September 11, 2025
Updated: September 11, 2025
Master the Shared Responsibility Model, PCI DSS 4.0 changes, and scope-reduction tactics (tokenization, segmentation) across AWS, Azure, and GCP.
Mohammed Khalil

The clock has run out. As of March 31, 2025, all requirements of the Payment Card Industry Data Security Standard (PCI DSS) 4.0 are mandatory. This isn't just another version update; it's a fundamental shift in how payment security is managed, especially in the cloud. We'll break down exactly what this means for your AWS, Azure, or GCP environment.
PCI compliance in the cloud is the process of meeting the PCI DSS for any application or system that stores, processes, or transmits cardholder data within a cloud service provider's (CSP) environment. While it's a contractual obligation from the major card brands (Visa, Mastercard, AmEx) and not a federal law in the U.S., the penalties for failure are severe enough to command boardroom attention.
The stakes have never been higher. The 2025 IBM Cost of a Data Breach Report reveals the average cost of a breach in the U.S. has hit an all time high of $10.22 million. Crucially, security reports consistently show that the top threats in the cloud aren't sophisticated attacks on the CSPs themselves, but customer side misconfigurations, weak credentials, and insecure APIs. This directly ties into the core challenge of cloud PCI compliance: you are responsible for what you build.
This isn't a theoretical overview. This is a practitioner's guide based on real world audit and penetration testing experience. We'll cover the Shared Responsibility Model, tactical blueprints for AWS, Azure, and GCP, and how to navigate the validation process to build a defensible and continuous compliance program.
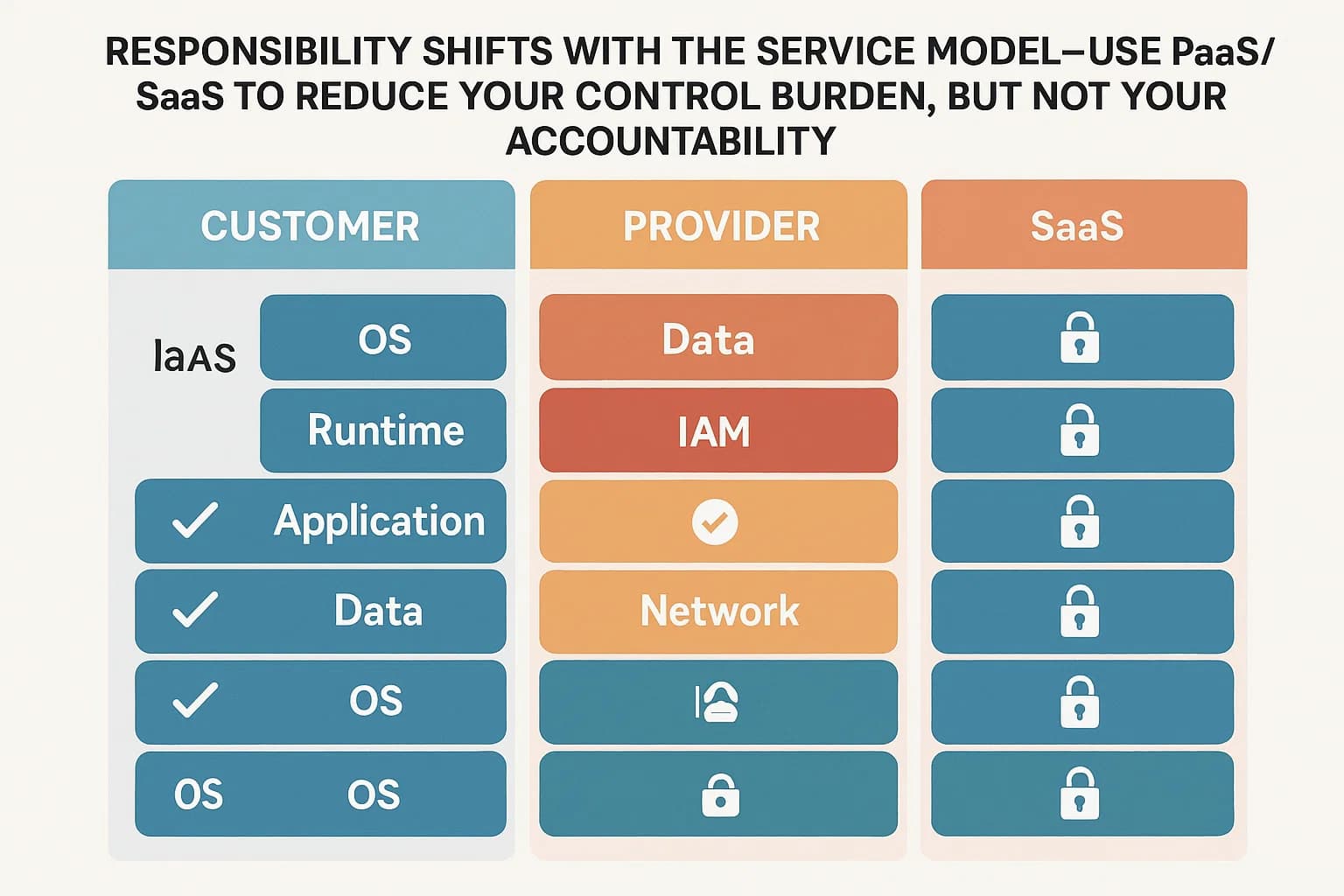
The non-negotiable foundation of cloud compliance is the Shared Responsibility Model (SRM). Getting this wrong is the root cause of most cloud compliance failures and data breaches. It boils down to a simple but critical distinction: "security of the cloud" versus "security in the cloud."
