February 12, 2025
Updated: February 12, 2025
Top tools, stacks, and frameworks for AWS, Azure, GCP, and Kubernetes cloud pentesting with automation, CI/CD integration, and PTaaS insights.
Mohammed Khalil

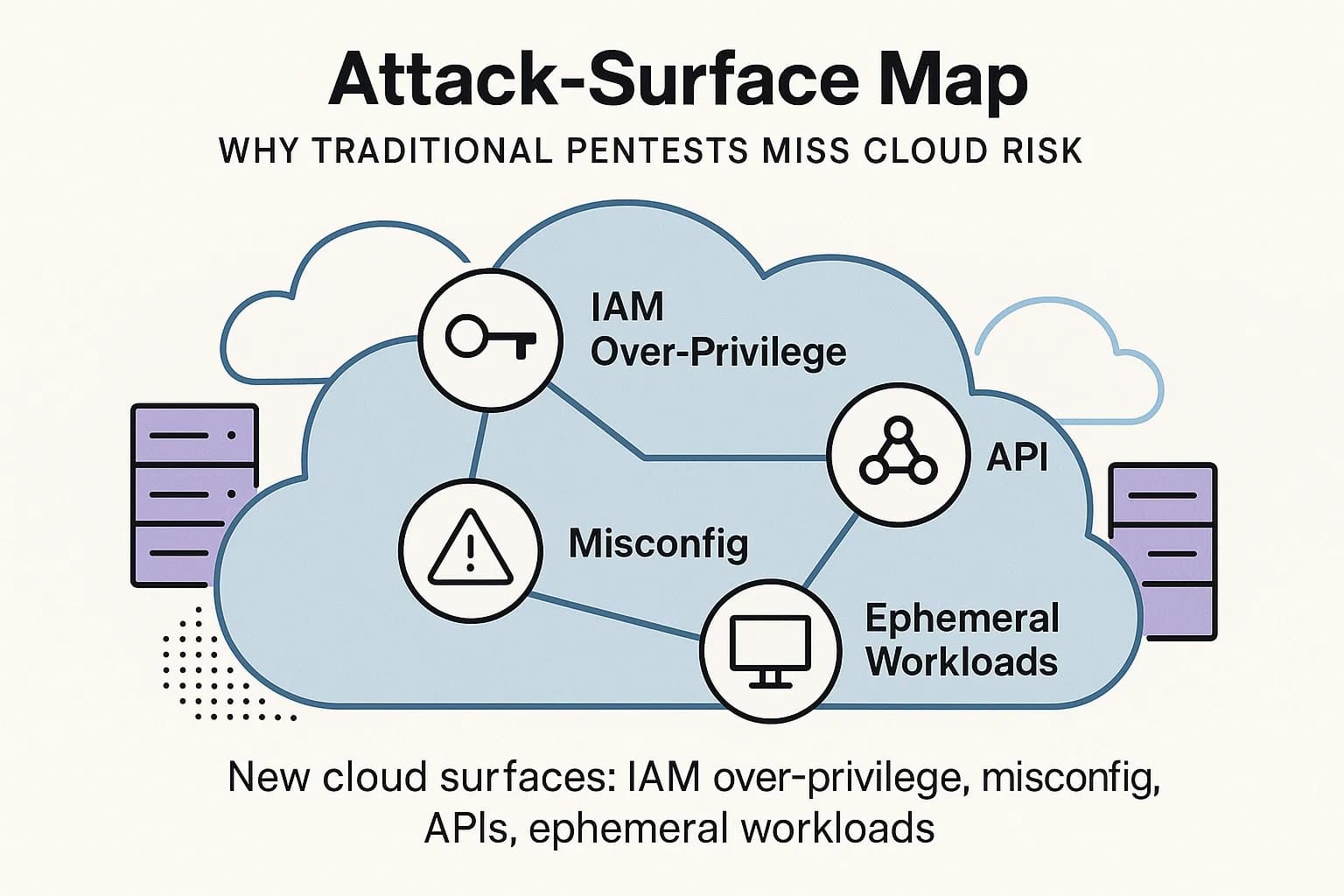
Cloud adoption and multi cloud architectures have exploded, but security hasn’t kept pace. According to Check Point’s 2025 Cloud Security Report, 65% of organizations had a cloud related incident last year.
