The Most Notorious Hackers in 2025
In 2025, the digital battleground has grown fiercer. Sophisticated threat actors are breaking through protections once considered robust, leaving entire industries reeling. Who are the most notorious hackers pushing the limits of cyber risk this year? Which groups and individuals dominate headlines, and why should security teams care?
In this article, you will:
- Learn the identities, histories, and tactics of top hackers of 2025
- Examine case studies from major breaches.
- Understand evolving trends in hacking techniques.
- See insights on how organizations can defend themselves.
This deep dive into the most notorious hackers in 2025 explores how they operate, their motivations, and what makes them uniquely dangerous today.
What Does “Notorious Hacker” Mean in 2025?
A “notorious hacker” in 2025 typically exhibits:
- High-impact breaches: Theft or exfiltration of data on the scale of millions
- Innovation in attack techniques: Use of AI, zero-days, supply chain exploits
- Political or geopolitical alignment: or ransomware-for-profit motives
- Media visibility and attribution : Their hacks are publicly acknowledged
According to the 2025 Global Threat Report, social engineering, cloud intrusions, and malware-free techniques are surging in frequency and impact.
Top Hacker Groups & Individuals of 2025

From North Korea to the Middle East, hacker groups shaped 2025’s cyber landscape.
Lazarus Group / TraderTraitor
- A state-linked North Korean actor. In February 2025, Lazarus orchestrated a \$1.5 billion Ethereum heist from Bybit.
- The subset known as TraderTraitor targets Web3 developers with spear-phishing and custom malware.
- The incident blurred the lines between state-sponsored operations and direct financial motivation.
IntelBroker
- Also known as Kai Logan West, IntelBroker was arrested in 2025 for operating BreachForums.
- Responsible for over 80 corporate and government data leaks.
- His case underscores how blockchain forensics and digital footprint tracing make anonymity harder.
Scattered Spider
- A criminal group specializing in social engineering and SIM-swap attacks targeting cloud services.
- In 2025, they claimed responsibility for stealing nearly 1 billion Salesforce client records.
- Merging with ShinyHunters, they represent a hybrid model of extortion and data brokerage.
Predatory Sparrow
- A pro-Israel group likely tied to state entities.
- In June 2025, they targeted Iran’s Bank Sepah and Nobitex exchange, stealing \$90 million.
- Their operations mix hacktivism with cyberwarfare tactics.
Dark Storm Team
- A pro-Palestinian actor collective known for DDoS and ransomware attacks.
- Claimed the March 2025 outage of X (Twitter).
- Frequently targets government and financial infrastructure.
Anonymous Sudan
- Active since 2023, responsible for thousands of DDoS campaigns on hospitals, media outlets, and agencies.
- U.S. indictments in 2024 disrupted their botnet infrastructure, but successors remain active.
- Motivated by disruption, not profit, their attacks still cause operational and reputational damage.
Case Studies: When Hackers Hit Big

Lazarus Group’s Bybit heist in 2025 remains one of the biggest crypto thefts in history
Bybit Crypto Heist
In Feb 2025, Lazarus exploited a third-party signing flaw in Bybit’s cold wallet infrastructure, stealing \$1.5 billion in Ethereum. The breach triggered a rapid market reaction and forced new crypto compliance checks.
Salesforce Client Data Theft
Scattered Spider’s phishing and SIM-swapping campaign compromised Salesforce clients rather than the platform itself, highlighting the fragility of vendor ecosystems.
Kering Luxury Data Leak
Hackers linked to ShinyHunters breached Kering, owner of Gucci and Balenciaga. Although financial data was spared, client contact information was exposed, damaging brand reputation globally.
“Signalgate” Incident
In March 2025, confidential U.S. military data was accidentally leaked via misused Signal apps. This showed how human error and governance lapses can rival even sophisticated attacks.