The provider be it AWS, Microsoft, or Google is responsible for protecting the foundational infrastructure that runs all of its services. This includes the physical security of their global data centers, the security of the core network fabric, and the integrity of the virtualization layer (hypervisor). This is a huge benefit, as it allows you to inherit a vast array of security controls. For example, you don't need to worry about installing cameras or biometric scanners in an AWS data center to meet PCI DSS Requirement 9 (Restrict physical access); AWS handles that for you.
You are responsible for the security of everything you create, configure, and manage within the cloud. This is your domain, and it's where auditors will focus their attention. Your responsibilities include:
This division of labor is not static; the line of responsibility shifts depending on the cloud service model you use.
Myth: "My cloud provider is PCI compliant, so my application is too."
Fact: This is the single most dangerous assumption in cloud compliance. Your provider's Attestation of Compliance (AOC) only covers their infrastructure the "security of the cloud." You must still secure your part of the shared model and undergo your own audit to prove it. You can and should download your provider's AOC and Responsibility Matrix from their respective portals AWS Artifact, Microsoft Service Trust Portal, or Google Compliance Reports Manager. These documents are not just guides; they are foundational audit artifacts that a Qualified Security Assessor (QSA) will use to define the scope of your assessment.
The traditional Shared Responsibility Model simply draws a line in the sand. If a customer misconfigures an S3 bucket and exposes cardholder data, it's the customer's fault, even though the incident reflects poorly on the cloud platform. This reality has led to a strategic evolution in how some providers view their role. Notably, Google has begun to champion the concept of "Shared Fate". This isn't just a marketing term; it's a shift that acknowledges a CSP's reputation is directly tied to its customers' security success.
A "Shared Fate" model implies a more proactive partnership. The CSP provides secure by default configurations, opinionated blueprints for compliant architectures (like GCP's PCI on GKE Blueprint), and integrated risk management tools. This is a direct response to the high rate of customer side misconfigurations being the primary cause of cloud data breaches. It's a business imperative for CSPs to help customers succeed, as major breaches on their platform, regardless of fault, cause significant reputational damage. When choosing a CSP, it's wise to evaluate not just their compliance status but the maturity of their "Shared Fate" offerings. How effectively do their native tools and blueprints accelerate your own compliance journey?