Misconfigurations like public storage or open ports and IAM misuses are top culprits. For example, IAM weaknesses fuel breaches, overprivileged accounts, lack of MFA. enable attackers to abuse access. A cloud pen test must therefore go beyond traditional on prem checks, probing APIs, service accounts, and ephemeral cloud assets.
This article answers the key question, what are the best tools and methods for cloud penetration testing today? We cover specialized tools, how they fit together in stacks for AWS/Azure/GCP/Kubernetes, pipeline integration, and mapping to compliance frameworks, all with actionable examples and expert insights.
Cloud environments differ radically from on premises networks. Testers face a shared‑responsibility model, API driven services, and strict provider rules. Instead of fixed servers, cloud apps use ephemeral resources containers, auto scaled VMs, serverless functions that appear and vanish as traffic changes.
As one security evangelist notes, Cloud resources are often created and destroyed automatically based on usage. This makes it difficult to detect vulnerabilities in assets that may only exist for a short time. Meanwhile, scattered in multi account setups and microservices, it’s easy for configurations to drift out of sync.
On the identity front, cloud tests must focus on IAM abuse and the control plane. Attackers often exploit over permissive roles or long lived keys AWS IAM policies with excessive privileges or Azure misconfigured RBAC paths. By contrast, on prem tests focus on lateral movements in fixed networks and AD domains.
Cloud tests must combine identity abuse privilege escalation via IAM chains with API and management plane exploits. They also contend with provider limits for example, you must avoid DoS or breaking SLAs, and get provider approval if running authenticated attacks. In short, cloud pen testing requires new tactics testing misconfigured APIs, public buckets, secret leaks, and cross service attack paths that go beyond classic perimeter scanning.
