October 24, 2025
Updated: October 24, 2025
The latest crypto hacking incidents statistics 2025. Verified figures on losses, attack types, regions, and trends. Clear insights and charts to guide risk decisions.
Mohammed Khalil

Crypto security remains a top priority in 2025. Capital flows have returned to digital assets, new users are entering the market, and attackers are adapting. The first half of the year already surpassed 2024 by total value stolen. Multiple firms report a sharp spike in large incidents, led by exchange and wallet compromises. Chainalysis noted more than $2.17 billion stolen by mid-July 2025, already exceeding all of 2024. Kroll’s threat lens placed first-half losses at about $1.93 billion, while CertiK tallied nearly $2.5 billion for H1 and highlighted wallet takeovers as the biggest driver. SlowMist tracked 121 security incidents and about $2.37 billion in losses in H1, a rise in value even as incident counts fell compared to last year.
The quarter-by-quarter pattern also changed. Q1 2025 was the worst quarter on record for crypto hacks, with Immunefi estimating $1.64 billion lost. Losses then eased through Q2 and Q3, though September spiked with a record count of million-dollar events. This points to better controls in some areas and continued pressure on high-value targets.
If you build, invest, or trade, you need reliable numbers to calibrate risk. Below is a concise snapshot followed by a detailed list. Here are the most important crypto hacking incidents statistics for 2025.
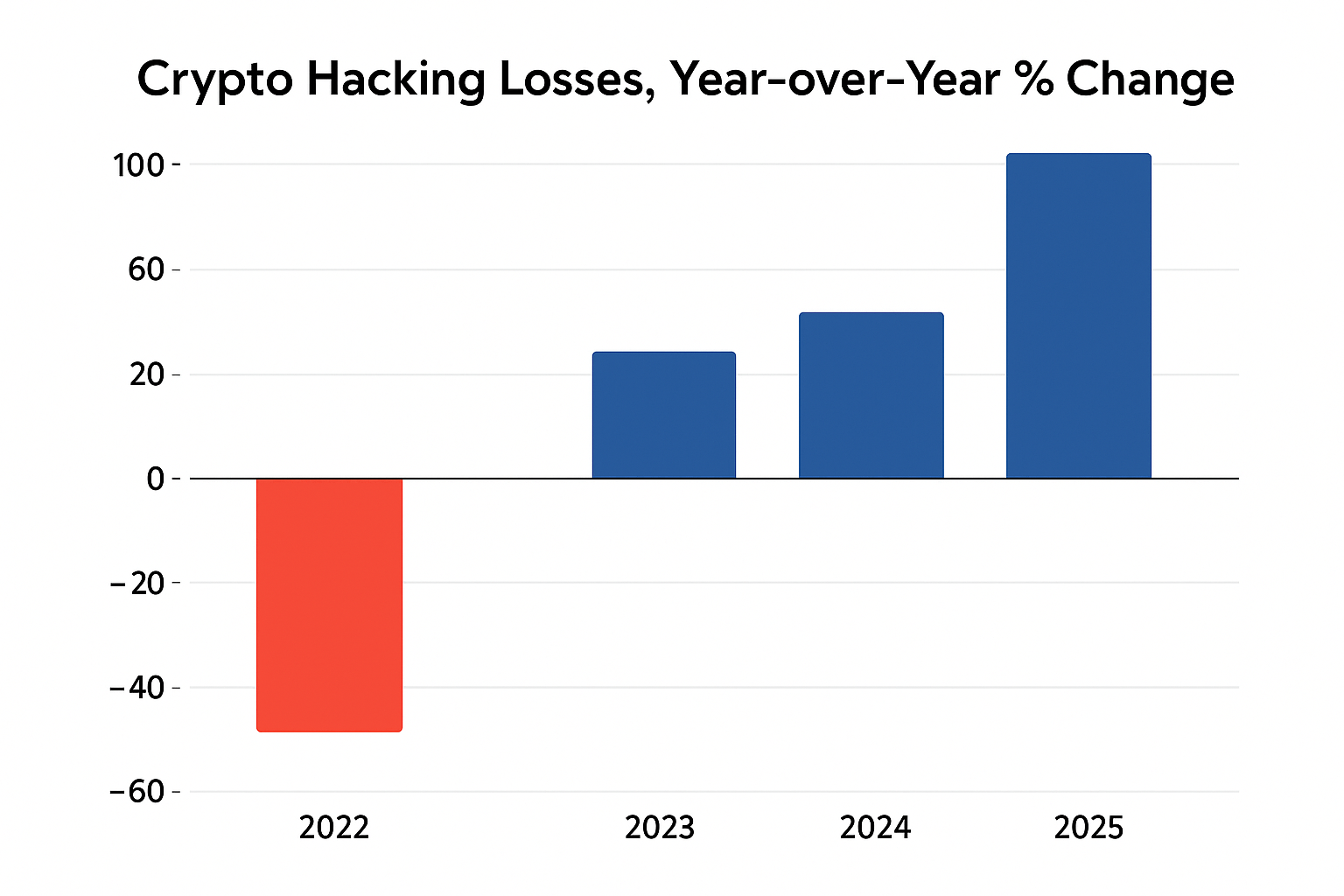
Crypto hacking losses did not rise in a straight line, they fell hard after the 2022 peak, then climbed again in 2024 and surged in 2025. In 2022, Chainalysis recorded a record $3.8 billion in stolen crypto. In 2023, totals dropped to about $1.7 billion, a decline of ~54 percent year over year. This sharp reduction tracked the cooldown in DeFi protocol exploits that had driven the 2021 to 2022 spike.