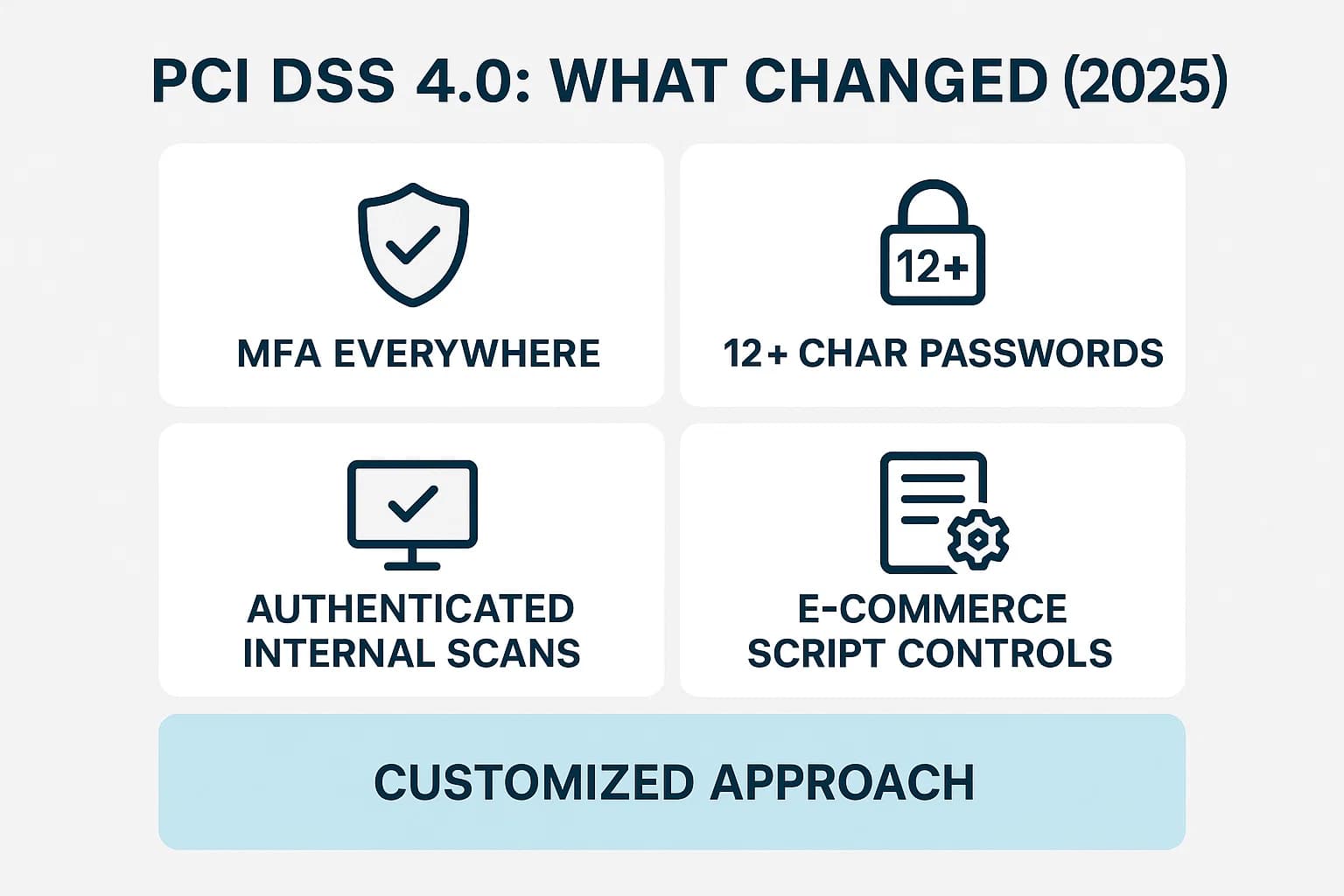
The transition to PCI DSS 4.0 is complete, with all new requirements becoming mandatory as of March 31, 2025. The standard's main goal is to promote security as a continuous process and add flexibility for modern technologies like the cloud, moving away from a simple "point in time" audit mentality.
