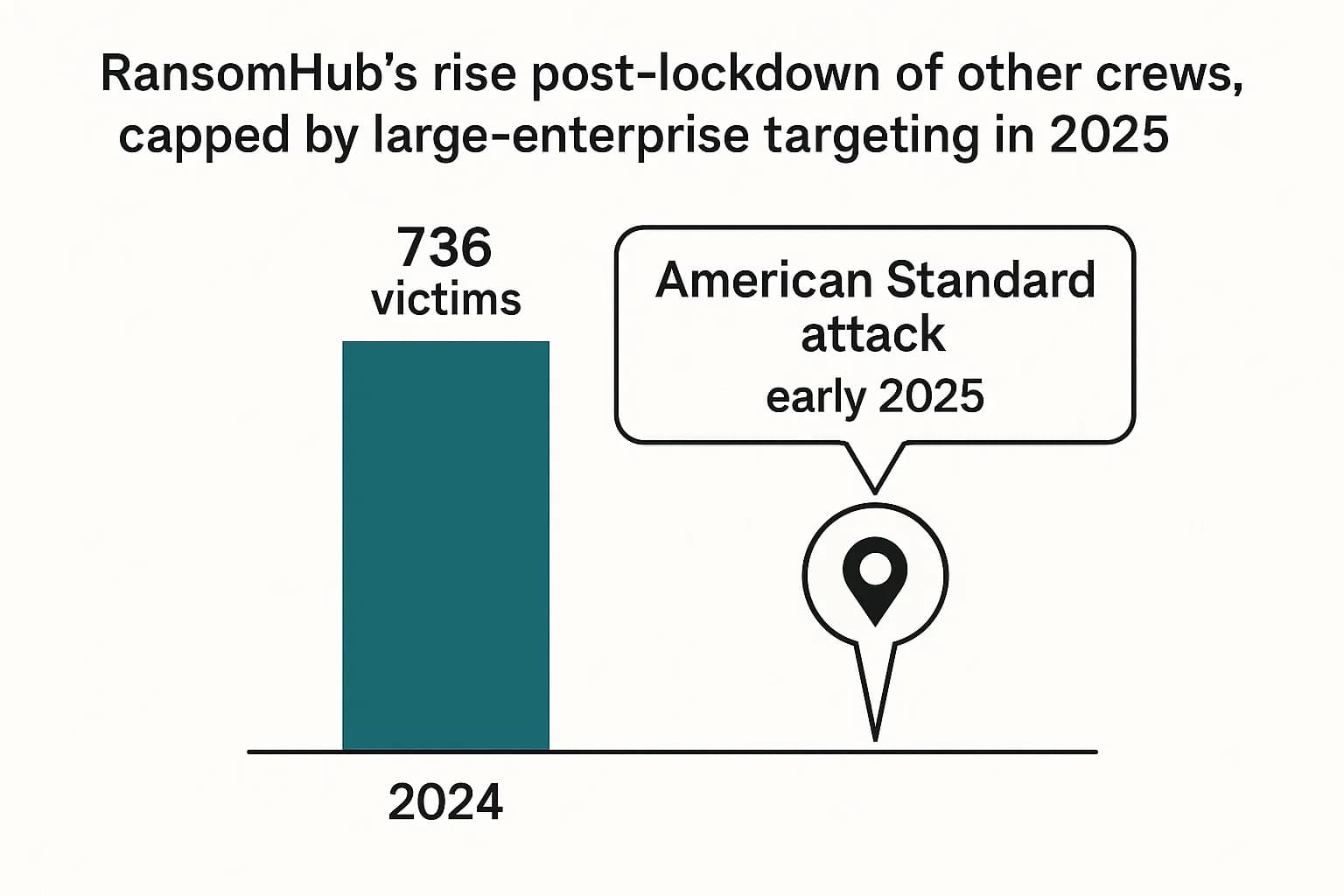
A Note on Legacy Groups
While new groups dominate the headlines, it's important to remember the names that built this criminal industry. Groups like Conti, DarkSide/BlackMatter, and Hive pioneered many of the tactics used today. Though now defunct or rebranded, their playbooks and malware source code often resurface in new operations. For example, researchers have noted similarities between Conti's TTPs and the Black Basta group, and the leaked source code of the Babuk ransomware has been repurposed by other actors. This ensures their destructive legacy continues.
