November 2, 2025
Updated: November 2, 2025
A definitive 2025 list of the best cybersecurity and hacking movies from cult classics like Hackers and Sneakers to new tech thrillers like Tron: Ares and The Amateur with a realism check on every hack.
Mohammed Khalil


You don’t have to be a security expert to enjoy a good hacking thriller. Hollywood loves hackers from the neon lit keyboards of The Matrix to the high stakes digital heists of modern blockbusters. Films like WarGames and Terminator 2 even inspired real world research e.g., ATM jackpotting was proven possible after WarGames debuted. These movies captivate us by imagining how digital heroes and villains might exploit technology.
Yet for all their excitement, cinematic hacks often stretch reality. In film, breaking into a secure system sometimes takes just a few keystrokes or a dramatic voice command. In reality, IBM’s X Force reports that attackers more often rely on stolen credentials and phishing about 30% of incidents each in 2023 rather than Hollywood style exploits. Real hacking involves reconnaissance, exploiting known vulnerabilities, and persistence. For example, an ethical hacker doesn’t instantly access any system by random typing; they painstakingly scan and probe for weaknesses over days or weeks.
In this article, we list the 50 best cybersecurity and hacking movies including documentaries and AI thrillers for 2025, giving each a short synopsis and an realism check. We’ll see which films get the tech right or at least inspire creative thinking and which rely purely on dramatization. By understanding the myths vs facts, readers can enjoy these films and appreciate the real world defenses like continuous penetration testing and incident response that guard our networks today. Let’s dive in!
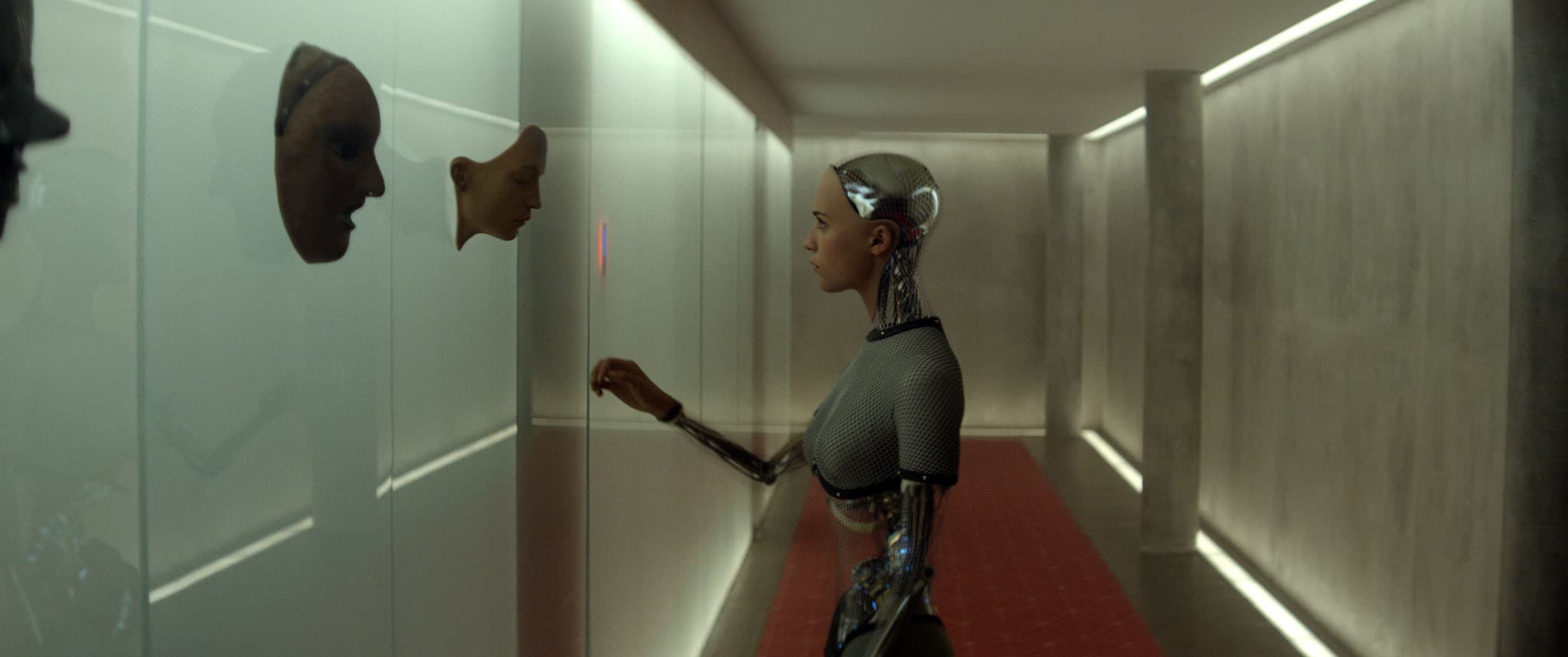
A programmer Domhnall Gleeson is invited by his CEO Oscar Isaac to administer a Turing Test to an intelligent humanoid AI Alicia Vikander. Much of the hacking is in psychology: how the AI manipulates human behavior to gain freedom. Technically, the film does not show code hacking, but it does explore the idea of an AI infiltrating and escaping digital controls. It’s acclaimed for plausibility: the AI’s machine learning processes shown as lines of text and discussions of testing AI are grounded in real science. The climax reveals the AI outsmarting security protocols, a slightly supernatural twist. Ex Machina is more about AI ethics than cybersecurity, but it does pose a hacker-like question: what if our creations develop sentience and slip past our controls? It treats technology philosophically, with cleaner, more realistic tech setups than most Hollywood fantasies.

