December 21, 2025
Updated: December 21, 2025
How stolen credentials, infostealer logs, and AI phishing now power most breaches
Mohammed Khalil

Information stealing malware infostealers or stealers are malicious programs designed to covertly siphon sensitive data from infected systems. Unlike noisy ransomware that announces its presence, infostealers operate stealthily, often remaining undetected while they pilfer credentials, browser cookies, credit card numbers, crypto wallet keys, and more. The stolen data is compiled into archives known as stealer logs, which have become a hot commodity in the underground economy. In 2024, infostealer activity reached unprecedented levels IBM X Force observed an 84% year over year increase in infostealers delivered via phishing emails. Mandiant reported that stolen credentials many sourced from infostealer logs became the second most common initial infection vector in 2024, involved in 16% of incidents second only to exploits. This trend underscores a decisive shift: instead of breaking in through exploits, threat actors are simply logging in with stolen passwords.
Several industry reports highlight why 2025 has seen an infostealer escalation. Verizon’s Data Breach Investigations Report DBIR found that credentials stolen by infostealers played a role in a huge share of breaches; 54% of ransomware victims had their domains appear in infostealer credential dumps. IBM’s Threat Intelligence Index noted credential harvesting was the top attack impact in 29% of incidents. Meanwhile, the sheer volume of data stolen is staggering. One security analysis found 53 million+ compromised credentials and 13 million infected devices tied to infostealer activity in 2024. In short, infostealers provide the fuel a trove of login data and identity artifacts that powers countless cybercrimes, from account takeovers and fraud to ransomware attacks facilitated by easy network access. This article examines how stealer malware works and ranks the top infostealer families of 2025 by their impact on the threat landscape, with a focus on Lumma Stealer, RedLine, Raccoon, and Vidar prolific malware families that epitomize this threat.
Infostealer malware typically spreads via social engineering and trojanized software, infecting PCs en masse to gather as many credentials as possible. Once on a victim machine, a stealer will quickly harvest sensitive data common techniques include form grabbing intercepting data users submit in web forms and keylogging to capture passwords as they are typed. Most stealers target web browsers as a primary source, extracting saved passwords, stored credit card details, cookies, browser history, and auto fill records. Many also look for popular application data: email client logins, FTP client credentials, VPN and remote access tool passwords, chat app tokens, gaming service logins, and cryptocurrency wallet files. All of this information is gathered silently in the background, often before endpoint security tools can detect the malicious activity.
After collecting data, the malware compiles the loot into a stealer log typically a ZIP file or folder containing multiple text files and folders. For example, a single infostealer log may include files like All Passwords.txt all captured credentials with associated site names, Cookies\ a folder of stolen browser cookie files, Wallets\ cryptocurrency wallet data, Autofill.txt saved form data like names and addresses, System.txt system info such as OS, IP address, hardware details, and even a desktop screenshot Screen.png. The stealer then exfiltrates this bundle to the attacker either directly to a command and control C2 server or via intermediary channels some stealers send logs over HTTP POST, others use Telegram bots or cloud storage. Notably, infostealers historically did not maintain long term persistence on the host many are smash and grab, meaning they run, dump data, send it off, and self delete. This is beginning to change; a few newer variants install persistence to collect data over time more on that later. In most cases, by the time a victim notices anything amiss if ever, their data is already packaged and shipped to criminals.