Cloud pen testing places IAM at center stage. Overly broad policies or missing MFA let attackers escalate privileges. As Check Point warns, overprivileged accounts… enable attackers to abuse access and escalate privileges. Tools must enumerate all roles and keys see pmapper for AWS IAM graphs and attempt to exploit weak policies.
Misconfigurations remain the number1 threat public storage buckets and permissive security groups consistently open doors. Cloud pen tests actively look for these for example using ScoutSuite or CSPM tools to flag unencrypted data stores or admin ports open to the internet. In short, a cloud test mimics an attacker chaining IAM flaws with misconfigs for instance, an exposed S3 bucket combined with a suboptimal IAM role can let a tester steal secrets or escalate access.
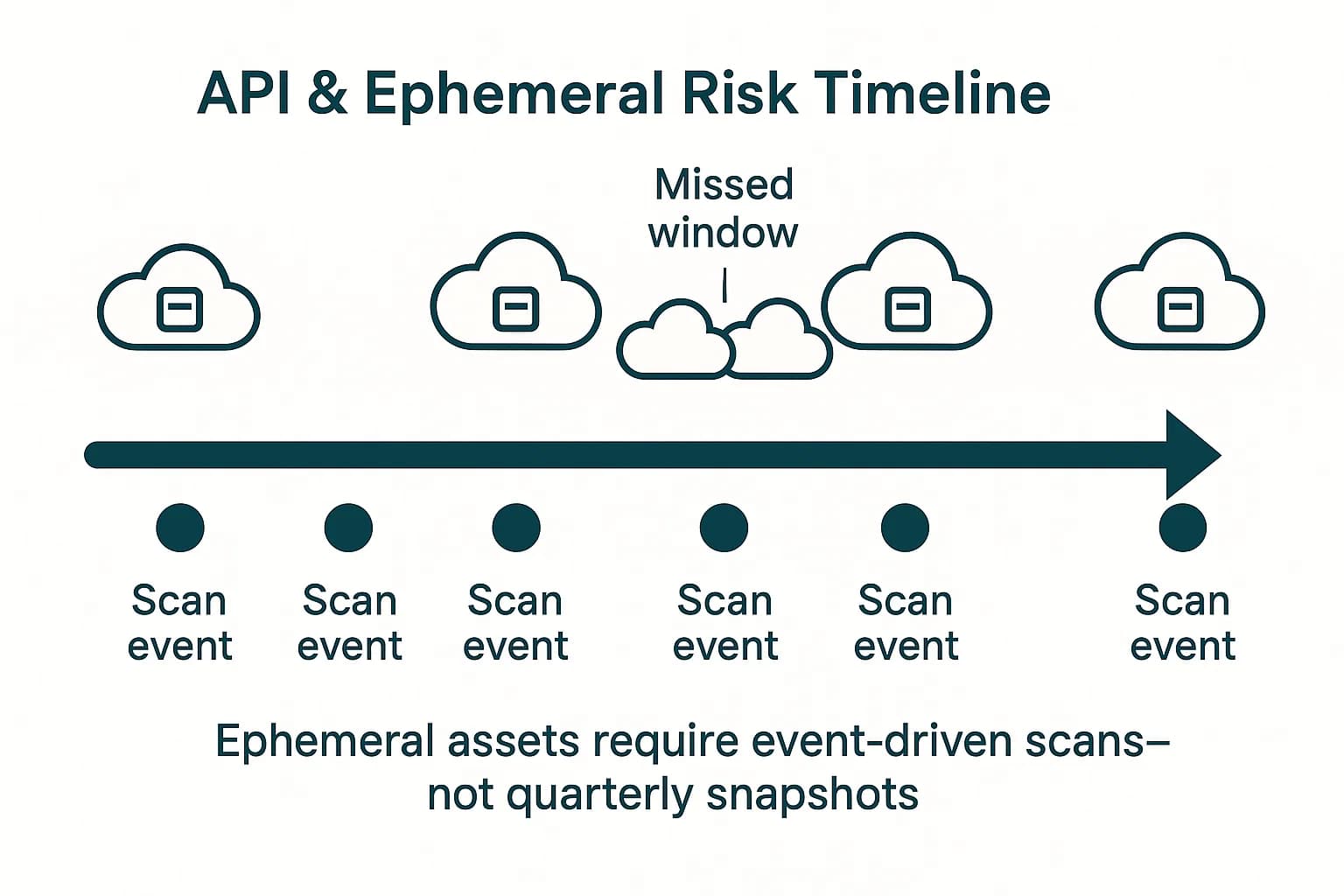
Unlike static on prem servers, cloud resources are managed through APIs. Attackers often exploit cloud APIs directly e.g. AWS APIs or Azure’s ARM REST to pivot or exfiltrate data.
Also, cloud accounts scale dynamically, spinning up thousands of VMs or containers. A vulnerability may exist only briefly unless scans run continuously. And multi account environments for dev, prod, multiple teams can drift, each account may have inconsistent security posture. For example, a misconfigured database in one AWS account may be missed if your scanner only targets the main account.
So cloud pen testing tools must inventory assets across accounts and even across clouds. Tools like CloudMapper help visualize AWS networks, while CSPM platforms consolidate policies across AWS/Azure/GCP.
In practice, a cloud tester must routinely rescan as one expert warns, if your scanners aren’t set for change events, new vulnerabilities can slip through. Overall, these differences make cloud tests an API centric, continuous, identity driven exercise, quite unlike a one off network scan on fixed infrastructure.