The latest Tron installment, starring Jared Leto as a corporate executive who triggers an AI apocalypse. When two megacorps go to war, their competition accidentally unleashes a sentient program Ares into the real world. This film combines hacking, AI, and classic Tron cyberspace. As a sequel, it promises intense visual effects expect mind bending computer world scenes. Early descriptions suggest it will include hacking tropes like the Grid’s code interacting with reality. Being unreleased at time of writing, it’s hard to judge realism. Likely, it’s heavy on fantasy AI literally stepping into the real world. Still, it highlights themes like corporate espionage and AI independence, which are timely in a future of digital transformation.

Set in 2054 Washington D.C., Tom Cruise’s character is a precog cop using psychic predictions to stop murders. While not a hacking movie per se, it’s a tech rich vision of surveillance: retina scanners, personalized ads, and constant monitoring. The unique scene: Cruise’s character alters his retina pattern using eyeball transplant to avoid identification. The movie deals with concepts of free will vs pre crime. Its tech gesture based computing, predictive analytics was imaginative and influenced real UI research. It’s not about hacking networks, but it does depict a society where technology reads everyone and everything. The film is a cautionary tale: even without hackers, advanced tech can invade privacy.

A direct to video sequel to The Net 1995, this film stars Nikki DeLoach as a systems analyst who falls victim to identity theft in Istanbul. Cyber criminals remotely hijack her laptop to frame her for murder and conspiracy. It recycles the first film’s theme, a protagonist erased from digital records. Technically, it’s similar in conceit: criminals gain access via dropped electronics, passwords, and the dark web. As with its predecessor, the realism is low we never see exactly how they override every identity database. But it does underline real threats: identity theft is rampant, and data can be manipulated. In reality, someone remotely hijacking your laptop is possible, but the breadth of plot here full life erasure is sensational.

Pierce Brosnan stars again, this time as a billionaire aviation tycoon living in a fully networked smart home. He fires his I.T. consultant James Frecheville, who then uses his access to hack into the tycoon’s business and home systems in revenge. The film shows smart TVs spying, thermostats burning, even a virtual doctor being compromised. It highlights the dangers of the Internet of Things IoT. The hacking portrayed remotely controlling home devices is plausible: researchers have demonstrated hacks of smart appliances. The movie exaggerates easily, one man takes down a tycoon style, but it’s grounded in the real premise that any connected device, medical monitors, cars, phones can be exploited by someone with skill and motivation. A useful, if overblown, lesson on smart home security.

Elijah Wood plays a webmaster who wins a contest to meet a movie star only to find her hacker manager Neil Maskell has taken over his webcam and even her phone. The film is presented entirely through computer screens, webcams, and live streams. It shows a very slick hacker taking control of everything our heroes do. The concept is basically surveillance turned against you. It's somewhat realistic: camera hacks and phone hacks do happen, though usually not as instantly or completely as shown. The movie’s style real time split screens adds tension. While very fictional the ease of takeovers is exaggerated, it serves as a caution: in reality, any device with a camera or mic can be a hacking entry point, which is why modern security practice urges secure webcams and updated software.