Several new and updated requirements in v4.0 have a significant impact on cloud deployments:
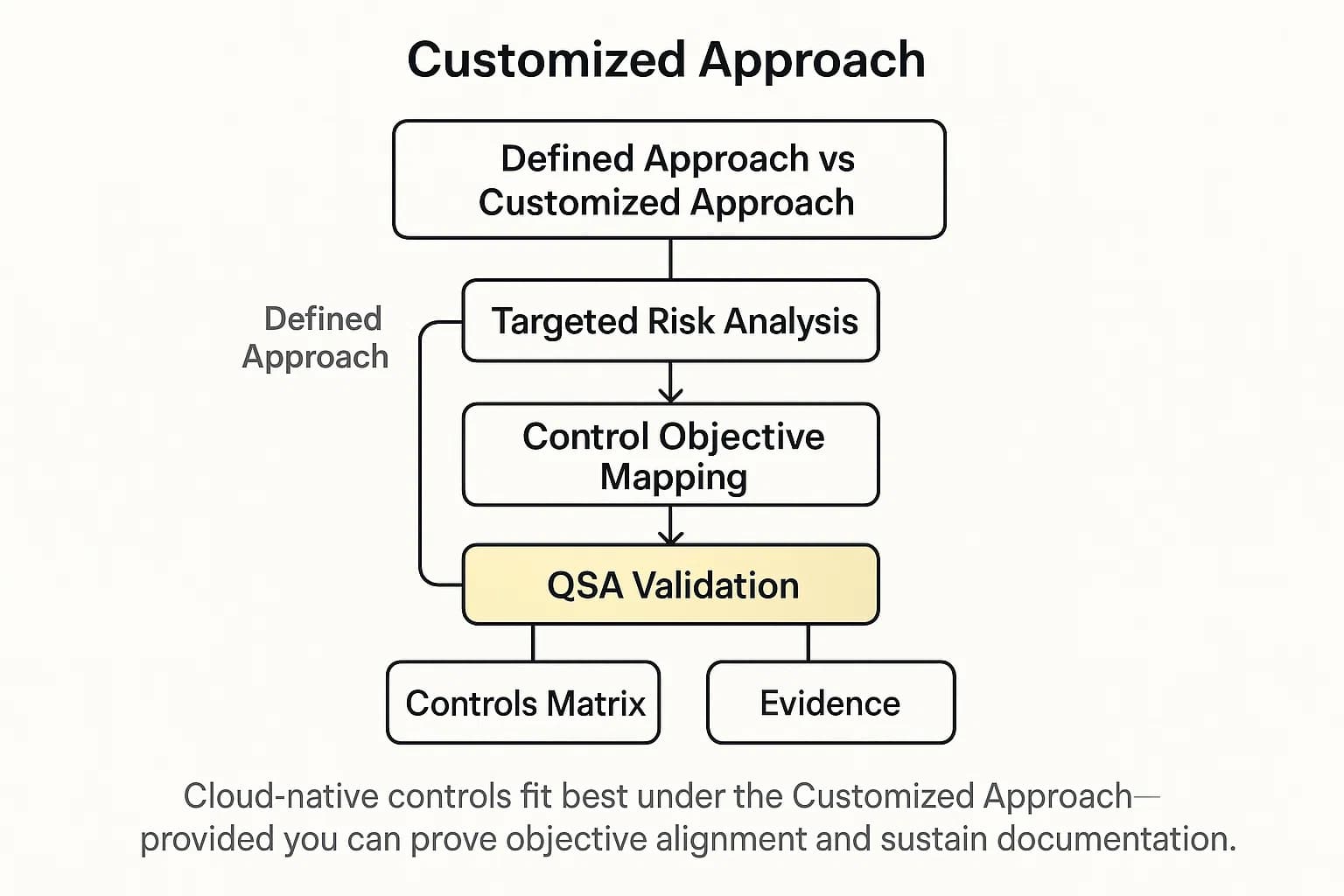
Perhaps the most significant change in PCI DSS 4.0 is the introduction of the "Customized Approach." Instead of rigidly following the "Defined Approach" (the traditional checklist of controls), organizations can now design and implement their own controls to meet a requirement's objective.
This is a critical enabler for cloud native environments. It allows you to use innovative, cloud specific solutions that don't fit the old, on premises model. For example, instead of a traditional hardware firewall appliance to meet Requirement 1, you can use a combination of AWS Security Groups, Network ACLs, and a Web Application Firewall (WAF), and then demonstrate to an auditor how this combination achieves the same security objective.
However, the customized approach is not an easy way out. The PCI SSC has stated it is best suited for "risk mature" organizations with established risk management programs. For each custom control, you must:
The ability to effectively use the customized approach serves as a direct indicator of an organization's cloud security maturity. A traditional "lift and shift" organization will likely stick to the defined approach, attempting to replicate on premise controls in the cloud. In contrast, a cloud native organization will want to leverage services like serverless functions, managed databases, and automated security groups, which don't map cleanly to the old checklist. To justify these modern controls to an auditor, they must use the customized approach, which demands deep documentation and risk analysis. Successfully navigating a customized approach assessment proves you not only have strong technical controls but also the robust governance, risk, and compliance (GRC) processes to back them up. It's a powerful signal to auditors and partners that you have a sophisticated and well managed cloud program.