Once exfiltrated, stealer logs become currency on the underground market. Cybercriminals aggregate and sell these logs on dark web marketplaces or private channels. For instance, the Russian Market and other illicit forums offer automated shops where buyers can search stolen logs by keywords, company domain, software, etc.. Telegram channels also serve as bazaars for fresh logs. The value of logs lies in the credentials and identity data they contain other threat actors purchase them to facilitate their own attacks. A single log might be sold to multiple buyers or in exclusive sales for premium data. Prices vary widely: an individual machine’s log might sell from $1 up to $100 or more depending on the richness of the accounts logs with banking, crypto, or corporate logins fetching higher prices. Meanwhile, initial access brokers IABs parse logs for valuable enterprise credentials VPN logins, RDP passwords, SaaS accounts and sell network access to those organizations for anywhere from a few hundred to several thousand dollars. In effect, infostealer logs enable a supply chain of crime: one group steals the data, another monetizes it through resale or leveraging the creds directly. This ecosystem has matured such that stolen passwords are now the lifeblood of many attacks Verizon reported 88% of web application breaches involved stolen credentials, and Mandiant emphasizes that access obtained via infostealers is a key enabler for intrusions across the board.
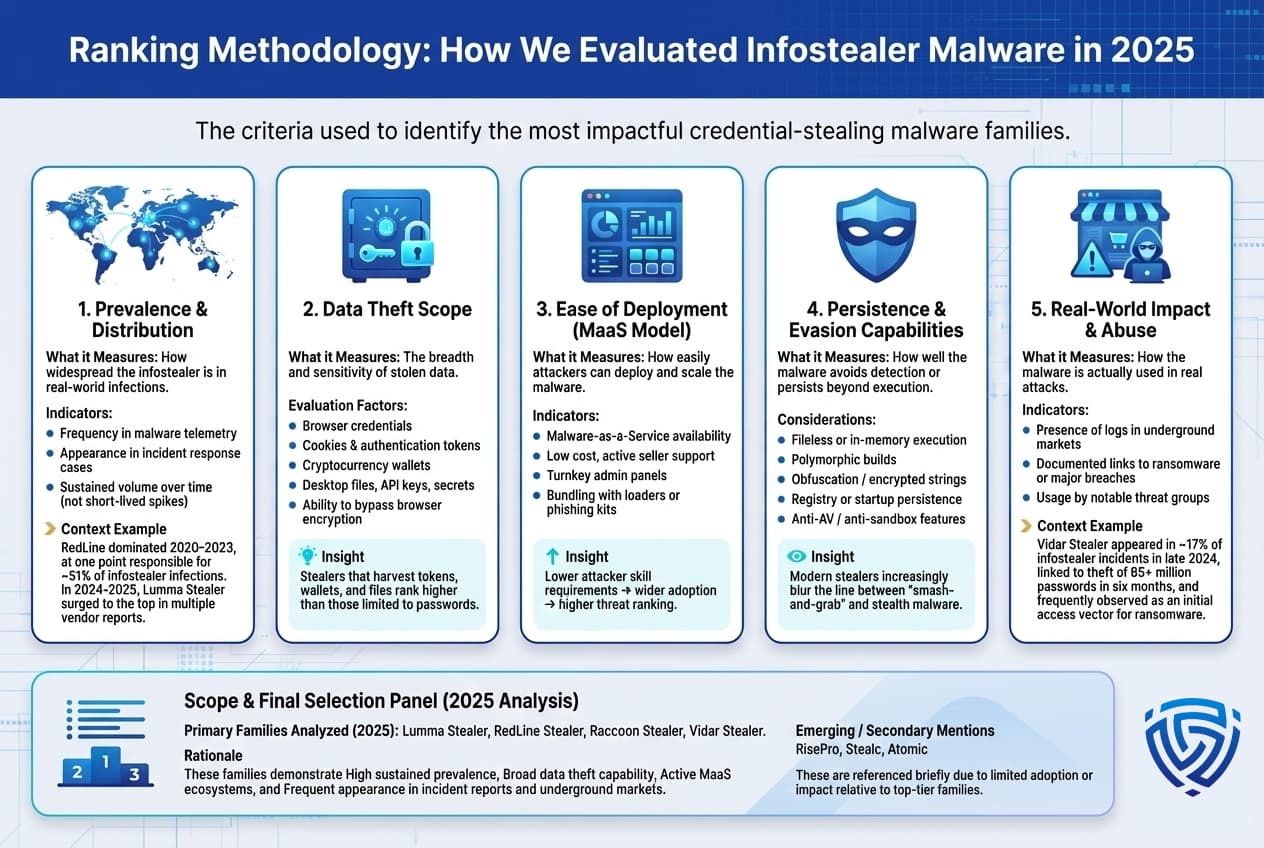
Not all infostealer families are equal. This ranking focuses on the most impactful stealer malware of 2025, based on several criteria:
Using these criteria, we focus on four major infostealer families dominating the landscape in 2025: Lumma Stealer, RedLine, Raccoon, and Vidar. These were chosen due to their high prevalence as noted by multiple security sources and their central role in the underground credential theft economy. Notably, emerging stealers like RisePro, Stealc, and Atomic are also in circulation, some are even referenced as up and coming in vendor reports but unless they demonstrated significant adoption or innovation, they are mentioned only briefly. The following sections break down each top family in a consistent format to understand why they matter, how they work, and how defenders can respond.
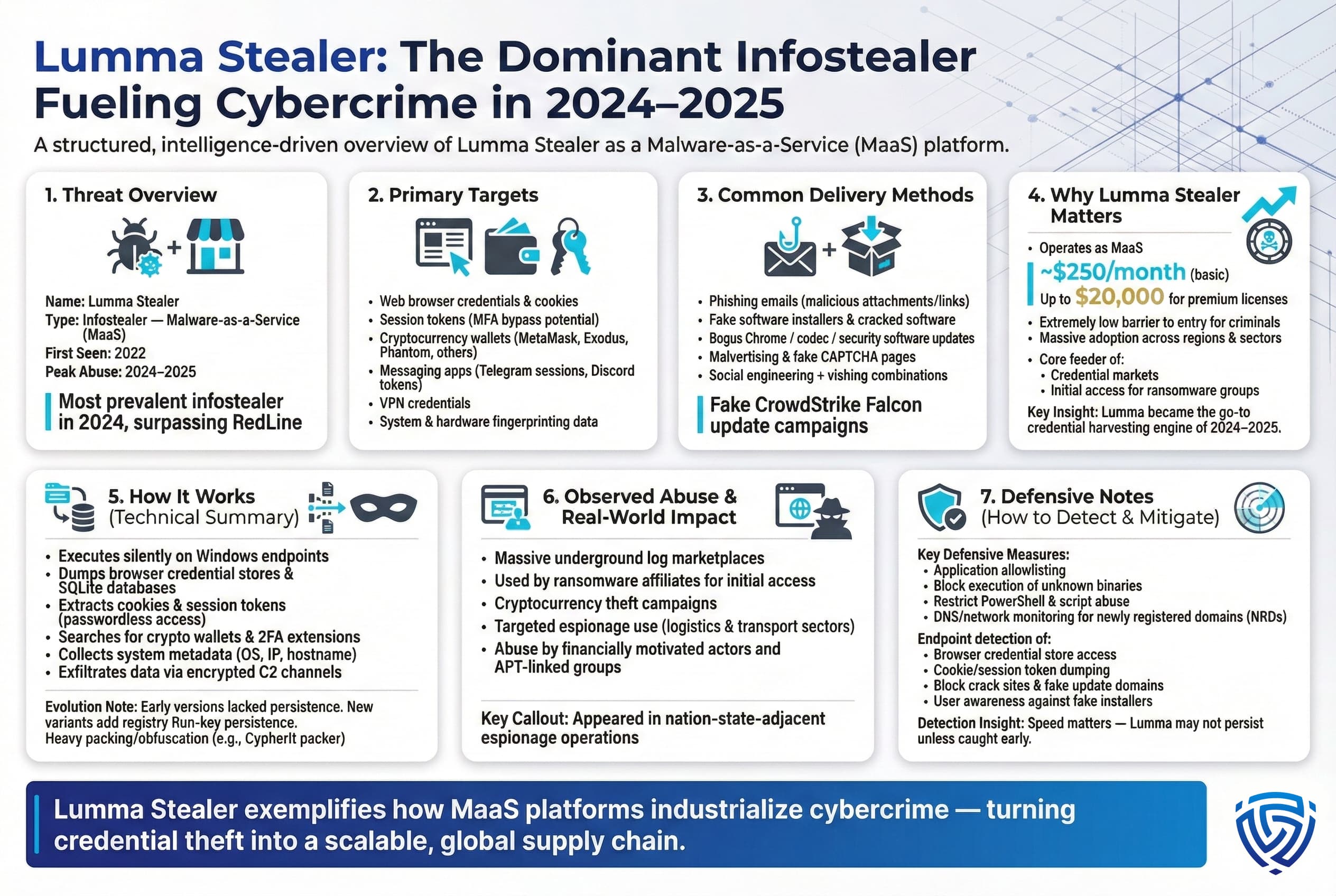
Why It Matters: Lumma Stealer emerged in 2022 and by 2024 rose to prominence as one of the most widely abused infostealers. It operates as a Malware as a Service, criminals can subscribe for as low as ~$250 per month basic up to $20,000 for premium licenses which dramatically lowers the skill and cost required to launch campaigns. This MaaS model, combined with Lumma’s effectiveness, led to rapid adoption across multiple regions and sectors . By mid 2024, Lumma overtook older stealers in prevalence; IBM’s data showed LummaStealer as the most common infostealer in 2024, surpassing even RedLine. Threat actors gravitated to Lumma due to its adaptability and the advanced tactics seen in distribution. Campaigns distributing Lumma have employed everything from spear phishing with CrowdStrike lookalike installers impersonating security software updates to mass spam combined with vishing voice calls to convince victims to run the malware. In short, Lumma Stealer matters because it became a go to tool for cybercriminals in 2024–2025, fueling a huge volume of credential theft and appearing in countless log sales.