2025 Trends in Hacking: What’s Changed?
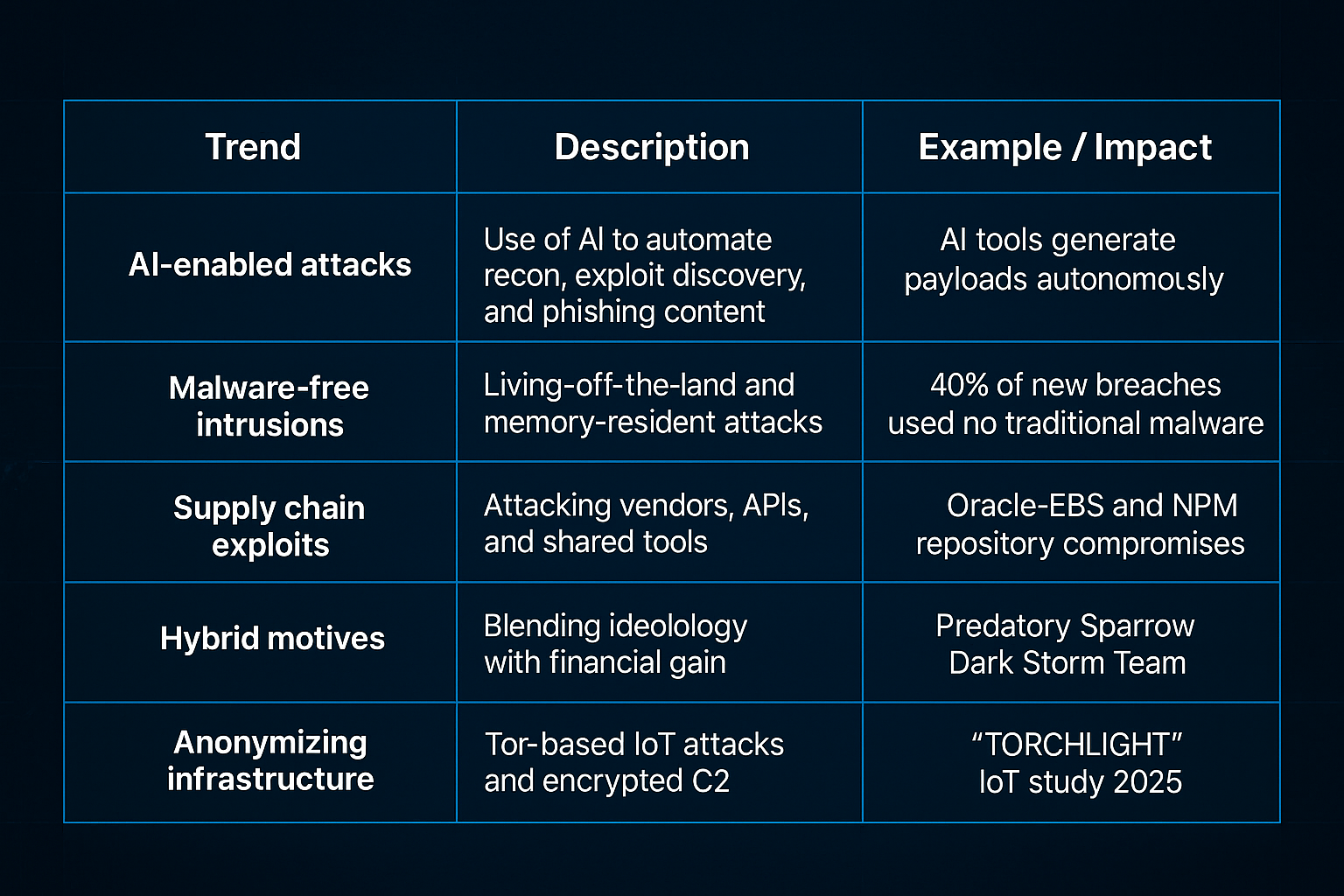
Key hacking trends shaping 2025, from AI-powered attacks to supply chain exploits and anonymizing infrastructure
Why These Hackers Matter
- Massive scale: Their operations affect millions.
- Technical sophistication: They pioneer techniques others replicate.
- Cross-sector risk: From fintech to government, no domain is safe.
- Regulatory consequences: Each major breach reshapes privacy and security law.
- Psychological impact: Fear and misinformation are now deliberate attack vectors.
How to Defend Against These Threats
- Adopt Zero Trust: Never assume internal trust boundaries are safe.
- Strengthen identity controls: Enforce MFA, detect SIM-swap attempts.
- Assess your vendors: Continuous security reviews of integrations and SaaS tools.
- Invest in threat hunting: Move beyond passive detection.
- Run tabletop exercises: Rehearse ransomware and data-leak response.
- Leverage AI for defense: Apply anomaly detection and behavioral analytics.
Featured Snippet Answer
The most notorious hackers of 2025 include: Lazarus Group (TraderTraitor), IntelBroker, Scattered Spider, Predatory Sparrow, Dark Storm Team, and Anonymous Sudan ,responsible for the most disruptive and financially devastating cyberattacks this year.
FAQs
- Are all of these hackers criminals?
Not always. Some, like Lazarus and Predatory Sparrow, are tied to state actors or cyberwarfare units. - How are hackers identified?
Through blockchain analysis, infrastructure reuse, leaked communication logs, and human errors in operational security. - Can small businesses be targets?
Yes. Most large breaches start with compromised partners or small vendors in the supply chain. - Have any been arrested?
IntelBroker was apprehended in 2025. Others operate from jurisdictions with limited extradition. - How does AI influence modern hacking?
AI accelerates reconnaissance, exploit generation, and phishing, but defenders also deploy AI for detection and incident response. - What’s next for cybercrime after 2025?
Expect more autonomous AI-powered attacks, targeted supply chain compromises, and new hybrid political-financial motives.