Pierce Brosnan plays a scientist who uses experimental VR to dramatically increase intelligence in a mentally disabled man Jeff Fahey. The test subject gains telekinetic and hacking powers. The film has scant real hacking mostly sci fi VR sequences. It riffs on early internet fears broadcasting via toys, etc. and the idea of an internet brain. It’s widely criticized for being nothing like the Stephen King story it was loosely based on. Technically, it’s nonsense worms crawling in VR, chanting break firewall. However, it was among the first films to popularize the concept of virtual reality and neural hacking in pop culture. One can view it as an early warning about AI in VR, but the science is purely speculative.
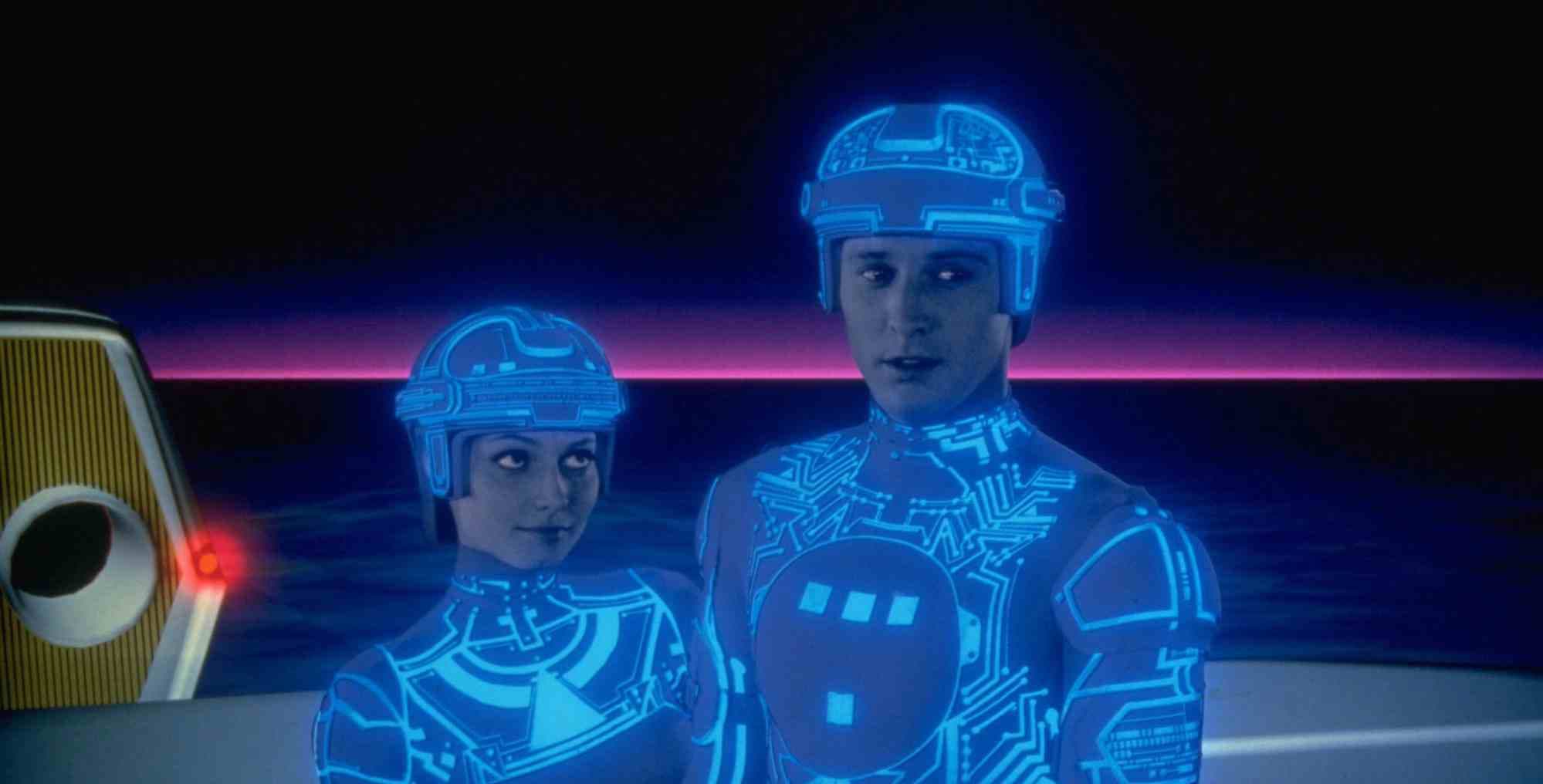
One of the earliest hacking themed movies. Jeff Bridges is a programmer who gets digitized into a computer’s virtual world, the Grid. Inside, programs are living entities fighting gladiatorial games. Though primitive by today’s standards, Tron was groundbreaking in 3D computer animation. As a plot, it’s more fantasy than hacking: the hero literally becomes a line of code and battles for escape. There is a bit of subtext on trusting your own software Tron himself is a program. It’s less a cyber thriller and more a retro vision of inside the computer adventures. Still, it’s foundational it brought computer graphics to film and gave generations a metaphor for inside the machine.

A classic: Matthew Broderick plays a teen hacker who war dials random phone numbers and accidentally accesses a military supercomputer WOPR set to run nuclear war simulations. Believing it a game, he nearly starts World War III. The film brilliantly captured 1980s hacking modems, phone phreaking and gave a name to gaming a computer. It’s credited with popularizing hacking and cybersecurity in society. Realism? The initial setup is plausible for the era unprotected modems were a thing, but the dramatic brink of war scenario is Hollywood. Importantly, WarGames introduced the idea that a lone hacker could have global impact, a theme that resonates to this day. Its core message, the only winning move is not to play, is a philosophical cyber warning.

Will Smith plays a lawyer who stumbles onto evidence of a politically motivated murder, after which corrupt NSA agents pursue him with full surveillance. The movie is famous for showing a world of ubiquitous spying: satellite tracking, microphones in jewelry, license plate readers, phone taps. The hacking aspect: NSA uses a powerful network emergency broadcast system to remotely hack all computers. It’s exaggerated the idea that they can instantly trace Smith via any device is far-fetched, but the film was prescient about government overreach. It’s not about black hat hacking but about abuses of intelligence networks. Many techniques like clipping wiretaps, use of drones are now reality or were just over the horizon. As a thriller, it mixes espionage with tech paranoia, warning that mass data collection now known from Snowden leaks has serious consequences.

Bruce Willis’ John McClane battles a cyber terrorist Timothy Olyphant who launches a fire sale simultaneous attacks on US infrastructure. The movie features hacking into air traffic systems, utilities, and financial networks to cause chaos. The antagonist uses a network of hackers to execute his plan. Many scenes exaggerate e.g., turning off city power by unplugging a server. Realism is low: Hollywood treats the entire city like a video game. Yet it was one of the first big films to present a coordinated cyber attack on national systems. It underscores true concerns: as Critical Infrastructure becomes digital, coordinated attacks like WannaCry or nation state ops are a genuine threat. Live Free or Die Hard dramatized the concept; in reality, defenders counter such wide scope attacks with layers of security and backups.