How It Works: Once executed on a Windows system, Lumma Stealer runs stealthily in the background, harvesting a wide range of information without obvious signs to the user. It first targets common sources of credentials: extracting saved usernames/passwords from browsers, pulling cookies and session tokens, and gathering auto fill data that might include addresses, phone numbers, and other PII. The malware also collects system details machine name, OS version, IP address, hardware identifiers which help attackers fingerprint the victim. Lumma is known to search for cryptocurrency wallet files for popular wallets like MetaMask or Exodus and can even target certain 2FA browser extensions to grab authentication data. All stolen data is aggregated and exfiltrated to the attacker’s server via encrypted channels, often a designated Lumma C2 panel. Initially, LummaStealer did not maintain persistence on the system meaning if the computer rebooted, it wouldn’t survive. However, recent variants introduced a persistence mechanism via registry Run keys to auto start the malware on reboot. This evolution shows the developers investing in longer term access. Lumma is also packed and obfuscated using techniques e.g. CypherIt packer, as noted by CrowdStrike to evade antivirus detection.
What Gets Stolen: LummaStealer’s data theft scope is broad. It snatches credentials and cookies from all major browsers Chrome, Edge, Firefox, Opera, etc., which often include website logins, stored session tokens, and even saved credit card info. It grabs browser histories and bookmarks useful for profiling the victim. It gathers system information like hostname, OS, installed software, and IP/location. It specifically hunts for cryptocurrency wallet files and seed phrases one report noted Lumma logs include files or indicators for wallets like MetaMask and Phantom a Solana wallet. Any installed crypto wallet applications are a target. Lumma also may steal messaging app data Telegram session files, Discord tokens and VPN client credentials if present similar to RedLine’s capabilities. In some campaigns, it was observed grabbing authentication cookies used for MFA bypass for instance, stealing session cookies that could let an attacker impersonate the user without needing a password. In summary, Lumma aims to vacuum up everything an attacker could monetize: passwords, financial info, digital currency, and platform tokens.
Observed Abuse: LummaStealer has been linked to both financially motivated cybercrime and espionage campaigns. On the cybercrime side, it plays a huge role in the credential theft economy Lumma logs are frequently sold on underground markets the malware’s own LummaC2 service has an invite only marketplace for logs and used for follow on fraud and network intrusions. For example, ransomware affiliates have likely sourced initial access via Lumma logs containing VPN or RDP credentials. One high profile incident in June 2024 involved Lumma being distributed via a fake CrowdStrike Falcon update, indicating that even savvy users IT personnel were targeted. On the espionage side, Cybereason reported that APT linked actors possibly with Russian or Chinese backing leveraged Lumma in targeted attacks against logistics and transportation companies in North America. In those cases, spear phishing emails delivered Lumma to conduct data theft on corporate networks potentially to gather emails, intellectual property, or as a foothold for further espionage. Additionally, Lumma has been a tool for cryptocurrency theft: campaigns aimed at individual crypto holders have used Lumma to steal wallet keys and 2FA tokens, leading to direct theft of crypto assets . The malware’s versatility useful for both financial crime and spying and wide availability mean it has shown up in a variety of threat investigations globally.
Defensive Notes: Defending against Lumma Stealer is challenging because of its rapid evolution and multi faceted delivery. New phishing lures and fake installer tactics are constantly observed from fake CAPTCHA sites to trojanized software on YouTube and GitHub links. Enterprises should implement layered defenses: block execution of unknown binaries, application allowlisting, and restrict scripting engines like PowerShell, which Lumma sometimes uses for payload delivery and even persistence setup . Network defenders can monitor for telltale signs: Lumma often uses newly registered domains NRDs for its C2 infrastructure, so connections to suspicious new domains or to known Lumma C2 addresses some campaigns use Telegram API as well should be flagged. On endpoints, focus on behaviors: the act of a process dumping browser credential stores or accessing browser SQLite files, or a user space process reading Firefox/Chrome profile data, could indicate an infostealer EDR tools can detect these suspicious actions. Since Lumma’s lack of initial persistence might allow it to slip by if not caught during execution, speedy detection is key. Also, because Lumma is often delivered via fake software cracks and updates, user education and web filtering play a role: blocking access to known crack sites and warning users against downloading software from untrusted sources can reduce infections. In short, a combination of technical controls, endpoint, network, DNS filtering and user awareness is required to counter Lumma’s threat.