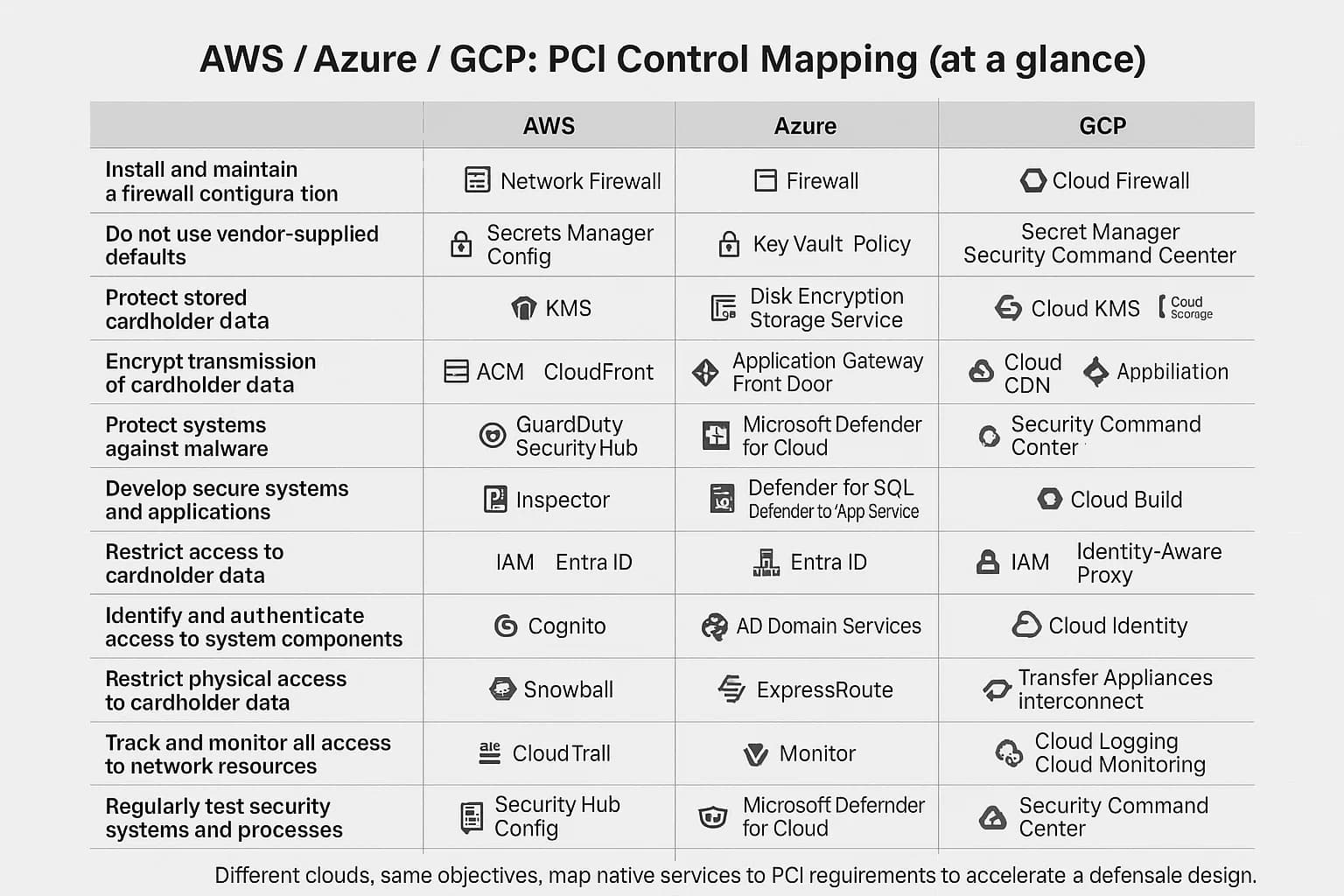
All three major cloud providers AWS, Microsoft Azure, and Google Cloud are certified as Level 1 Service Providers. This means they provide a compliant foundation, but the tools, service names, and implementation details differ. The following provides a practical mapping of their core services to the 12 PCI DSS requirements, helping you architect your side of the responsibility model.