The trend reversed in 2024. Chainalysis reported ~$2.2 billion in funds stolen, an increase of ~21 percent versus 2023. Incident counts rose as well, from 282 to 303, with the majority of value tied to compromised private keys at centralized services. Several nine-figure service breaches contributed to the rebound.
Momentum accelerated in 2025. By July 17, 2025, stolen funds had already reached ~$2.17 billion, essentially matching the entire 2024 total with half the year still remaining. Chainalysis noted that this was the largest first-half value since its tracking began, driven heavily by the ~$1.5 billion Bybit theft attributed by investigators to North Korea linked actors. Chainalysis also flagged that by the end of June, year-to-date stolen value was 17 percent higher than in 2022 at the same point, underscoring how concentrated service breaches can outweigh improvements elsewhere.
Putting the percentages together for clarity.
• 2022 → 2023: down ~54 percent.
• 2023 → 2024: up ~21 percent.
• 2024 → 2025 H1-to-date: ~99 percent of 2024’s full-year losses had already been reached by mid-July 2025, indicating a steep upward swing within the year.
Key takeaway. After a post-peak pullback in 2023, the percentage trend turned positive, first moderately in 2024, then sharply in 2025 as a few very large service breaches dominated totals. Teams should not infer safety from lower incident counts alone, because a small number of high-impact compromises can flip the year-over-year percentage back to strong growth.
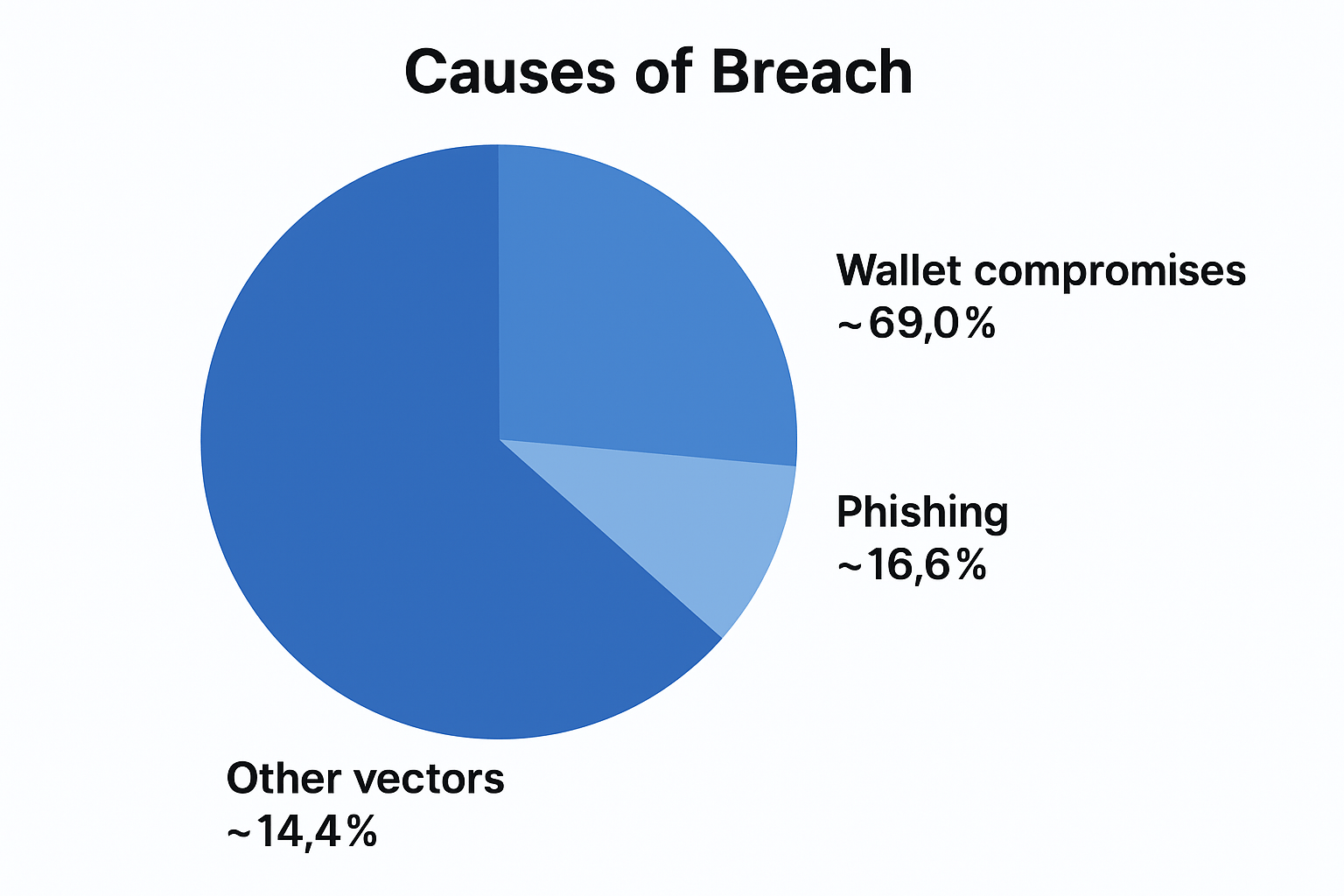
The 2025 pattern is clear, high-value losses skew toward wallet takeovers, while phishing drives the most incident volume. Using CertiK’s H1 2025 dataset as the best mid-year snapshot:
For additional color on how the mix shifted during the year, Q2 2025 shows phishing as the top quarterly driver by value, with code exploits in second place:
What this means. Treat keys and wallets as crown jewels, adopt hardware-backed signing and strict device hygiene, and train users on grant approvals and fake interfaces. Pair this with defense-in-depth on protocol code and service operations, since a smaller number of high-impact service breaches can still dominate annual loss totals.
CryptoBreachCauses
The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
Q1. How much was stolen in crypto hacks in 2025 so far
Independent trackers report multi-billion totals by mid-year, led by a few very large service and wallet breaches. Numbers vary by scope and recovery status.
Q2. What are the main causes of crypto breaches in 2025
Wallet takeovers lead by value. Phishing leads by count. Code bugs and service misconfigurations still cause large events.