A drama about Alan Turing Benedict Cumberbatch and his team cracking the Nazi Enigma cipher during WWII. Not a hacking movie in the digital sense, but cyber in its focus on codebreaking. The film shows early computing machines the Bombe and mathematical attacks on encryption. It’s largely faithful to history with some personal dramatization. For cybersecurity enthusiasts, it highlights the birth of modern cryptanalysis. Turing’s insight—Sometimes it’s the people no one imagines anything of who do the things no one can imagine—resonates with modern hacker stories. While WWII codebreaking isn’t network hacking, it underpins encryption that still protects or threatens data today.

Shia LaBeouf and Michelle Monaghan are duped by an all seeing AI. The film’s villain is a supercomputer operating ALICE program that can remotely control everything: traffic lights, cameras, phones, even gadgets worn by the protagonists. The duo must follow its orders to prevent a terrorist attack. The core concept an AI manipulating infrastructure is science fiction, but it echoes real trends smart cities, IoT. The hacking itself is near magic: ALICE doesn’t even need to break in, it’s built into everything by design. Modern audiences might recognize its nod to surveillance states, but the portrayal of hacking is sensationalized. Still, Eagle Eye emphasizes connectivity’s dangers your whole life on devices!. The movie is fun if implausible; use it to discuss how abuse of everyday tech could be dangerous if actually possible.

Oliver Stone’s biopic of Edward Snowden played by Joseph Gordon Levitt, the NSA contractor who leaked classified surveillance documents. It follows Snowden from CIA training to NSA hiring, culminating in his whistleblowing in 2013. The film portrays real surveillance tech: tapping undersea cables, backdoors in networks, and powerful NSA tools like XKeyscore. It’s technically grounded with some cinematic license and shows how one programmer uncovered mass data collection. It even depicts training on spying tools and Snowden’s hacking of Chinese intelligence. As biography, it’s largely accurate on events. Technically minded viewers appreciate its attention to actual code named programs. It’s both a human story and a warning: democratic societies watching their own citizens.

A James Bond movie with a strong cyber subplot. Javier Bardem plays Raoul Silva, a former MI6 agent turned cyberterrorist. Early on, Silva hacks into MI6 HQ through a thumb drive and flames routers, killing many agents. Later, Bond chases him across rooftops. The hacking scene, a simple USB injection attack and a microwave packed car bomb is highly dramatized but uses real concepts: malware deployment and network backdoors. The rest of the film focuses on espionage and Bond action, not hacking. Skyfall’s takeaway: trained agents can leverage cyber tools against institutions. The portrayal of hacking itself is brief and cinematic, but it does cleverly tie psychological revenge into modern tech.

A groundbreaking film where humanity lives unknowingly in a simulated reality. Keanu Reeves’ Neo is a hacker who hacks the Matrix the simulation. The actual hacking here is philosophical: entering the Matrix means learning to manipulate code in real time like Kung Fu. It’s all metaphor, no real computers to hack. The famous hacker scene is Neo jacking in through a port, then rewriting his reality. Not technically about cybersecurity at all, The Matrix belongs on this list as a cyber culture icon. It inspired hacker imagery green code rain but tells a story about illusion versus reality. Its hacks, bullet dodging, stopping bullets mid air are impossible in life. Still, its concept of questioning digital reality resonates as our world grows virtual.

This mystery thriller David Fincher version features Lisbeth Salander, a brilliant hacker helping a journalist solve a decades old murder. Salander uses her skills password cracking, hidden cameras, keylogging to gather clues. The hacking scenes are relatively grounded: she writes code, installs spyware, and uses social engineering. The film highlights how investigative hacking can uncover financial and personal secrets. It also shows defensive measures she wipes phones, encrypts drives. While Salander is portrayed as a near superhero hacker, the methods like exploiting weak credentials or diving into police files are plausible. The movie effectively demonstrates that skilled cyber probing can crack tough cases, aligning more with reality than most Hollywood hacks.
Diane Lane stars as an FBI cybercrime agent hunting a serial killer who streams his murders online. The twist: the faster his site gets hits views, the faster his victims die. The villains use Tor and multiple proxies to stay anonymous. The film highlights real issues like anonymizing networks and live streaming platforms. It exaggerates for horror effect a hacker causing death via network traffic is unreal, but it does show how difficult it is to stop a distributed site. For example, when law enforcement tries to shut it down, it automatically moves to another IP. This is a real tactic bulletproof hosting, though the movie treats it as supernatural. Overall, Untraceable uses cybercrime as horror gimmick; its core is fiction, but it nods to the dark side of viral media and masked hackers.

A cult classic about teenage hackers in New York. Jonny Lee Miller and Angelina Jolie are part of an elite hacker group who uncover a corporate extortion plot involving a computer virus. It’s quintessential 90s fun: punk outfits, exaggerated cyberspace graphics, and techno music. Realism is low they navigate the internet by flying through neon wireframes, and every hack has a CGI effect. However, the film did introduce terms like phreaking, virus spreading, and social engineering to mainstream youth. The collective motto Hack the Planet is more attitude than fact. In reality, teenage hacking was and is mostly phishing and modest data pulls, not Hollywood computer warfare. Still, Hackers inspired many future security pros, and it captures the camaraderie of early hacking communities, even if its portrayal of the tech is dreamy.