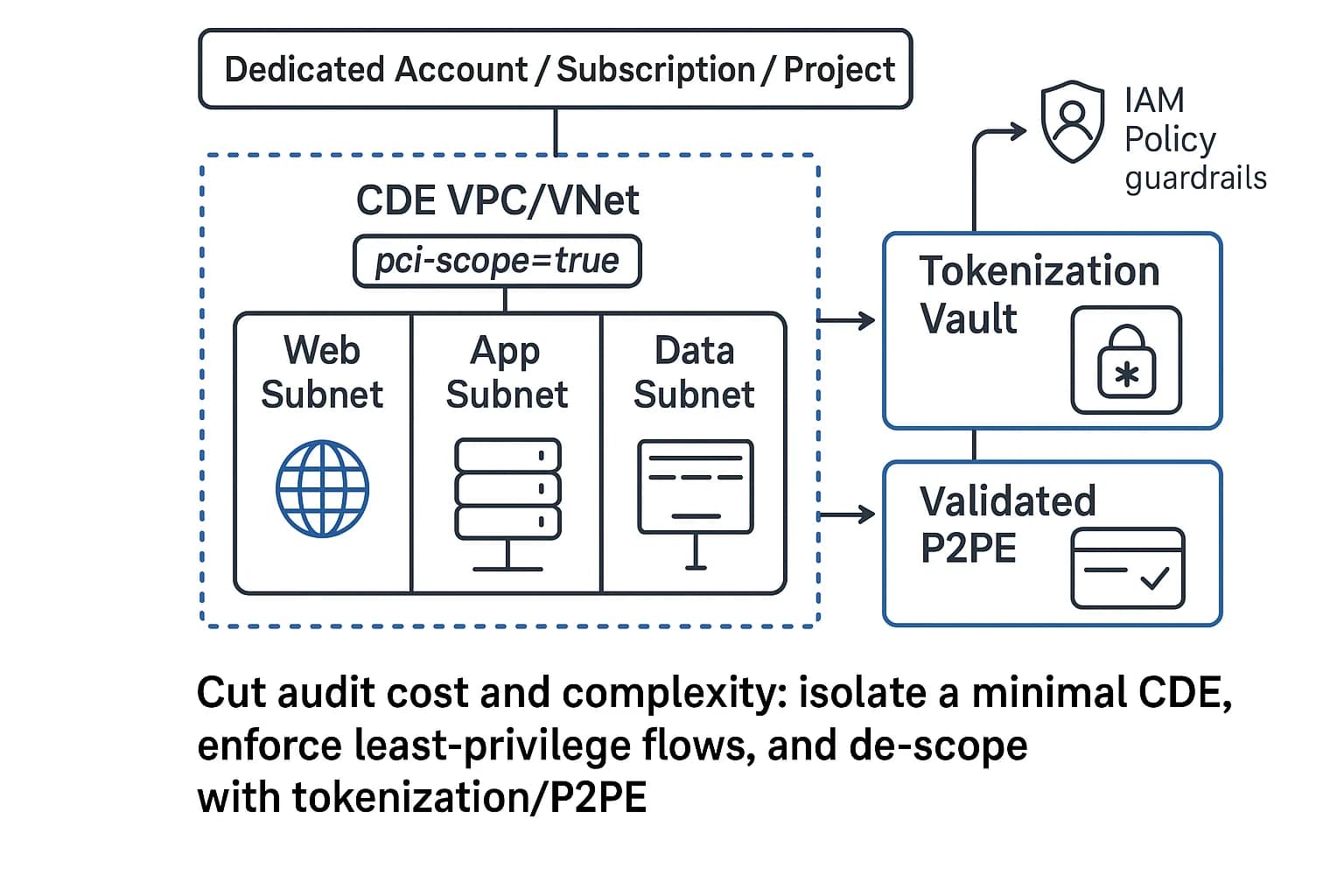
The single most impactful strategy for managing the cost and complexity of a PCI DSS audit is to minimize the scope of your Cardholder Data Environment (CDE). The CDE includes all the people, processes, and technology that store, process, or transmit cardholder data (CHD) or sensitive authentication data (SAD). The guiding principle is simple: if a system doesn't need to touch cardholder data, it shouldn't be in the CDE. A smaller, well defined CDE is easier to secure, monitor, and audit.
Here’s a step by step guide to building a tightly scoped CDE in the cloud:
Beyond network controls, you can use data centric approaches to remove systems from scope entirely.
Mini Case Study: A Level 1 merchant recently migrated their payment processing flow from monolithic EC2 instances to a serverless architecture using AWS Lambda and a tokenized payment gateway. This strategic shift reduced the number of customer managed controls for PCI DSS Requirement 11 by over 30% and cut their annual audit preparation time by nearly 40%, as entire categories of OS level patching and monitoring became AWS's responsibility.