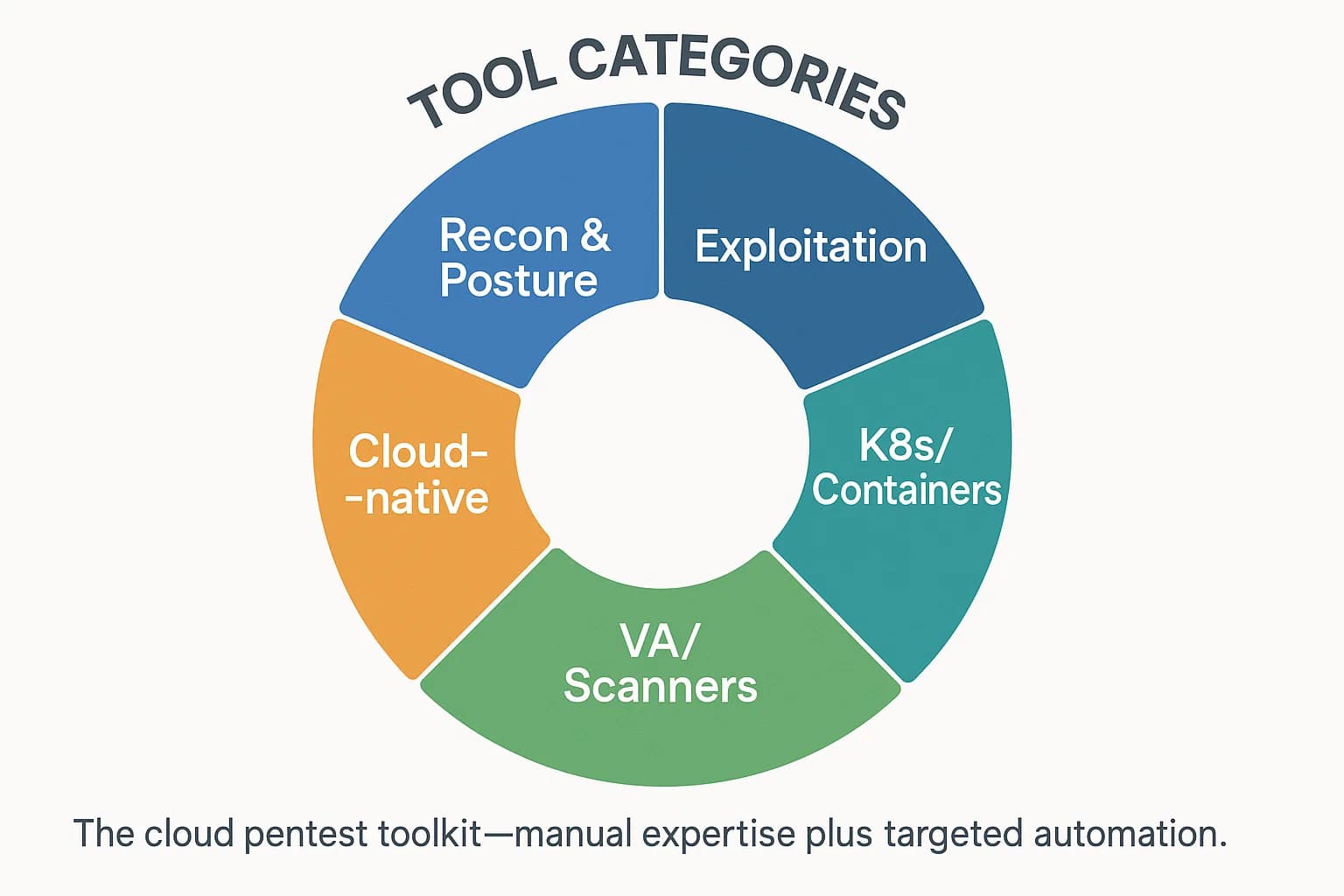
Cloud pen testing tools fall into several categories. Below we map out open source and commercial options for each use case. Each tool is briefly described, with notes on when it excels.
Reconnaissance and posture assessment tools crawl your cloud inventory and flag misconfigurations. Open source scanners like Prowler AWS centric run CIS/NIST checks on IAM, S3, EC2, etc. For example, Prowler’s CIS benchmark reports help satisfy compliance and quickly surface risky resources.
ScoutSuite by NCC Group is a multi‑cloud auditor, it uses APIs to gather and summarize AWS/Azure/GCP configurations in a single report. Likewise, CloudMapper Duo Labs visualizes AWS networks and finds open security groups. Native cloud services also exist, AWS Inspector see below and Microsoft Defender for Cloud include posture checks and continuous monitoring.