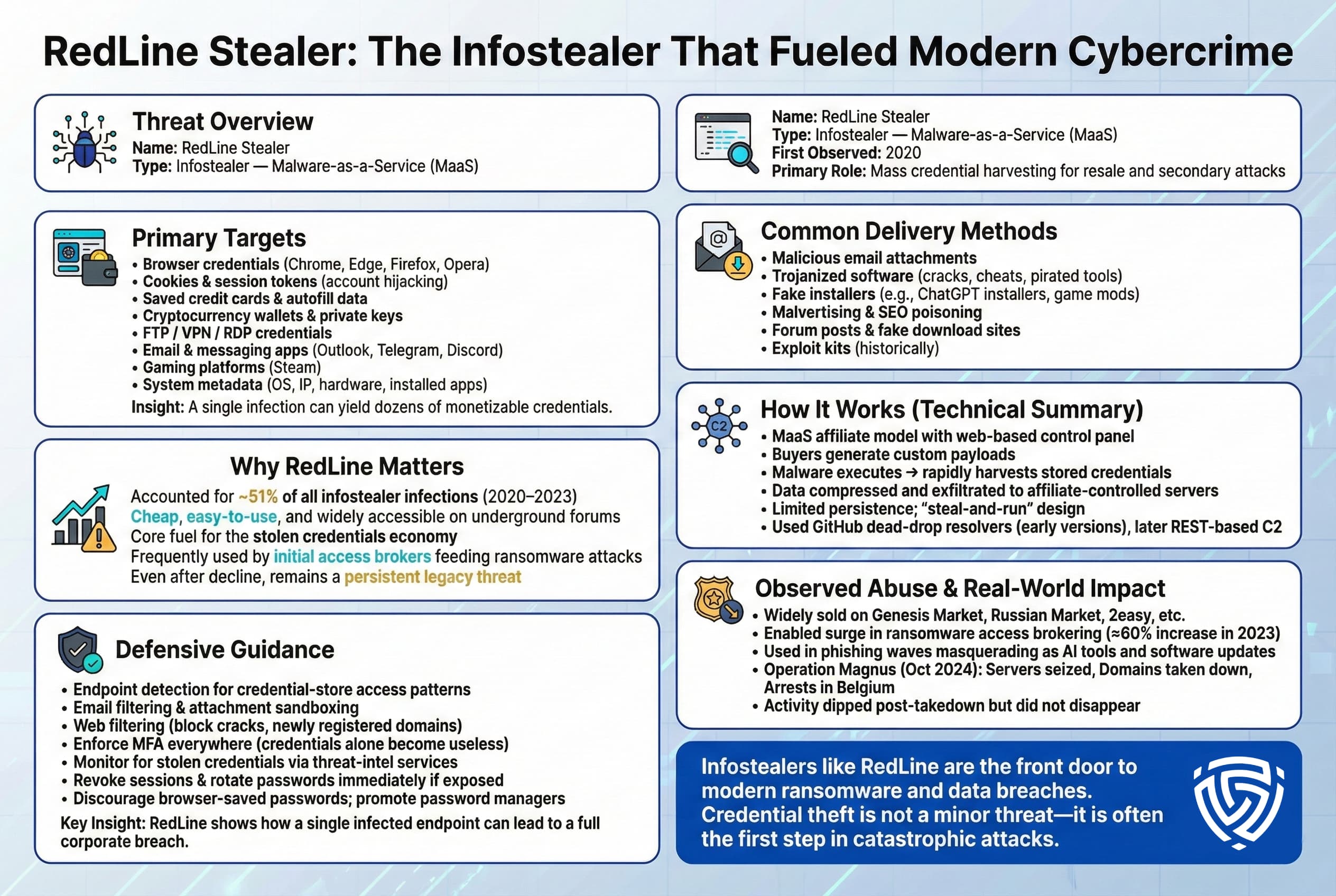
Why It Matters: First identified in 2020, RedLine Stealer became one of the most pervasive info stealers in the early 2020s. Its popularity was due to a perfect storm of features: it was sold cheaply and openly on Russian underground forums available to virtually any criminal, easy to use with a web based control panel, and effective at grabbing a wide array of valuable data. According to Kaspersky telemetry, RedLine accounted for over half 51% of all infostealer infections from 2020 through 2023 an astonishing share that attests to how many threat actors were leveraging it. This stealer essentially fueled the initial boom of the stolen log marketplace; throughout 2021–2022, RedLine logs became synonymous with big troves of credentials being sold in bulk. Even as newer competitors emerged, RedLine remained widely used though its dominance dipped by 2024, with IBM ranking it the fifth most used stealer as Lumma and others rose. Another reason RedLine matters is its involvement in real world incidents: many corporate breaches have been traced back to stolen RedLine credentials. Ransomware crews and access brokers have openly favored RedLine logs for finding VPN/RDP credentials to penetrate organizations. In essence, RedLine was a workhorse of cybercrime for several years, and even after law enforcement actions described below, its legacy and variants continue to threaten organizations.
How It Works: RedLine operates on a MaaS affiliate model. Buyers affiliates purchase a subscription monthly or lifetime and receive access to a web based control panel that allows them to generate customized malware binaries and receive stolen data. The RedLine malware binary, once delivered to victims via email attachment or download, executes and begins its info stealing routines. It will typically scan for installed browsers and applications and extract stored credentials, cookies, and other data using built in routines for each app for browsers, it accesses SQLite databases or credential stores; for apps like Discord/Telegram, it might grab session files. RedLine also can deploy simple keyloggers and form grabbers to capture input that isn’t already saved. The stolen data is then packaged, often compressed, and sent back to the affiliate’s control server which, in the RedLine model, is often self hosted by each buyer using the panel they got. ESET’s analysis of RedLine’s backend revealed it had a somewhat sophisticated infrastructure: earlier versions used GitHub repositories as dead drop resolvers to retrieve the addresses of control servers, and newer versions shifted to using a REST API model for C2 communications. RedLine does not usually persist after execution it aims to steal and transmit data quickly before it’s caught. It also has had multiple generations with various obfuscation techniques; researchers found hundreds of unique RedLine panel IP addresses and many distinct samples, indicating how widespread and diversified its use was.
What Gets Stolen: RedLine is a comprehensive stealer. It targets nearly all common credential sources on Windows. This includes: Browser data saved logins usernames/passwords from Chrome, Firefox, Edge, Opera, etc., cookies which can hijack logged in sessions, browsing history, and saved autofill info names, addresses, phone, which are useful for identity theft. Cryptocurrency it locates files or wallet data for crypto wallet apps e.g. wallets like Exodus, Jaxx, Ethereum wallet files and can steal private keys if they're stored insecurely. Application credentials RedLine scans for credentials in FTP clients FileZilla, etc., VPN clients, email clients Outlook, Thunderbird, and messaging apps Telegram, Pidgin. It was even known to steal gaming credentials e.g., Steam accounts and information from VPN and remote desktop tools, as noted by ESET. It grabs system information including the computer name, user name, OS, installed software list, and sometimes running processes data that helps log sellers advertise the log e.g., contains Steam, Discord, NordVPN data. A noteworthy aspect: RedLine also attempts to steal saved credit card info from browsers and perhaps software license keys from certain apps, essentially anything that could be monetized. All this stolen info is compiled into the stealer log package which the attacker can download from their panel. Because RedLine’s theft scope is so broad, a single RedLine infection can yield dozens of account credentials and personal data points from one computer.
Observed Abuse: RedLine’s footprint in real attacks is extensive. Prior to late 2024, it was arguably the most abused infostealer by cybercriminals, showing up in countless malware campaigns. For example, in 2023 a wave of phishing emails promised a free AI tool ChatGPT download the installers were bundled with RedLine, leading to many victims unwittingly sending their passwords to the attackers. RedLine has also been delivered through exploit kits in drive by download attacks, and via malicious advertisements that trick users into downloading fake software. On the underground markets, RedLine logs were a staple the infamous Genesis Market before its takedown and later Russian Market, 2easy, etc., were flooded with logs from RedLine Stealer during its peak years 2021–2022. This glut of stolen data directly enabled a surge in secondary attacks: reports note that initial access brokers used RedLine data for ransomware; one Register article highlighted a 60% jump in infostealer related activity feeding ransomware in 2023. In essence, many ransomware victims first had an employee’s VPN password stolen by RedLine, sold on a forum, and then purchased by a ransomware affiliate. Recognizing RedLine’s impact, international law enforcement launched Operation Magnus in late 2024, which targeted RedLine’s infrastructure. In October 2024, Dutch police, FBI, Europol and others took down RedLine’s backend servers and even arrested two individuals in Belgium associated with running it. This operation dismantled three primary RedLine servers and seized domains, temporarily disrupting the malware’s proliferation. ESET’s investigation in tandem with law enforcement also revealed that RedLine and a clone called META Stealer likely shared the same creator, suggesting one group was running multiple MaaS services. After the takedown, RedLine activity dipped, but it did not vanish entirely some affiliates may still be using older builds or variants, and other competitors rushed in to fill the void. Nevertheless, RedLine’s infostealer empire as ESET called it was responsible for a vast number of stolen credentials and subsequent breaches over the past few years.