In a traditional on premise world, the CDE was defined by a physical rack of servers and a specific VLAN. The network diagram was the ultimate source of truth for the audit boundary. In the cloud, this is no longer the case. A Lambda function in one VPC can access an S3 bucket in another, completely bypassing traditional network controls. The only thing governing that connection is an IAM policy. This means that identity and metadata have become the new perimeter. A robust resource tagging strategy (e.g., applying a tag like
pci scope=true to all CDE components) becomes a powerful compliance tool. Security policies, firewall rules, and monitoring alerts can then be applied dynamically to any resource bearing that tag. Your security and compliance teams must shift their mindset: the CDE is no longer just a network segment; it's a collection of resources defined by IAM roles and metadata tags. A failure to properly manage IAM and tagging is a failure to manage your CDE boundary.
Building a secure environment is only half the battle; you also have to prove it's effective. The validation process is how you demonstrate compliance to the card brands and your acquiring bank. This is why it's crucial to understand why continuous penetration testing matters.
Your required validation method is determined by your merchant level, which is based on your annual volume of payment card transactions.
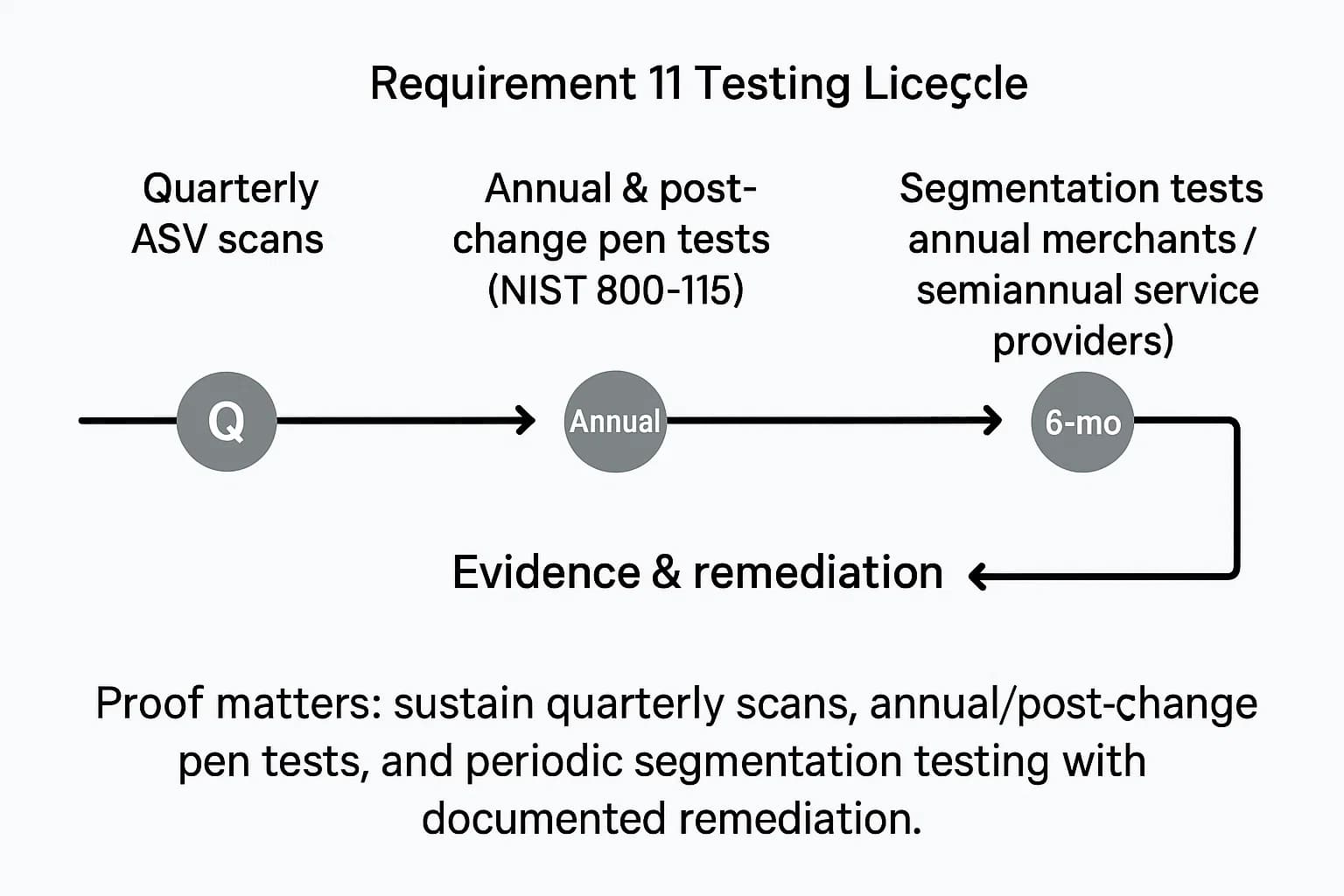
Requirement 11 is all about regularly testing your security systems and processes. It's one of the most hands-on parts of the standard.
