October 23, 2025
Updated: October 23, 2025
Learn what quishing is, how QR code phishing works, and how to stop it. Real examples, step by step defenses, and a quick checklist for teams
Khaled Hassan

QR codes were designed to make life easier. Point your camera, open a page, pay a bill, join Wi-Fi, or pull up a menu. That speed is exactly why attackers love them. QR code phishing, also known as quishing, turns a harmless square into a shortcut to credential theft, payment fraud, and device compromise. You scan because the code looks official. A logo sits nearby. The promise is simple, pay here or track your parcel. In seconds, you are typing a password or card number on a page that looks right but is not.
Quishing succeeds because it moves the moment of decision away from your protected desktop to your phone. Your email gateway may block suspicious links in messages on your laptop. It will not stop you from scanning a printed sticker on a parking meter or an image in a forwarded email that hides its URL inside a QR pattern. On a small mobile screen, domains truncate, brand marks are tiny, and subtle typos are tougher to spot. Attackers design their pages for this reality. They keep the flow fast and the pressure high.
This guide explains how quishing works, why it is rising, and how to stop it with practical controls. We walk through the attacker playbook from code placement to credential capture. You will learn how to recognize red flags in the moment, even on a phone. We map the defenses that matter most, from QR-aware email filtering to phishing resistant MFA. We also include training scenarios you can copy, with normal versus vulnerable examples that make the risk concrete for your team.
If you run security, you will find a prioritized checklist and a buyer’s guide for tools that understand QR threats. If you manage facilities, you will get a physical inspection routine that catches tampered signage before it hurts staff or visitors. If you are a daily user, you will leave with simple habits that keep scans safe. Pause. Preview the domain. Proceed only if it checks out. Prefer official apps for payments and deliveries.
Qhishing
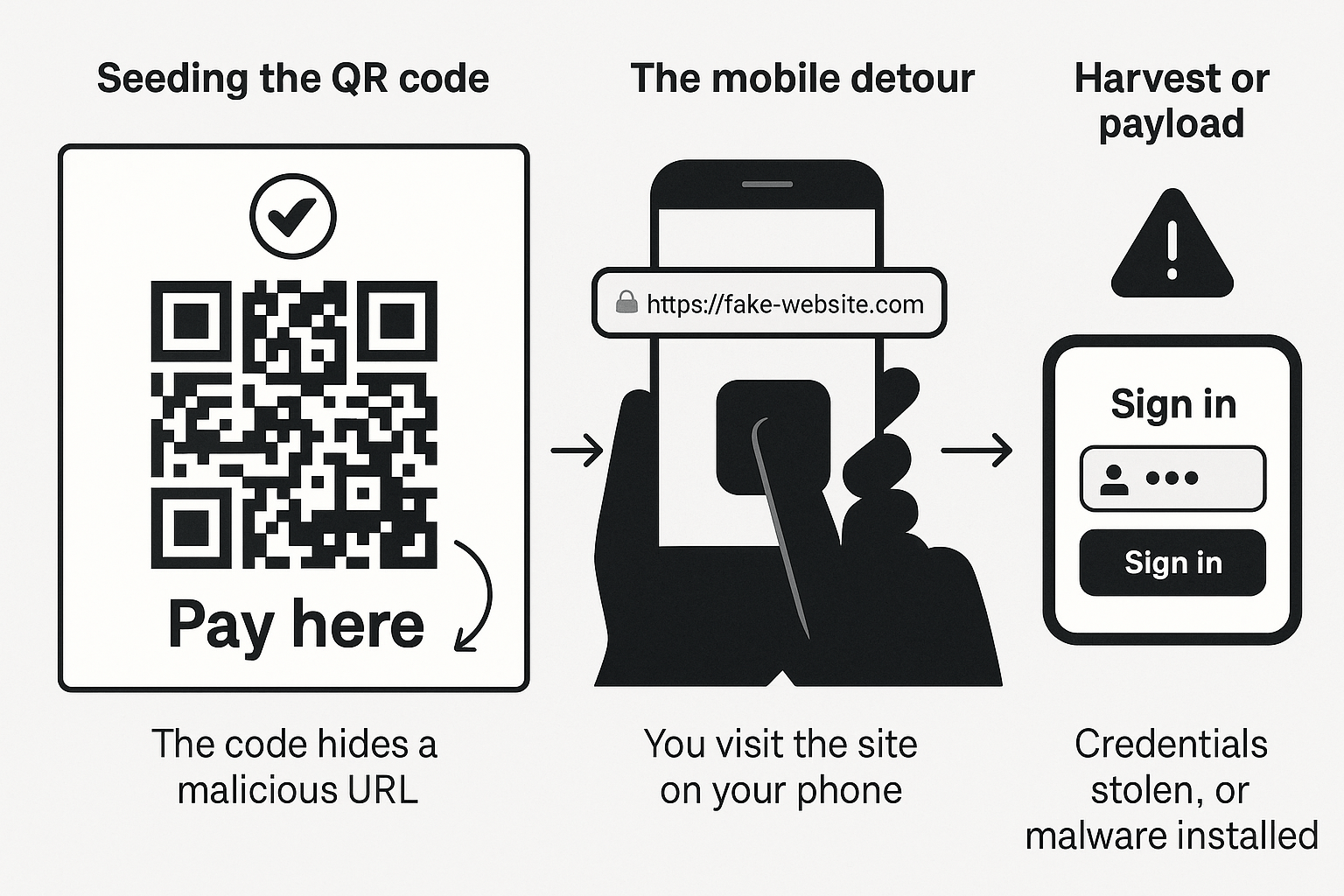
Definition: Quishing is phishing that uses a QR code to lure you to a spoofed website or malicious app. Attackers print or embed a code on emails, posters, invoices, parking meters, delivery notes, or packaging. You scan, land on a fake site, and enter credentials or payment details. Because the scan happens on your phone, outside many enterprise defenses, detection is harder. Microsoft and industry reports have tracked a steady rise in QR code phishing, including large waves delivered by email images that carry QR codes instead of clickable links.
Attackers place a code on a surface people trust, or inside an email image that looks like a legitimate notice. Examples include parking meters, restaurant tables, shipping labels, service tickets, gift cards, and corporate posters in lobbies. Recent cases show fake parking codes that led drivers to phishing payment pages. The Guardian