Defensive Notes: Many organizations learned of a compromise only when third party services like HaveIBeenPwned or SpyCloud reported their users’ credentials in a RedLine log dump. To defend against RedLine, a multi pronged approach is needed. Endpoint security should be configured to detect RedLine’s behavior for example, the malware often injects into legitimate processes or uses known patterns to access browser databases. Monitoring for processes rapidly reading multiple credential stores or spawning system information commands can raise red flags. Given RedLine’s penchant for disguises Office document attachments dropping it, or fake software installers, email and content filtering is crucial: block or sandbox attachments like .exe, .scr, or macro enabled docs coming via email. Web filters can interdict access to known crack sites or newly registered domains hosting malware. Since RedLine steals valid credentials, implementing MFA on all remote access can blunt the damage even if an RDP password is stolen, an attacker might be stopped by a second factor though beware of cookie theft bypassing MFA. After the Operation Magnus takedown, defenders briefly had relief, but one should not be complacent RedLine variants or copycats like META Stealer may still circulate, and the data already stolen will remain in criminal hands. It’s wise to proactively search threat intel sources for your organization’s domain or email accounts appearing in stealer logs. If found, those accounts should be treated as compromised passwords changed, sessions revoked, further investigation for any sign of unauthorized access. Lastly, on user endpoints, disable saving passwords in browsers or encourage use of secure password managers this can reduce the free loot available if an infostealer like RedLine runs. RedLine taught the security community a costly lesson: a seemingly minor malware on a home user’s PC can lead to a major corporate breach if that user’s credentials are not protected.
Why It Matters: Raccoon Stealer has been a mainstay infostealer in the criminal toolkit, known for its low cost and high usage. It first emerged in 2019 as an inexpensive MaaS reportedly priced around $200 per month or $75 per week for subscribers. This affordability made it attractive to a wide swath of cybercriminals. Raccoon built a reputation for reliability and was quite prevalent in 2020–2021. In early 2022, the Raccoon operation went dark briefly the group claimed a lead developer died in the Ukraine conflict, but by mid 2022 a revived Raccoon Stealer v2 appeared, indicating development had resumed. This Raccoon 2.0 came with improvements rewritten in C, better performance and the actor behind it stayed active on forums, continually updating the malware. The return of Raccoon was notable security firms like Sekoia and Zscaler analyzed Raccoon v2 in 2022, highlighting its robust data stealing abilities passwords, cookies, crypto and changes like dropping the use of Telegram for C2. By 2023–2024, Raccoon was again widely used in the wild. While maybe not as dominant as Lumma or RedLine in sheer numbers, it held a strong presence and was often mentioned as a top 5 infostealer in circulation. Its importance also lies in representing the professionalization of infostealers Raccoon’s developers provided regular feature updates and customer support to criminals, effectively operating as a business. In summary, Raccoon matters because it’s one of the longstanding, stable infostealer families that continues to enable mass credential theft, and its resurgence demonstrated the resilience of the MaaS cybercrime model even after disruptions.
How It Works: Raccoon Stealer runs on Windows and follows a typical infostealer flow: when executed, it will deploy routines to scrape data from browsers and common apps. The malware has built in code to target dozens of applications. It hunts for browser databases grabbing login data, cookies, etc., searches for files associated with crypto wallets wallet.dat files, mnemonic phrases, and collects system info. A noteworthy aspect of Raccoon v2 the 2022+ version is that it was rewritten in C earlier was C++ and uses a multithreaded approach to speed up data collection. By stealing from multiple sources in parallel threads, it can exfiltrate everything quickly, reducing the window that defensive tools have to catch it in action. Raccoon v2 also simplified its C2 communication: the older version infamously used Telegram’s API to fetch a list of active C2 servers embedding Telegram channels as an updater mechanism, whereas v2 moved to a more direct method with hardcoded server IPs to retrieve C2 addresses. The stolen data is packaged often zipped and sent to the C2 server under the operator’s control. Raccoon, like others, historically does not establish persistence it aims to grab data during that session. However, it employs anti analysis techniques especially in the packed form to evade sandboxes and researchers: CloudSEK noted Raccoon samples using advanced packers to detect virtual machines and debuggers. This includes things like checking CPU timing RDTSC instruction to detect VMs and hiding its threads from debuggers. Such techniques make it harder for automated defenses to flag Raccoon immediately.
What Gets Stolen: Raccoon Stealer’s haul is very similar to RedLine’s in scope. It will steal login credentials and cookies from all popular browsers, including passwords and stored form data. It will gather any saved cryptocurrency wallet credentials or keys for instance, it targets files for wallets like Ethereum, Litecoin, Bitcoin Core, as well as browser extension wallets. It records some system information IP, locale, OS which may be included in the log for context. One unique twist: Raccoon, at least in older variants, would also dump a list of processes and possibly look for specific app files. The Cloudflare analysis of Lumma indicates many stealers produce similar outputs like Processes.txt, etc., so Raccoon likely does as well. Malpedia documentation confirms Raccoon collects passwords, cookies, autofill data, cryptowallet details, and system info like IP and geolocation. Essentially, if a piece of software has a saved password or session token on the system, Raccoon aims to get it. It may not explicitly keylog like Agent Tesla or Formbook families do, but with so much info stored in browsers nowadays, it doesn’t need to the saved data is enough. After stealing, Raccoon packages the data typically per victim. The group behind Raccoon also implemented some business rules common in Russian MaaS malware, such as not targeting CIS countries to steer clear of Russian domestic targets, which means Raccoon logs predominantly contain victims outside that region.