Commercial CSPM/CNAPP products like Palo Alto Prisma or Check Point CloudGuard offer agents and dashboards across clouds. In general, CSPM tools automate the check config vs best practices step as Palo Alto notes, they automate the detection and remediation of misconfigurations across cloud resources. By using these tools, testers build inventory assets, policies, network paths and catch obvious gaps before deeper exploitation.
For hands-on attacks, specialized exploitation frameworks exist in each cloud. Pacu AWS is the leading open source toolkit essentially Metasploit for AWS. It has 35+ modules covering every phase, recon, persistence, privilege escalation, data exfiltration, and cleanup. For instance, Pacu can test S3 bucket permissions, spawn backdoor Lambda functions, or abuse EC2 metadata to escalate privileges.
For Azure, MicroBurst by NetSPI is a PowerShell suite for Azure discovery and exploitation. It automates common AD/cloud techniques like dumping credentials, abusing managed identities, or spooling tokens.
GCPBucketBrute is a Python tool by Rhino Security that brute forces Google Cloud Storage bucket names and tests your access to each crucial step in GCP tests, as it identifies public or weakly protected buckets and their privileges. In short, these exploitation tools mimic attacker methods Pacu chains IAM roles and KMS privileges, MicroBurst hunts Azure AD attack paths, and GCPBucketBrute finds and abuses open cloud storage. Commercial red team platforms e.g. Cobalt Strike with cloud scripts can supplement them, but these open tools are battle tested by cloud security experts.
Kubernetes and container workloads introduce their own risks. Popular open source tools include kube bench CIS benchmark checker for Kubernetes and kube hunter Aqua Security which actively probes clusters for exposed services and misconfigurations. For example, kube bench will list any nodes or pods that fail CIS settings RBAC rules, API server configs, while kube hunter can simulate attacks exposed dashboards, open etcd, etc. from an attacker’s view.
Kubescape ARMO is a comprehensive K8s security scanner that evaluates clusters against frameworks like NSA guidelines or MITRE ATT&CK. It gives posture reports on network policies, pod settings, etc.
At the image level, container scanners like Trivy Aqua or Syft+Grype find vulnerabilities and secrets inside images. Trivy, for instance, scans container images and Kubernetes resources for vulnerabilities, misconfigurations, and hidden secrets, making it ideal for catching insecure base images. In practice, a Kubernetes pen test workflow might use kube bench to check for insecure cluster settings, then run kube hunter and Kubescape for runtime exposures, and finally scan the app images with Trivy to ensure no known CVEs slipped in.
While penetration testing focuses on business logic and chained exploits, vulnerability scanners remain useful for cloud asset scanning. AWS Inspector native AWS automatically discovers EC2 instances, ECR images, and Lambda functions, and continually scans them for software vulnerabilities and unintended network exposure. It reports CVE findings and network risks directly in AWS Security Hub.
Similarly, third party scanners like Tenable Nessus, Qualys Cloud Security, and Rapid7 can run on cloud hosts via agents or network scans. These tools use large vulnerability databases e.g. CVEs to flag missing patches or misconfigured services across AWS/Azure/GCP VMs.
For example, Nessus Cloud Edition can orchestrate scans of your cloud VPC or managed instances. The advantage they produce detailed reports often in HTML/JSON that compliance teams expect.
In summary, native scanners like Inspector and multi cloud tools like Nessus/Tenable fill out the vulnerability assessment box, complementing the offensive tools above.
Each cloud platform has a recommended stack of tools and playbooks. Below we outline example stacks for AWS, Azure, GCP and Kubernetes, combining open source and native tools. These playbooks serve as step by step templates for pentesters and DevSecOps teams.