What you see: A clean code, a brand logo, and a short call to action like “Pay here,” “Track your parcel,” or “Verify account.”
What is happening: The code hides a URL that looks close to a real brand. Some codes route through a link shortener or multiple redirects before the final page.
You scan with your camera or a reader. Your phone opens the site in a small browser tab. On mobile, URL bars truncate, and brand cues are smaller, so warning signs are easy to miss. Microsoft researchers have shown attackers intentionally move the decision point to phones to bypass desktop filters. Microsoft
Real-world data points: FBI advisories describe QR-led scams tied to delivery and prize themes. UK reporting shows thousands affected by “pay to park” quishing, including large individual losses.
Tip: If a code is on a meter, poster, or table, verify the URL on the vendor’s official page or app store listing before you pay.
r1nggo-pay[.]info or a short link that lands on a domain unrelated to the operator. The page asks for full card details and security code, then sets up recurring charges. These patterns have been observed in multiple UK incidents in 2024 and 2025. The Guardiancarrier.com/track.Scenario 1: Parking
https://pay.ringo.co.uk/parking/zone/12345https://r1nggo-pay.co/zone/12345?session=... → card form that asks for CVV.Scenario 2: Delivery
https://www.dhl.com/track?AWB=...https://dhl-track-support.com/verify → asks for email password to “release parcel.”Scenario 3: Corporate survey
https://forms.microsoft.com/r/...https://microsoft-forms.work-survey.net → SSO look-alike.Use this trio in tabletop drills. Show screenshots of the mobile URL bar and make the team identify the tell.
Quishing shifts phishing from the inbox to your phone, using the trust of physical spaces and the constraints of small screens. Defenses work best when you treat QR codes as a first-class threat. Add QR-aware email filtering, run realistic QR simulations, move to phishing-resistant MFA, and audit public signage. If you make these steps routine, QR codes become less of a trap and more of a tool.
Is scanning any QR code safe?
No. You cannot see the destination without scanning. Treat public codes as untrusted, verify the domain, and prefer official apps for payments.
Can email security stop quishing?
Yes, but only if it extracts URLs from QR images and analyzes the destination. Choose gateways that support this and pair with user training.
What if I already scanned and entered data?
Change the related passwords, revoke sessions, notify your bank if you entered card details, and report the incident. In the US, file at IC3.
Are QR codes themselves malicious?
The code is just a pointer, the risk comes from where it points. Attackers rely on trust in physical spaces and small mobile screens.
Which MFA stops quishing?
Use phishing-resistant MFA like passkeys or security keys. Even if a fake page captures a password, the attacker cannot easily replay a hardware-bound credential.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us