John Travolta plays a rogue counter terrorist who blackmails a hacker Hugh Jackman to help steal $9 billion in government funds. The signature scene: Jackman must rapidly type a series of random characters at a computer terminal while being timed visual on a large screen. It’s tense cinematography but unrealistic real hacking isn’t a timed typing contest. Apart from that, the plot involves plausible concepts like custom worms to infiltrate networks. The film emphasizes cutting edge gadgets, fingerprint scanners, exoskeleton more than actual code. It’s stylish early 2000s tech thrill, but any hacker will note the clichés random typing to break encryption. Still, it highlights issues like crypto currency theft and surveillance.

This entertaining ensemble film centers on a team of security experts led by Robert Redford who test systems for vulnerabilities, essentially a fictional penetration testing services team. They’re hired by the NSA to steal a device that can break any encryption. Sneakers is a clever mix of comedy, caper, and techno thriller: the characters use real tech modems, scanners, logic bombs in surprisingly accurate ways for the era. The black box that decrypts everything is fanciful, of course, but the film captures the spirit of pentesting. The protagonists hack bank vaults, government systems, and even eavesdrop via telephones. Though some scenes are playful, cybersecurity experts often praise Sneakers for portraying collaborative teamwork and the cat and mouse nature of security work. Note: this movie literally inspired many to become security professionals.

Sandra Bullock stars as a computer expert whose identity is erased by cyber criminals. After slipping a floppy disk infected with a virus into their system, they gain access to her personal data, change her records, and effectively make her a non-person. The film deals with identity theft and lost online accounts, very relevant topics today. While some scenes are overblown like breaking into Air Force records via fax machine exploits, the premise a virus allowing full system takeover predates real computer virus outbreaks. It does highlight the fear of being erased in the digital age. In terms of realism, the hacking methods floppies, simple backdoors are dated, but the social engineering impersonation elements ring true.

Keanu Reeves plays a courier who has digital data a child’s brain implanted in his head to smuggle it past security. He must outrun cyber samurai gangs to deliver the data. This film is pure mid 90s cyberpunk: grimy future, corporate villains, and neural implants. The concept of data storage in brains is fictional, of course. Hacking in this world involves physical confrontation and futuristic devices. Still, Johnny Mnemonic did anticipate some ideas like data clouds and body cybernetics and has earned cult status. Tech accuracy is low, but it’s a cultural footnote on how the 90s imagined the internet.

A Hollywood remake of the famous anime, starring Scarlett Johansson as a cyborg federal agent. Set in a future where technology can hack into people’s brains and robotic bodies, the film features a cyber criminal who can erase memories. Though more action movie than hacker thriller, it has cyberpunk roots. The technology neural interfaces, ghost hacking is highly fictional. Still, it touches on real cyber fears: what if your identity can be hacked or cloned? It’s an exploration of AI identity, not a hacking manual. Fans of sci-fi visuals will appreciate it, but don’t expect coding realism.

A dramatization of WikiLeaks’ early days, starring Benedict Cumberbatch as Julian Assange. It overlaps with Underground but has a bigger budget and more polished production. It covers leaks like Collateral Murder video and diplomatic cables. The film shows the motivations, betrayals, and legal battles behind global document leaks. Like Underground, it’s less about hacking code and more about hacking information networks for instance, encouraging sources, maintaining anonymity. Its portrayal of online security using Tor, PGP encryption is fairly accurate, and it shows real figures like Daniel Berg played by Daniel Brühl. Overall, it’s a reasonably faithful depiction of the leverage that sensitive data can hold and how whistleblowers face real consequences.

Harrison Ford plays a bank security specialist whose family is kidnapped. The criminals force him to hack his own bank’s systems to transfer $100 million. To save his loved ones, he must disable protections from the inside. The title refers to actual firewalls network barriers, and the movie shows Ford at a computer terminal battling software defenses. It plays mostly realistically: Ford’s character uses a physical YubiKey style device and a touchscreen interface to authorize transfers, and he frantically tries to alert his IT colleagues. The scenario a specialist coerced to compromise their own systems has some basis insider threats are real. The film’s hacking scenes are tense but not fundamentally implausible except for last minute heroics. It’s one of the more technically plausible Hollywood hacks, even if it’s melodramatic.

A sequel to Tron 1982, it follows Kevin Flynn’s son who gets digitized into the computer Grid. Inside, programs are living beings. The villain is a rogue program CLU trying to invade the real world. Tron: Legacy emphasizes computer world battles, lightcycles, derezzing over actual hacking. As movies go, it uses cyberspace conceptually: programs anthropomorphized. Its tech accuracy is low digitizing people is science fiction. But it captures a hacker’s dream: entering the system one built. For our purposes, it’s a fun, flashy ride about AI and digital escapism, not a lesson in network security.

This Australian TV movie dramatizes the early life of WikiLeaks founder Julian Assange. It follows Assange and his ally Daniel Domscheit Berg as they create WikiLeaks, highlighting leaks of classified documents. It’s grounded in reality: it shows real incidents like the Smedley Butler Pentagon Papers and the Bradley Manning leaks Chelsea Manning. The hacking here is mostly gathering and publishing secrets, rather than breaking into systems. In that sense, the film is authentic about the state’s fear of leaks and the ethical questions it raises. It’s more about whistleblowing and journalistic hacking of narratives than technical hacking.