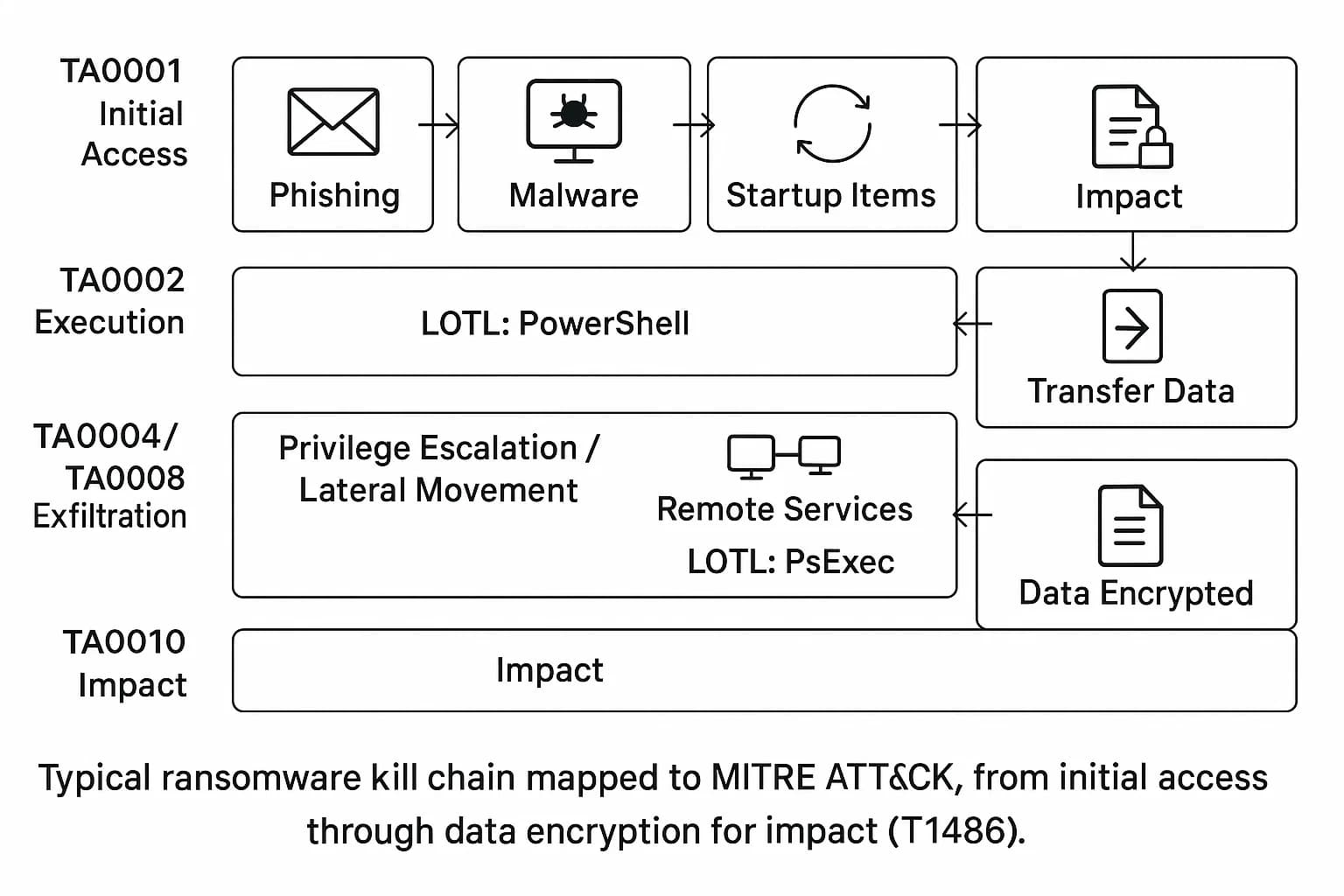
Most ransomware attacks follow a predictable lifecycle, often mapped to the MITRE ATT&CK framework. Understanding these stages is key to stopping an attack early.