Observed Abuse: The trajectory of Raccoon’s use is interesting. Before its brief hiatus in early 2022, it was involved in numerous credential theft campaigns globally. After its comeback as Raccoon v2, it quickly picked up steam: by late 2022, some researchers dubbed a massive Raccoon campaign Recordbreaker for the sheer number of stolen records it produced. While exact numbers are hard to pin down, one report in 2022 suggested Raccoon infections led to millions of credentials stolen in just a few months, indicating its heavy use. Raccoon logs have been sold on the same markets as others; however, in 2023 a site called Raccoon Logs or similar emerged possibly run by the malware authors selling access to logs via a subscription, which suggests the operators themselves tried profiting directly from the data in addition to selling the malware. There were also instances of Raccoon being used in targeted attacks: for example, Raccoon was used to steal data from cryptocurrency services and high net worth individuals’ wallets, given its focus on crypto credentials. Raccoon has appeared in various threat reports for instance, it was mentioned alongside Lumma and RedLine as being disguised in fake invoice phishing waves in early 2024. That demonstrates how common it was in broad phishing campaigns. Furthermore, law enforcement in the US indicted a Raccoon Stealer administrator in 2022, which briefly disrupted it, but the fact that it’s still thriving in 2025 shows how resilient these operations can be with new personnel or rebranding after arrests. Overall, Raccoon logs continue to be a staple commodity for account takeover particularly consumer accounts, since many Raccoon victims are individuals and occasionally provide a foothold into companies when an employee’s personal device is compromised.
Defensive Notes: Defending against Raccoon is akin to defending against any modern infostealer it requires catching either the initial intrusion or the data exfiltration. Since Raccoon is often delivered via phishing or web downloads, email security and browser protections SmartScreen, Safe Browsing should be kept updated to block known malicious links. On endpoints, one can hunt for indicators of Raccoon activity such as the creation of suspicious ZIP files in temp directories, or processes accessing the AppData/Local/ paths where browser profiles reside. Network wise, Raccoon v2’s C2 traffic may use non standard ports or direct IP connections after it fetches config, which can stand out if monitored. Given Raccoon’s anti VM tricks, running malware analysis sandboxes in full CPU emulation mode or detecting RDTSC usage might help identify it. Another key defensive step is to limit the impact of stolen data: ensure employees don’t reuse passwords and implement password managers with strong master passwords so even if a password vault file is taken, it’s not trivial to crack. The usual advice to not store plain passwords in browsers applies encourage clearing saved credentials or using browser’s built in password manager only with an adequately strong OS account password on Windows, credentials are encrypted with the user’s login password, so having strong Windows account creds can help. Additionally, monitor underground sources for Raccoon logs containing your domain services exist that track millions of logs, and they can alert an organization if, say, an employee’s corporate email and password were in a Raccoon dump. Early notification can enable rapid incident response e.g. forced password resets, checking for any use of those creds by attackers. Finally, stay updated on threat intel: the Raccoon group frequently updates their malware, meaning IoCs like C2 domains/IPs change often. Subscription to threat feeds that include infostealer indicators can ensure your network blocklists and detection signatures keep pace.
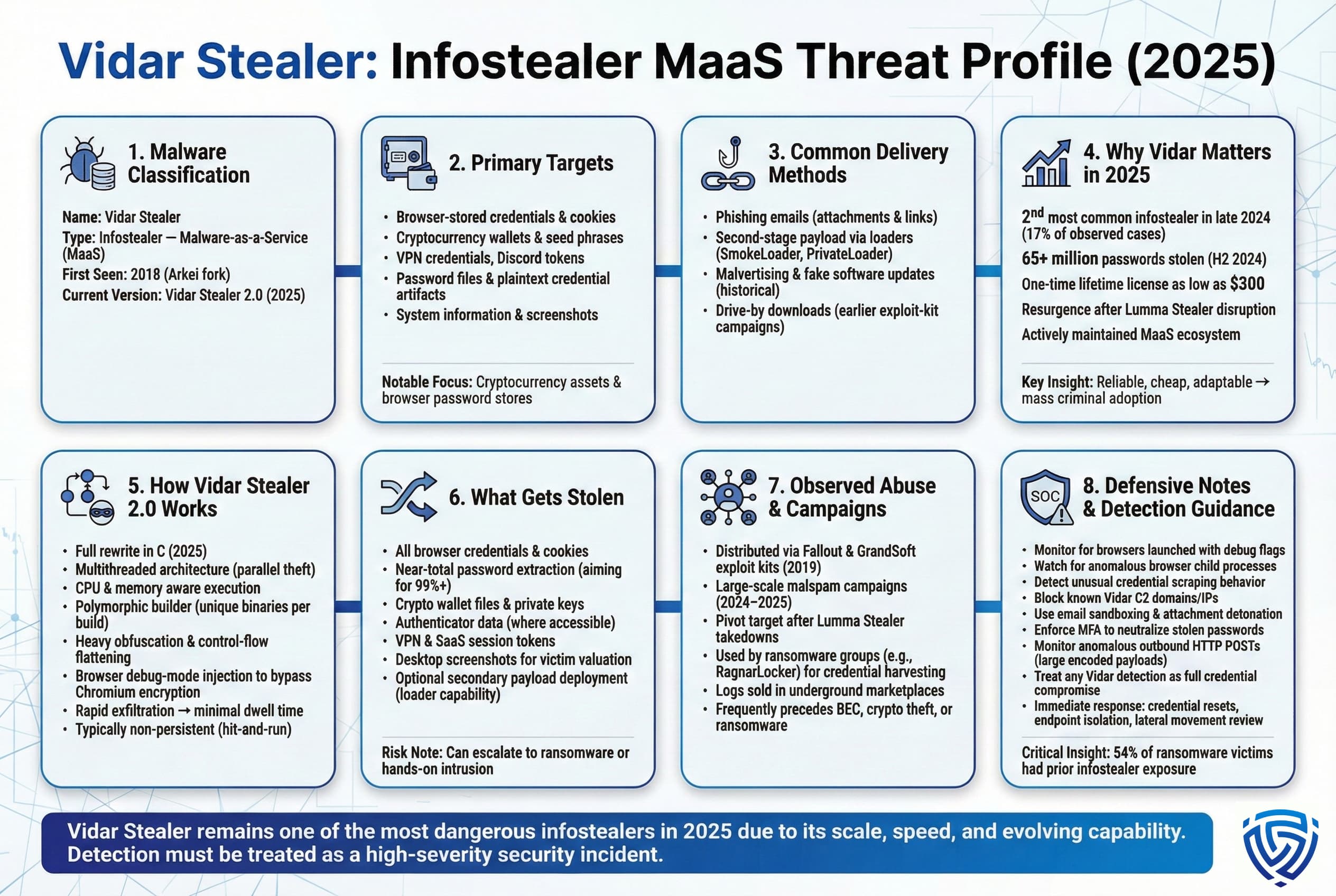
Why It Matters: Vidar is a veteran in the infostealer space active since 2018, it was originally a fork of the older Arkei stealer and quickly became one of the most popular infostealers in circulation. Over the years, Vidar maintained a reputation for reliability and was involved in numerous campaigns including being distributed by some exploit kits. By 2024, Vidar’s continued presence earned it a spot among the top infostealers, often mentioned alongside RedLine and Raccoon. In fact, data from KrakenLabs/Specops shows that in late 2024, Vidar was the second most common infostealer, seen in 17% of cases with over 65 million passwords stolen in H2 2024 alone. It rivaled Lumma Stealer and demonstrated significant impact. Vidar matters not only due to its prevalence but also its adaptability: in 2025, the malware underwent a major update labelled Vidar Stealer 2.0 that completely overhauled its code for greater efficiency and stealth. This evolution shows that its developers likely operating a MaaS service are intent on keeping Vidar competitive in the infostealer market. Notably, after Lumma Stealer’s operations were reportedly disrupted by law enforcement in early 2025 causing Lumma activity to dip, many cybercriminals pivoted back to Vidar as their tool of choice. With a one time purchase cost as low as $300 for lifetime use, Vidar is an attractive alternative for criminals seeking a stable infostealer platform. In summary, Vidar’s sustained popularity, huge data theft tallies, and ongoing upgrades firmly establish it as one of 2025’s top threats.