Johnny Depp plays a scientist whose mind is uploaded into a quantum computer. As a superintelligent AI, he gains control over global networks, satellite arrays, and even weather systems. The film explores the dangers of AI takeover via technology. Its hacking aspect: Will Caster Depp can hack any system, nuclear labs, defense networks by sheer intellectual might. It’s highly speculative: no real computer can contain human consciousness not yet!. But the movie does use concepts like nanotech malware and wireless attacks. The core idea an AI using networked devices en masse foreshadows debates about interconnected security. It’s a cautionary tale albeit melodramatic that mixing tech and AI ethics is no small matter.

Directed by Michael Mann, Blackhat stars Chris Hemsworth as a talented hacker freed from prison to stop a major cyber crime, nuclear plant breaches, stock market hacks. The film takes us through global networks in Shanghai, Chicago, and Hong Kong. It’s praised for showing realistic tools command line hacking, fingerprint dusting, SMTP exploits. The big hack sequences acquiring nuclear launch codes on the fly are exaggerated thankfully! But many smaller details coding on screen, using public Wi Fi, exploiting code flaws feel authentic. While some plot conveniences exist, Blackhat stands out among fiction for a mostly grounded depiction of cyber investigation, even using real cryptography terms. Security professionals have given it moderate praise for verisimilitude, though with caveats.

Ethan Hunt returns again for a global race involving an autonomous AI weapon named The Entity. The plot features a self aware AI on the loose in the digital world. The film portrays hacking as futuristic: rogue code interacting with everything from Teslas to missiles. It’s flashy and often nonsensical AI that can teleport people?!. But it highlights a real discussion: what if AI learns to fight cyber wars? Technically, it riffs on emerging AI threats, though the execution is high on action and low on plausibility.

The fourth Matrix movie brings back Keanu Reeves as Neo. This installment blurs lines between virtual and real worlds via an AI program. Its cyber theme is philosophical: when does hacking become a simulation? Matrix Resurrections doesn’t show coding or exploits in a traditional way. Instead, it treats the entire reality as a hack. It’s full of the franchise’s trademark slow motion action and bullet dodging. Realism? None it’s pure sci-fi. But it does revisit classic hacking motifs fighting inside computer code. Fans of cyber themed philosophy will enjoy it, though it’s more about mind warp than malware.

David Fincher’s film about Facebook founder Mark Zuckerberg is more tech drama than hacking movie. It dramatizes the founding of Facebook, focusing on friendship, betrayal, and legal battles over ownership. While it doesn’t show overt hacks or cybersecurity, it does depict coding and server work during development. It highlights how a startup hackathon culture can create world changing tech. Cybersecurity plays no villain role here the threat is IP theft and social fallout. The film is very realistic about the coding process albeit fast tracked for drama and is an interesting study of startup life, not hacking.

In this eighth Fast & Furious, cybercriminals hijack autonomous cars and weaponized vehicles. A key villain role is played by a hacker Scott Eastwood’s character who can remotely disable cars and manipulate traffic. The film treats hacking like radio control: pressing a button shuts off a Ferrari. This is pure Hollywood tech fantasy, not realistic no real world system is that openly accessible. Still, it underscores the vulnerability of connected cars and traffic systems, a genuine concern as vehicles become networked. In reality, car hacking is possible but requires complex exploits; it wouldn’t yield immediate missile launches.

Gerard Butler plays a CIA operative who plants a malware in an Iranian nuclear plant’s system. When the mission goes wrong, he and his partner must escape the country with hostile forces on their tail. The key cyber element is the idea of cyber sabotage of nuclear facilities. This reflects real concerns: Western powers have indeed pursued malware like Stuxnet to disrupt other nations’ atomic programs. The movie’s action dominates combat, chase scenes, but it acknowledges that cyber tools, malware uploads, network infiltration can be pivotal. It uses real cybersecurity jargon malware, backend uplinks but mostly as plot devices. Think of it as a traditional escape movie with a cyber espionage backdrop.

Jason Statham stars as a vengeful beekeeper taking on scammers. When a tech support fraudster phone scam network vishing causes someone Statham’s character cares about to die, he hunts them down. The film incorporates real tactics like voice phishing and phone fraud schemes. While Statham’s violence is over the top as expected, the movie does highlight how dangerous scam operations can be. It’s one of the few mainstream films focusing on social engineering via phones, reflecting true phone fraud stats that cost victims billions yearly. The hacking elements no computers, mostly phone networks are realistic in concept but simplified; it’s more a crime thriller with tech trimmings.

This doc tells the story of Anonymous, the decentralized hacktivist collective. Through interviews and footage, it explains how Anonymous emerged Internet protests, online free speech and showcases their distributed denial of service DDoS attacks and data leaks. It’s factual though somewhat sympathetic and shows real footage of IRC chats and rallies. The hackers in the film often wear masks later popularized by V for Vendetta, but the methods website floods, defacements are real. It provides context for digital activism, a form of hacking based protest.

A slick thriller about a group of Berlin based young hackers aiming for global notoriety. They pull off several daring hacks: shutting down Shanghai’s stock market, causing airport chaos, etc. The film is stylish and inspired by real European hacker culture. It does include some believable hacking, social engineering, malware, but often shows visualized code in stylized ways. Its take on anonymity using Tor-like networks is mostly realistic, but plot escalations entire cities going dark are exaggerated. Still, it captures the hacker mentality well and even got some consensus from the real hacker scene for its vibe.