Budgeting for PCI compliance requires a realistic view of both direct and indirect costs. However, these expenses pale in comparison to the financial and reputational fallout of non compliance.
A typical PCI compliance budget includes several key components:
The costs of getting compliance wrong are far more severe:
It's clear that PCI DSS compliance should not be viewed as a mere cost center, but as a strategic investment in risk reduction. Research shows that the average cost of non compliance is nearly three times higher than the cost of maintaining a compliance program. The initial investment in a QSA audit, penetration test, and necessary security tools might seem high. However, a single non compliance fine for a few months could easily exceed that amount, even without a breach occurring. A single data breach, with an average cost in the millions, represents an existential threat to many businesses. The controls required for PCI DSS strong segmentation, encryption, comprehensive logging, and regular testing are the very same controls that form the foundation of a mature security program. Therefore, the budget allocated for PCI is not just for a certificate; it's a budget for foundational cybersecurity that protects the entire business.
Yes, absolutely. All major cloud providers are Level 1 PCI DSS compliant service providers. However, their compliance only covers the infrastructure ("security of the cloud"). You are still responsible for securing your applications and data according to the Shared Responsibility Model.
PCI DSS is a prescriptive standard focused specifically on protecting payment card data, with 12 strict requirements. SOC 2 is a flexible framework based on the Trust Services Criteria (Security, Availability, Confidentiality, Processing Integrity, Privacy) that reports on an organization's security controls but doesn't dictate exactly which controls to use. Many organizations that handle payments will need to comply with both.
PCI DSS 4.0 is much better suited for the cloud. The "Customized Approach" allows organizations to use cloud native security controls (like security groups and serverless functions) instead of traditional on premise solutions. It also mandates stronger controls like MFA for all access to the CDE, which is critical in cloud environments where admin consoles are accessible over the internet.
The first and most critical step is scoping. You must identify and document every system, process, and person that interacts with cardholder data to define your Cardholder Data Environment (CDE). Without an accurate scope, you cannot apply the necessary controls or effectively reduce your compliance burden.
Not automatically. Using a compliant payment gateway like Stripe or Square can significantly reduce your scope, often allowing you to qualify for a simpler SAQ (like SAQ A). However, you are still responsible for ensuring your own systems (like your e-commerce server) don't inadvertently handle or store card data and are securely configured.
For merchants, segmentation testing must be performed at least annually. For service providers, PCI DSS 4.0 requires it to be performed every six months. It must also be performed after any significant change is made to the segmentation controls.
The biggest and most common mistake is fundamentally misunderstanding the Shared Responsibility Model. Many companies incorrectly assume that because their cloud provider is compliant, they are compliant by extension. This leads to neglecting their own responsibilities for data encryption, access control, and vulnerability management, which is precisely where most cloud breaches occur.
The path to sustainable PCI compliance in the cloud is clear: master the Shared Responsibility Model, be relentless in reducing your scope, and embrace automation to make security a continuous process, not a point in time audit.
The rigor demanded by PCI DSS 4.0 should not be seen as a burden. The disciplines it enforces, strong access control, comprehensive logging, robust vulnerability management, and a risk based security mindset are the very cornerstones of a mature and resilient cloud security program. Achieving PCI compliance is a byproduct of building a secure environment. By using the standard as a framework, you're not just protecting cardholder data; you're building a foundation of security that protects your entire business, enhances customer trust, and enables you to innovate safely in the cloud.
Ready to Strengthen Your Defenses?

The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
PCI Security Standards Council : PCI DSS Overview
PCI SSC : Self Assessment Questionnaires (SAQs)
Microsoft Service Trust Portal
Azure Policy : PCI DSS initiative
Google Cloud : Compliance Reports Manager
Google Cloud : Security Command Center
Google Cloud : VPC Service Controls
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us