How It Works: The new Vidar Stealer 2.0, announced in October 2025, is a full rewrite in C older versions were in C++. It introduced a multithreading architecture: upon execution, Vidar determines the CPU core count and available memory of the victim machine, and then spawns multiple threads to steal from different sources concurrently. This means it can pilfer credentials, cookies, and files in parallel, greatly speeding up the theft process and shortening the time before exfiltration which in turn minimizes the window for detection and response. Vidar 2.0 also features a polymorphic builder that generates unique binaries for each build, giving each sample a distinct signature to evade antivirus detection. Additionally, the malware employs control flow flattening and other code obfuscation techniques to hinder reverse engineering. One particularly noteworthy advancement is how Vidar 2.0 tackles the encryption of browser password stores: modern Chromium based browsers encrypt saved passwords with an OS bound key and features like Chrome’s Enhanced Safe Storage protect them. Vidar now launches the browser in debug mode and injects code to extract decryption keys directly from memory, bypassing the browser’s normal encryption protections. This allows it to retrieve nearly all stored credentials even from up to date browsers a significant improvement in capability criminals behind a newer stealer called StealC claim many stealers only recovered ~43% of passwords due to not handling certain encryption, and new methods like Vidar’s aim for near total extraction. After data collection, Vidar exfiltrates to its C2. It likely compresses the loot and sends it, potentially using HTTP/S or a low level protocol. It’s sold as a MaaS, so different affiliates may have their own C2 servers. Like most stealers, Vidar doesn’t typically persist it tries to complete its mission quickly and exit. However, if deployed via a loader, sometimes the loader might reinfect or ensure persistence at a different layer.
What Gets Stolen: Vidar Stealer targets a comprehensive set of credentials and personal data. This includes all the web browser credentials and cookies, similar to others. It places a particular emphasis on cryptocurrency related data: any locally stored wallets files from wallet software directories, as well as text files that might contain seed phrases or private keys, are grabbed. The Cloudflare analysis of infostealers notes logs often have a Wallets folder, and Vidar certainly fills that when possible. Vidar also steals authenticator data if accessible for instance, it might try to snatch files from Authy or other 2FA apps on desktop, though 2FA apps are less common on PCs. It collects system info and might take a desktop screenshot to help the attacker gauge the environment if they see a corporate desktop background, that log becomes more valuable. Additionally, Vidar historically could download additional malware or files older versions of Vidar had a feature where the C2 could command it to download and execute a secondary payload, functioning as a loader. This means a Vidar infection could escalate if the attackers choose e.g., they might deploy ransomware as a second stage after stealing data. The presence of that capability underscores the threat: not only does Vidar steal data, but it could directly facilitate an attack if credentials found are immediately useful. With the 2025 update, the core data stolen remains largely the same, but the completeness of the theft is enhanced as mentioned, they aimed to extract 99%+ of credentials by bypassing protections. In essence, if you have it saved or cached on your PC, Vidar will try to get it from your browser passwords to your crypto keys to possibly your Discord tokens and VPN logins.
Observed Abuse: Vidar has been observed in numerous cyber incidents over the years. In earlier times 2019, it infamously was distributed via the Fallout and GrandSoft exploit kits, piggybacking on drive by downloads on compromised websites. In those cases, unwitting users visiting a site could get silently infected with Vidar if their software was unpatched. More recently, Vidar appears in many malspam campaigns. For example, in the second half of 2024, as Lumma Stealer saw big usage, Vidar was not far behind one report from late 2024 noted Vidar being used to steal 65 million passwords in just a few months, which implies a massive number of infections likely via large botnets of spam or other mechanisms. By 2025, after some law enforcement targeting of Lumma, Vidar saw an uptick: Trend Micro observed threat actors shifting from Lumma to Vidar and another stealer called StealC as Lumma’s operation was disrupted. This suggests many criminal affiliates simply switched to using Vidar, boosting its prevalence further. The quote from Trend Micro analysts in late 2025 was that as Lumma declines, security teams should anticipate increased Vidar 2.0 prevalence in campaigns through Q4 2025. Real world consequences of Vidar can be severe: credentials stolen by Vidar have led to everything from drained cryptocurrency accounts if a private wallet key is taken to compromised corporate email accounts used in business email compromise if an Office365 session token or password was taken. And since Vidar can act as a loader, some ransomware incidents likely began with Vidar infection followed by hands on keyboard attackers deploying encryption malware. We also see Vidar logs for sale on marketplaces, though specific Vidar shop might not exist like Lumma’s instead, their logs are just part of the general infostealer log dumps. One interesting case: in 2022, the RagnarLocker ransomware gang was observed deploying Vidar on some networks to gather credentials and facilitate their intrusion a crossover between crimeware and targeted ransomware operations. This highlights that even organized ransomware groups see value in infostealer malware as a tool for lateral movement or supplemental data theft.