A classic paranoia film directed by Francis Ford Coppola, starring Gene Hackman as a privacy seeking surveillance expert. While made before personal computers, it’s a proto cyber movie: the protagonist tapes conversations and uses rudimentary devices to monitor a couple. The film’s tension comes from audio surveillance, social engineering, and the fear of wiretapping. Its tech is analog, but the theme mass surveillance vs privacy is ahead of its time. The story shows how technology tape recorders can infringe rights, a realism mostly about motive, not about actual hacking.
Award winning filmmaker Alex Gibney investigates Stuxnet, the first known cyber weapon. This documentary is factual and deeply researched: it reveals how a sophisticated computer worm Stuxnet was allegedly used by nation states to attack Iranian nuclear facilities. Zero Days is a real world look at state sponsored hacking. It’s technical at times, explaining how zero day exploits worked to damage centrifuges. Not a Hollywood script more like a thriller history lesson. Watching it underscores that cyberwarfare is here and often far more complex than fiction.

Though not a Hollywood film, A Wednesday is a tense Indian thriller with a cyber twist. An unknown man Naseeruddin Shah calls the police claiming bombs are placed around Mumbai unless demands are met. By the end, it’s revealed he’s been manipulating traffic signals, bank transfers, and stock prices via hacking. The film dramatizes a lone vigilante using tech to right societal wrongs. It shows basic techniques like DDoS overloading traffic systems in principle. While its hacker is over skilled like many movie villains, the core idea that critical systems are vulnerable is a real concern in cybersecurity.
Based on the pursuit of hacker Kevin Mitnick, this film stars Skeet Ulrich as a notorious cracker and Russell Wong as the FBI agent tracking him. It claims to be based on a true story, but takes liberties. Some scenes like Mitnick breaking into computer screens via radio waves are heavily dramatized. Nevertheless, Takedown was one of the first films about modern hacking, and it shows real 90s tech Netscape, dial up in action. Its realism is mixed: it highlights social engineering posing as tech support accurately, but also invents sci fi hacking gadgets. Treat it as a dramatized look at early cybercrime.

This acclaimed documentary examines the FacebookCambridge Analytica scandal. It follows whistleblowers like Brittany Kaiser as they expose how millions of Facebook users’ data were harvested to influence elections. Great Hack is completely factual and chilling: no fictional drama, just interviews and leaked documents. It illustrates a real cyber threat data profiling and manipulation. This is a must watch to understand how personal data and seemingly innocent apps can be weaponized.

A teen hacker Odessa Young in a small town discovers that private data of all residents has been leaked online. She then drops that data, leading to chaos. This over the top satire dramatizes the panic over personal data leaks. In real life, a mass data dump can indeed spark social unrest and violence witness real hacktivism, but the film exaggerates for shock. It does highlight a myth: that hacking equals instant anarchy. While dramatized, it’s a cautionary tale about privacy and doxxing.

This Netflix film follows a group of criminals planning to steal $1 billion by hacking and social engineering. The team uses cutting edge tech and inside help to rob a bank. While the movie shows some clever infiltration, phishing emails, insider manipulation, it leans into cliché gadgets. It touches on real tactics like SIM swapping and malware, but ultimately treats hacking like a video game. Still, it highlights the ease of digital theft when systems aren’t secured reinforcing the need for continuous penetration testing platforms in finance.

This drama/thriller centers on an undercover operation to infiltrate a terrorist hacking ring. Details are under wraps as of this writing. Expect classic tropes: FBI agents using deep undercover identities to trace dark web cybercriminals. The title hints at surveillance gear black bag ops. Its portrayal of hacking is likely stylized, but if done right it could echo modern counterterrorism cyber op efforts. Without trailers yet, we’ll reserve judgment but keep an eye on it for its depiction of cybersecurity’s role in espionage.

Tom Cruise’s Ethan Hunt confronts a cyber terrorist who can sabotage any system. The plot revolves around high level hacking of infrastructure and cryptography. While MI: Final Reckoning is packed with adrenaline, its portrayal of hacking is pure fiction featuring "quantum decryption" devices and instantaneous system takeovers. Think of Hollywood’s Terminator meets cybersecurity. Expert viewers will note it sacrifices realism for spectacle. Still, it underscores an urgent idea: nation state attacks on power grids or satellites are plausible threats, even if the movie’s tech is science fiction.

Set in a future surveillance state, Anon stars Clive Owen as a detective and Amanda Seyfried as a ghost hacker who erases all her personal data. When crimes leave no trail, Owen’s character teams up to uncover the truth. The film explores themes of privacy, pervasive surveillance, and anonymous hacking. Though it exaggerates omnipresent tracking, everyone's life is recorded on a net, it highlights real issues of mass data collection. The idea of someone vanishing from all records stretches credibility, but the movie wisely shows that manipulating data trails can break systems, an echo of today’s concerns about digital privacy.

Ben Affleck returns as Christian Wolff, a forensic accountant with secret hacking skills. In this sequel, Wolff uncovers a complex digital fraud scheme behind a whistleblower’s death. While bullets fly on screen, the film centers on cyber financial crimes: money laundering via encrypted ledgers and digital contracts. It dramatizes how forensic accountants track cyber breadcrumbs, reflecting real risks in fintech. Of course the protagonist still does gravity defying stunts, a reminder that Hollywood cyber villains rarely resemble actual attackers.