Q3. Are incidents going up or down year over year
Incident counts can fall while total losses rise. Fewer but larger breaches can drive new highs.
Q4. Which quarter was the worst in 2025
Q1 was the peak for losses. Q2 and Q3 trended lower, with spikes in specific months.
Q5. Which targets are most at risk
Centralized services, custodial wallets, and users with hot wallets. Protocols with weak key management or third-party integrations are also exposed.
Q6. What attack types should teams prioritize
Credential and key theft, phishing, wallet approval scams, supply chain compromises, and logic flaws in smart contracts.
Q7. How do recoveries affect totals
Frozen or returned funds reduce net losses. Some reports list gross losses, others list net. Always check the method.
Q8. What can users do to reduce risk
Use hardware wallets. Verify domains. Limit approvals. Keep devices clean. Never share seed phrases. Use passkeys where available.
Q9. What can exchanges and custodians do
Enforce HSM backed keys. Segregate duties. Monitor withdrawals in real time. Run continuous red teaming. Patch fast and publish postmortems.
Q10. Are state-linked actors involved
Some large events are linked to state-sponsored groups. They target services with high liquidity and weak operational controls.
Q11. Which regions see the most loss
Losses concentrate where liquidity and user counts are highest. Large centralized services skew regional snapshots.
Q12. How reliable are the numbers
They are estimates from reputable firms. Scope, data sources, and recovery timing differ. Triangulate across multiple reports.
Q13. How often is this page updated
When credible new datasets or large incidents appear. Check the update note near the top of the page.
Q14. What is the best single metric to track
Loss per incident. It shows concentration of risk better than incident count alone.
Q15. Can smart contract audits stop hacks
Audits reduce risk but do not eliminate it. Use audits, bug bounties, formal verification, and runtime monitors together.
The 2025 picture is clear. Fewer incidents can still mean higher losses, and large service or wallet breaches shape annual totals. Q1 set records, then pressure eased, though September reminded everyone that risk clusters can return quickly. For exchanges and custodians, prioritize key management, change control, and rapid incident response. For users and merchants, hardware keys, phishing education, and careful app permissions reduce exposure. Bookmark this page. We update it as new crypto hacking incidents statistics 2025 data appears.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us