Defensive Notes: The latest developments in Vidar multithreading, encryption bypass make it a formidable threat, but defenders can adapt accordingly. Endpoints should be updated with detection signatures for Vidar 2.0 the changes in how it behaves e.g., launching browsers in debug mode might themselves be detectable anomalies. For instance, a standard user machine normally wouldn’t launch Chrome with remote debugging flags; seeing that could indicate an infostealer trying to hook the browser. Monitoring for unusual child processes of browsers or the presence of known Vidar mutexes/indicators is useful. Network wise, blocking outbound traffic to known Vidar C2 infrastructure is a key threat since intel feeds from vendors like Trend Micro or Recorded Future can provide domains/IPs associated with current Vidar campaigns. Because Vidar often comes via email, strong email filtering and attachment sandboxing can catch it: an attachment that, when detonated, spawns a process that starts scraping credential stores should ring alarm bells. User education remains important: discourage users from downloading software from non official sources, which is a common way Vidar propagates. On the policy side, enforcing MFA on critical accounts and monitoring login attempts can limit damage stolen passwords alone should not grant access to sensitive systems if MFA stands in the way though stolen cookies could, so consider device/session monitoring too. Given Vidar’s focus on speed, one defensive angle is to detect data exfiltration channels for example, if Vidar sends logs via HTTP, anomaly detection might catch a client PC suddenly posting large base64 blobs to an odd domain. Incorporating threat hunting queries for infostealer patterns like looking for use of mshta.exe or PowerShell spawning unexpectedly, which was seen in some Vidar infections can help find early signs of compromise. Finally, ensure that incident response plans include steps for infostealer driven incidents: if an endpoint is found infected, assume all its credentials are compromised and initiate credential resets and scans for any lateral movement. With the knowledge that infostealers often precede bigger breaches, remember that 54% of ransomware victims had infostealer logs with their credentials, treating a detected infostealer infection as a serious incident can prevent escalation to a full blown breach.
Despite the variety of infostealer families, they often rely on a core set of infection vectors to enter systems. Recognizing these common delivery mechanisms can help organizations harden their defenses:
In summary, infostealers largely rely on social engineering tricking the user to run something they shouldn’t. Whether it’s a phish email, a tempting free download, or a spoofed update alert, the initial execution is the critical point. To combat this, organizations should employ a combination of secure email gateways, web filtering to block known malicious sites and ads, application control to prevent unauthorized executables from running, and user education. By reducing the chances of a user running an unknown program, you significantly reduce infostealer incursions. Importantly, because home and personal devices are often targeted e.g. an employee’s home PC might get a stealer via a game crack, extending some protections to those environments through DNS filtering, antivirus, or zero trust access that limits what stolen credentials can do is worth considering in a work from home era.
The aggressive theft by infostealers is ultimately driven by profit and stealer logs have become extremely valuable commodities for attackers for several reasons:
In essence, stealer logs are valuable because they collapse the attack chain. Instead of having to fish for credentials with targeted efforts, threat actors can simply buy a ready made kit of credentials and sessions. It’s fast, cheap, and scalable. They enable attackers to operate with the legitimate keys to the kingdom, often flying under the radar because they’re logging in with valid credentials rather than deploying noisy exploits or malware. This shift is why many security experts say we’ve moved from an era of break in to log in for threat actors. Why hack a door when the keys are readily for sale? Defenders must accordingly adjust, placing greater emphasis on credential abuse detection and zero trust assumptions, because infostealers have flooded the landscape with stolen auth artifacts.
Infostealers cast a wide net, but certain groups and environments are especially at risk due to the data they handle or the security challenges they face:
In summary, the infostealer wave puts virtually everyone at some risk given how one in five individuals was affected in 2023, but remote/BYOD workers, resource constrained SMBs, active crypto holders, and cloud centric orgs have a particularly large bullseye. Recognizing if you fall in these categories should prompt extra defensive measures. For example, if you’re a small business relying on Google Workspace, you might enforce security keys U2F for MFA to mitigate stolen passwords, since you know an infostealer could steal the password but not the physical key. Or if you’re a remote worker, you ensure your personal laptop has company EDR agent and you separate personal browsing from work tasks maybe using a dedicated browser for work accounts. These targeted precautions can significantly reduce risk for those most exposed.
Infostealers present a multi dimensional threat, but there are concrete steps security teams can take to mitigate the risk and impact. Here are key defensive takeaways:
By executing on these defensive measures, security teams can significantly reduce the risk posed by infostealers. It’s about assuming compromise since it’s nearly impossible to stop 100% of malware and making sure that a stolen password or two doesn’t easily implode your network. In the current landscape, where infostealers are rampant, organizations that prioritize identity security, endpoint vigilance, and user education will fare far better against this silent but potent threat.
The threat landscape in 2025 underscores a sobering reality: while ransomware and headline grabbing hacks continue, the quiet theft of credentials via infostealer malware has become the engine driving much of the underground economy. Infostealers like Lumma, RedLine, Raccoon, and Vidar have enabled cybercriminals to steal hundreds of millions of credentials and monetized them through a mature ecosystem of log markets and access brokers. The result is an epidemic of account takeovers and an easy path for attackers to infiltrate organizations by simply reusing stolen logins. As defenders, we must adapt to this threat first perspective recognizing that preventing and detecting infostealer activity is now just as critical as patching servers or filtering ransomware. This means doubling down on identity security strong MFA, credential hygiene, dark web monitoring and endpoint visibility, as well as proactive user awareness.
Encouragingly, a threat informed defense can yield results. Many infostealer techniques, while stealthy, leave trails that diligent monitoring can catch unusual PowerShell executions, strange outbound connections, abnormal data access patterns. By focusing on those weak signals and hardening the practices that infostealers exploit like unmanaged password storage and lax BYOD controls, security teams can shrink the attack surface. The underground may continue to innovate with new stealers and tactics as seen with Vidar 2.0’s emergence but an organization that emphasizes zero trust, never trusting a single credential and rapid incident response can blunt their impact. The days of assuming a user login is safe are over; now, every authentication attempt must be scrutinized for risk.
In conclusion, infostealers will likely remain a favored tool of cybercriminals as long as passwords and cookies hold value. They fuel everything from petty fraud to major breaches. The onus is on defenders to remove that fuel from the fire: protect the credentials, and you cut off the lifeblood of many attacks. As we move forward, adopting passwordless technologies and robust identity verification will be key strategies to make infostealer logs far less valuable. Until then, vigilance and layered defenses are paramount. By understanding the threat of the malware families, their modus operandi, and their role in the cybercrime supply chain we empower ourselves to anticipate the attackers’ moves and stay one step ahead. In the cat and mouse game of cybersecurity, infostealers have had a big run, but armed with knowledge and resilient practices, we can deny them the easy victories and better safeguard our organizations’ most critical asset: our credentials.
About the Author
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us