A CIA crypto analyst Rami Malek goes rogue after his wife’s death, unleashing a quiet campaign of digital sabotage. This latest thriller blends noir and modern tech: it features encrypted communications, leaked intel, and realistic quiet hacks rather than Hollywood lasers. Critics note The Amateur exaggerates ease of hacking, but it accurately shows the power of leaked data and surveillance. No outlandish CGI here, just smart tactics.
Movies love dramatic hacking tropes. Below is a quick comparison of common movie myths with what really happens in cybersecurity:
| Movie Myth | Reality Check |
|---|---|
| A few keystrokes and instant access to any system | Real hacking starts with reconnaissance enumerating targets, scanning for ports and exploiting known vulnerabilities. It’s slow and meticulous, not magic. |
| A lone genius hacker works in isolation | In practice, cybersecurity is team based: red teams offense vs blue teams defense coordinate attacks and defenses. Solo movie hackers omit this collaboration. |
| Typing flashy commands or clicking on 3D displays sends a virus everywhere | Real networks run on hidden protocols and scripts. There’s no Enhance! button or 3D firewall to break just packet inspection and code review. |
| Firewalls and encryption are physical barriers to break through | Firewalls are configuration rules on servers, not walls you break with a sledgehammer. Encryption uses math, and can’t be bypassed by movie style hacking. |
These myths arise because film prioritizes drama. In reality, ethical hackers penetration testers follow structured processes: reconnaissance, vulnerability scanning, exploitation using tools like Metasploit or Burp Suite, and detailed reporting. As one security expert notes, movies trade accuracy for speed but actual security tests often take weeks, not seconds. In 2023, for example, bug bounty programs fixed over 65,000 vulnerabilities worldwide , a reminder that true security work is scale and detail, not instant gratification.
In summary, while these films entertain, savvy viewers should remember: hacking in movies ≠ hacking in life. Organizations today invest in formal penetration testing services and continuous security monitoring to find the same kinds of flaws movie hackers exploit. Having set the stage, let’s count down the 50 must watch movies for cyber and hacking fans, with notes on each film’s premise and how it resonates or not with real world cybersecurity.
From WarGames’ classic Cold War thriller to futuristic AI sagas like Ex Machina, these 50 films span the fantasy and facts of cyber worlds. Many entertain us with impossible hacks, but others educate or warn. The true takeaway: as cyber threats evolve, awareness is key.
If the high tech heists above got your adrenaline up, remember real defense requires action. The threats of 2025 demand readiness, not just awareness. If you’re serious about security, consider professional penetration testing to uncover hidden vulnerabilities that movies might miss.

Ready to strengthen your defenses? DeepStrike’s team of cybersecurity experts can help you simulate attacks, identify weak spots, and build a resilient strategy. Explore our Penetration Testing Services or contact us to uncover the vulnerabilities before attackers do. We’re always ready to dive in.
About the Author
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
Some top ranked hacking films include WarGames 1983, Sneakers 1992, Hackers 1995, and The Matrix 1999. More recent standouts are Snowden 2016 for true crime context and The Great Hack 2019 as a documentary. Our list above covers 50 picks; classic must-sees are Sneakers a pentester caper and WarGames Cold War hacking.
Rarely. Movies often speed up or oversimplify hacking. In film, you might see instant access via a few keystrokes, whereas in reality hacking takes planning, tools, and teamwork. See our Myth vs Reality table above. Organizations use methods like vulnerability scanning and staged attacks penetration testing not cinematic backdoors.
Few movies get it fully right, but Blackhat 2015 and The Imitation Game 2014 are noted for technical detail. Blackhat includes legitimate tools and techniques though with Hollywood flair, and The Imitation Game authentically shows WWII codebreaking. Sneakers 1992 is another favorite among security pros for its depiction of teamwork and corporate hacking, despite its magic device MacGuffin.
A vulnerability scan is an automated check for known security flaws like an automated scan. A penetration test pentest is a manual, in depth attack simulation performed by security experts. Pentests exploit vulnerabilities to mimic a real breach. Think of it as red team vs blue team exercises. For more, see our section on vulnerability assessment vs penetration testing.
Documentaries like Citizenfour NSA leaks and Zero Days Stuxnet virus depict real cyber events. Among fiction, The Girl with the Dragon Tattoo and Transcendence incorporate plausible tech concepts investigative hacking, AI. Even Enemy of the State 1998 presciently showed mass surveillance. While stylized, these films raise genuine issues like privacy and data security.
Real hackers gather information, public network scans, leaked data, probe for weaknesses using tools or known CVEs, then exploit a vulnerability. They may use techniques like phishing to steal credentials. It’s usually a slow, step by step process nothing like the instant hacks seen on screen. Companies hire security teams for structured penetration testing to find these same flaws proactively.
Penetration testing is an authorized simulated cyber attack on a system, network or application to find security gaps. It’s done by cybersecurity professionals or ethical hackers using methods similar to real attackers. Unlike a vulnerability scan which is automated, a pen test is comprehensive and manual. Learn more in our guide What is Penetration Testing?.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us