What's OAuth?
OAuth is an open-standard authorization protocol or framework that provides applications the ability for “secure designated access.” For example, you can tell Facebook that it’s OK for deepstrike.io to access your profile or post updates to your timeline without having to give DeepStrike your Facebook password. OAuth can also be used for authentication; for example, to log into your application using social sign-in feature [ Google, Facebook, Microsoft, etc ].
Overview of the OAuth 2.0 protocol
OAuth is a complex security protocol, with different components sending pieces of information to each other in a precise balance akin to a technological dance. There are two major steps to an OAuth transaction: issuing a token and using a token. The token represents the access that's been delegated to the client and it plays a central role in every part of OAuth 2.0
The OAuth ecosystem consists of actors and components that communicate with each other.
OAuth Actors: [ Clients, Authorization server, Protected resources, and resource owners ]
- An OAuth client is an application that makes requests to access protected resources on behalf of a user or on its own behalf. OAuth clients can be anything from a web server application, a browser-based application, or a mobile app.
Note: The client doesn't have to understand the token nor should it ever need to inspect the tokens contents. Instead, the client uses the token as an opaque string.
- An OAuth protected resource is any data or service that requires controlled access, typically hosted on a resource server that enforces access controls via OAuth tokens.
Resource Server: This is the server hosting the protected resources. It is responsible for handling requests to access these resources, validating access tokens provided by clients, and serving the resources to clients based on the access granted by these tokens.
- In the context of OAuth, the resource owner is an entity that can grant access to a protected resource. Typically, this is the user who owns the data or has control over it.
- The OAuth Authorization Server is a crucial component in the OAuth 2.0 protocol, the authorization server authenticates the resource owner and client, provides mechanisms for allowing resource owners to authorize clients and issues tokens to the client.
OAuth components: [ Tokens, Scopes, and Authorization grants ]
- Access Token: An OAuth access token, some times known as just a token in casual reference, it is a piece of data generated by the Authorization server and used by a client to make authenticated requests to a resource server. The token indicates the rights that's a client has been delegated by the resource owner, allowing the client to access protected resources without exposing the resource owner’s credentials.
- Scope: An OAuth scope is a representation of a set of rights at a protected resource. Scopes are an important mechanism for limiting the access granted to a client.
- Authorization grants: OAuth authorization grants are mechanisms in OAuth 2.0, a protocol for authorization, that enable a client application to obtain limited access to a user's protected resources hosted by a resource server. These grants are essentially credentials that represent the user's consent for the client to access these resources. The type of grant chosen depends on the client type, whether the client is confidential (capable of maintaining the secrecy of credentials) or public, and the user experience desired.
OAuth Vulnerabilities
There are vulnerabilities that can occur in the clients as well as the other OAuth actors, including the OAuth tokens. An example of the vulnerabilities that can occur on the client side is: OAuth Hijacking via unverified id_token
Now, we're going to talk about OAuth Hijacking via the "Login with Google One Tap sign-in" feature and how to detect it.
At first; what is GOOGLE One Tap Sign-In?
Google One Tap is a new feature that allows users to create an account or log in to the website with a single click. It is also known as YOLO (You Only Login Once). The login widget appears as a popup, and it will prompt the users to sign in or sign up with the existing Google account.
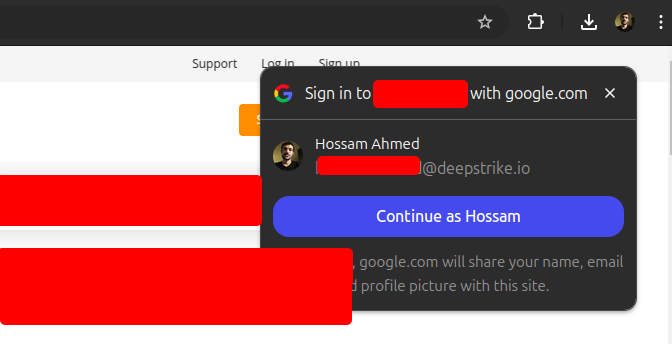
Google one tap login
How Does GOOGLE One Tap Sign-In Work?
- A JavaScript library is included on your website. HTML or JavaScript is used to customize the look and feel of the personalized button and, on one tap, control the automatic sign-in and sign-out behaviors.
- The Users who are signing in for the first time are prompted for consent to share their Google Account profile information. After providing the consent, a JSON Web Token (JWT) credential containing the user’s name, email, and profile picture is shared using a callback handler.
- Now you can use the ID token to create a new account on your platform or allow the verified user to continue using your site.
In the server-side, how does the developer deal with the ID token in order to verify if this token is for a person who is already registered in the application or not?
At first, what’s inside in the ID token Payload?
- iss (issuer): Issuer of the JWT (Google)
- sub (subject): Subject of the JWT (the user)
- aud (audience): Recipient for which the JWT is intended (The Client)
- exp (expiration time): Time after which the JWT expires
- iat (issued at time): Time at which the JWT was issued; can be used to determine age of the JWT
- jti (JWT ID): Unique identifier; can be used to prevent the JWT from being replayed (allows a token to be used only once)
Now, Validation of an ID token in the back-end requires several steps:
- Verify that the ID token is properly signed by the issuer.
- Verify that the value of the iss claim in the ID token is equal to https://accounts.google.com or accounts.google.com
- Verify that the value of the aud claim in the ID token is equal to your app's client ID.
- Verify that the expiry time (exp claim) of the ID token has not passed.
- The last step is to check whether this user has an account in the application or not, this is done through one of the following values: sub claim or email claim.
- If the “email” value or the “sub” value is linked to an account in the application, the session or JWT is returned in the response according to the nature of the authentication mechanism in the application. If not, he call the registration feature to create an account based on “email” claim.
- But, what if the developer doesn’t check the value of the audience for any reason?
- In this case, the ID token from another client can be used to login or create a new account in the target application; it does not need to be specific to the client that refers to the application we are using. However, the ID token must have been signed by Google and must not have exceeded its expiration date.
Attack scenario:
An attacker can create a client on the "Google Developers Platform" and configure Google One Tap Sign-In in their application to exploit a misconfiguration, such as failing to check the "audience" value. This can lead to account takeovers if the user has registered with both the vulnerable application and the attacker’s application through Google One Tap Sign-In.
Finally
To defend against OAuth hijacking, implement these key security measures:
- Verify Token Signature – Ensure the ID token is signed by Google using its public keys.
- Check Issuer (iss) – Accept only tokens from https://accounts.google.com.
- Validate Audience (aud) – The token must match your app’s Client ID.
- Enforce Expiry (exp) – Reject expired tokens to prevent replay attacks.
- User Verification – Match sub or email to existing users in your database.
- Monitor & Log Requests – Detect anomalies in OAuth authentication attempts.
- Restrict OAuth Clients – Allow only trusted apps to register and use OAuth.
- Secure Backend Validation – Always verify ID tokens on the server before granting access.