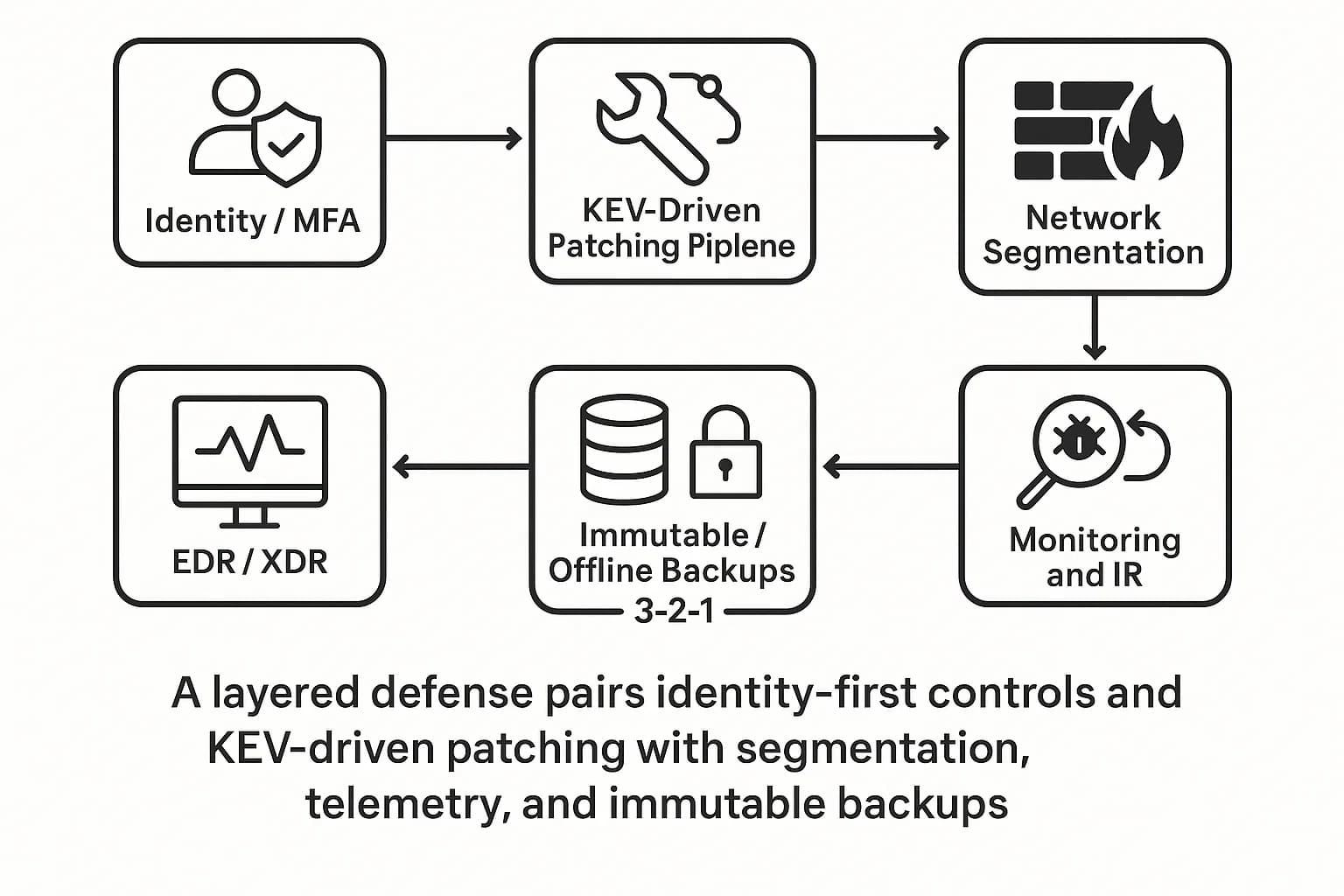
A strong defense is a layered defense. The following steps are based on expert guidance from the CISA Ransomware Guide and NIST frameworks.
Q: What is a ransomware group?
A ransomware group is an organized team of cybercriminals that uses malware to encrypt a victim's data and demand payment. Most now use double extortion, stealing data before encrypting it and threatening to leak it online to force payment.
Q: How does RaaS (Ransomware as a Service) work?
RaaS is a criminal franchise model where developers lease ransomware tools to affiliates for a share of the profits, typically 20-30%. This model makes sophisticated attacks accessible to a wider range of criminals, fueling the rise in ransomware incidents.
Q: Who are the biggest ransomware groups now?
As of 2025, the most prominent groups are Qilin, Akira, Cl0p, and RansomHub. The landscape is highly dynamic, with new groups constantly emerging to replace those disrupted by law enforcement.
Q: What industries do ransomware groups target?
They target any industry that is likely to pay. The most heavily impacted sectors are manufacturing, healthcare, government, and professional services because downtime is extremely costly and disruptive for them.
Q: How can organizations protect themselves from ransomware?
A layered defense is crucial. The most effective measures are: maintaining secure, offline, and tested backups ; enforcing phishing resistant MFA on all critical accounts ; patching vulnerabilities promptly ; and having a well practiced incident response plan.
Q: What is double extortion in ransomware?
Double extortion is when attackers both encrypt your files and steal a copy of your data. They then demand payment for two things: the decryption key to restore your systems and a promise not to leak your stolen data publicly.
Ransomware gangs in 2025 are more sophisticated and business-like than ever. The RaaS model ensures a steady supply of attackers, and tactics like double extortion are designed to defeat traditional defenses. For the latest on attack volumes and targets, see our guide to ransomware trends.
The only effective strategy is active readiness. Building a resilient defense requires a commitment to the fundamentals: strong backups, aggressive patching, robust access controls, and continuous security validation.
Ready to Strengthen Your Defenses?
The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike with over 15 years of experience in threat intelligence and offensive security operations. Holding certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies and is a regular contributor to industry publications on threat actor TTPs. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in finance, healthcare, and critical infrastructure.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us