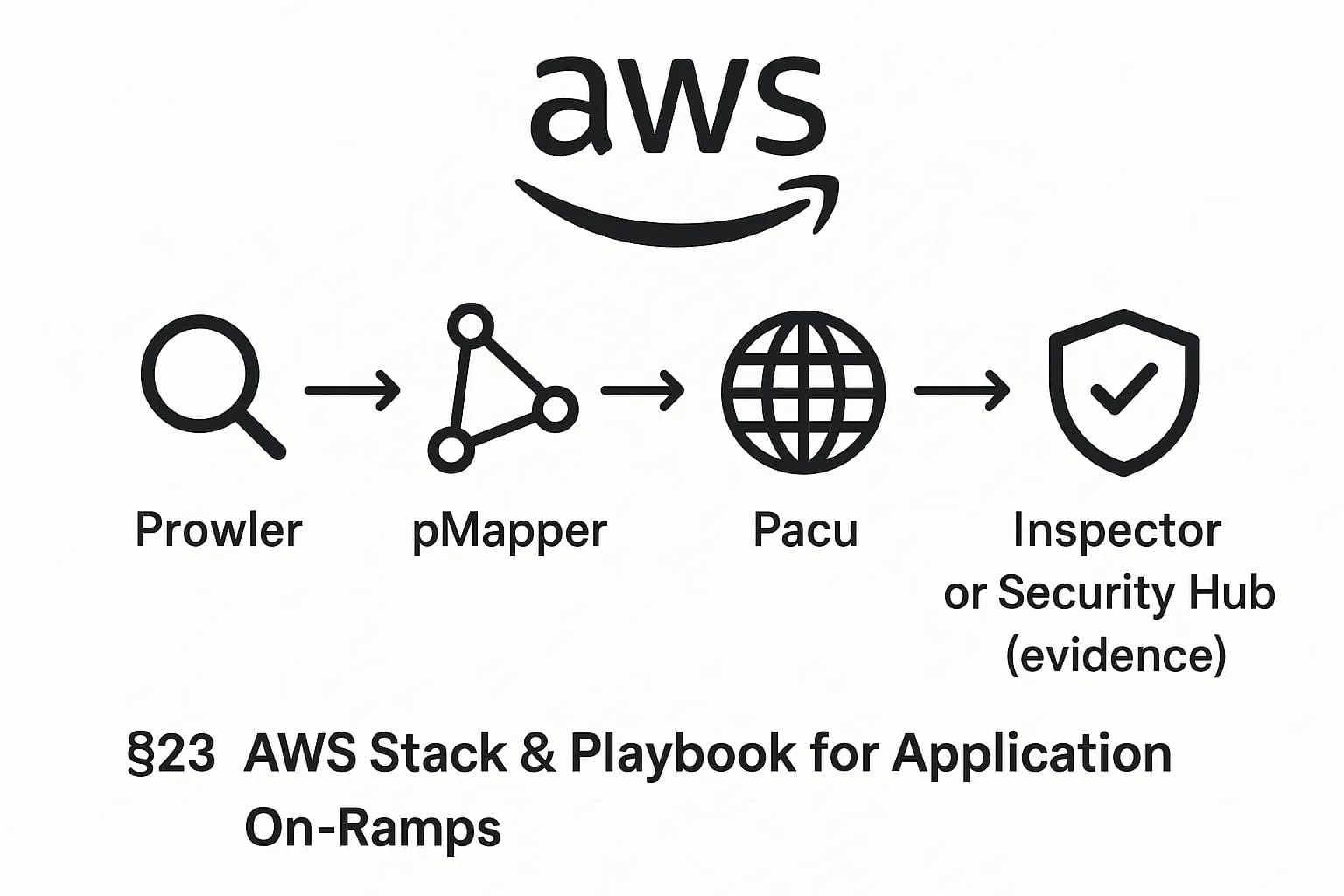
For AWS environments, a typical pen test flow starts with reconnaissance. Run Prowler to audit all AWS accounts against CIS, NIST, or PCI benchmarks. Prowler will generate an HTML report on IAM policies, S3 buckets, security groups, etc. From there, use pmapper AWS IAM visualizer to build a graph of user/role relationships and spot privilege escalation paths.
Once you identify promising paths e.g. a role with S3 read and EC2 launch, shift into attack mode with Pacu. For example, feed Pacu partial credentials or a compromised role Pacu can enumerate remaining permissions, attempt EC2 impersonation, exfiltrate S3 data, abuse KMS keys, or disrupt CloudTrail logs.
Document each step screenshot the Pacu findings and note the commands in your report. After remediation, re-run Prowler/ScoutSuite to show the misconfigurations are fixed.
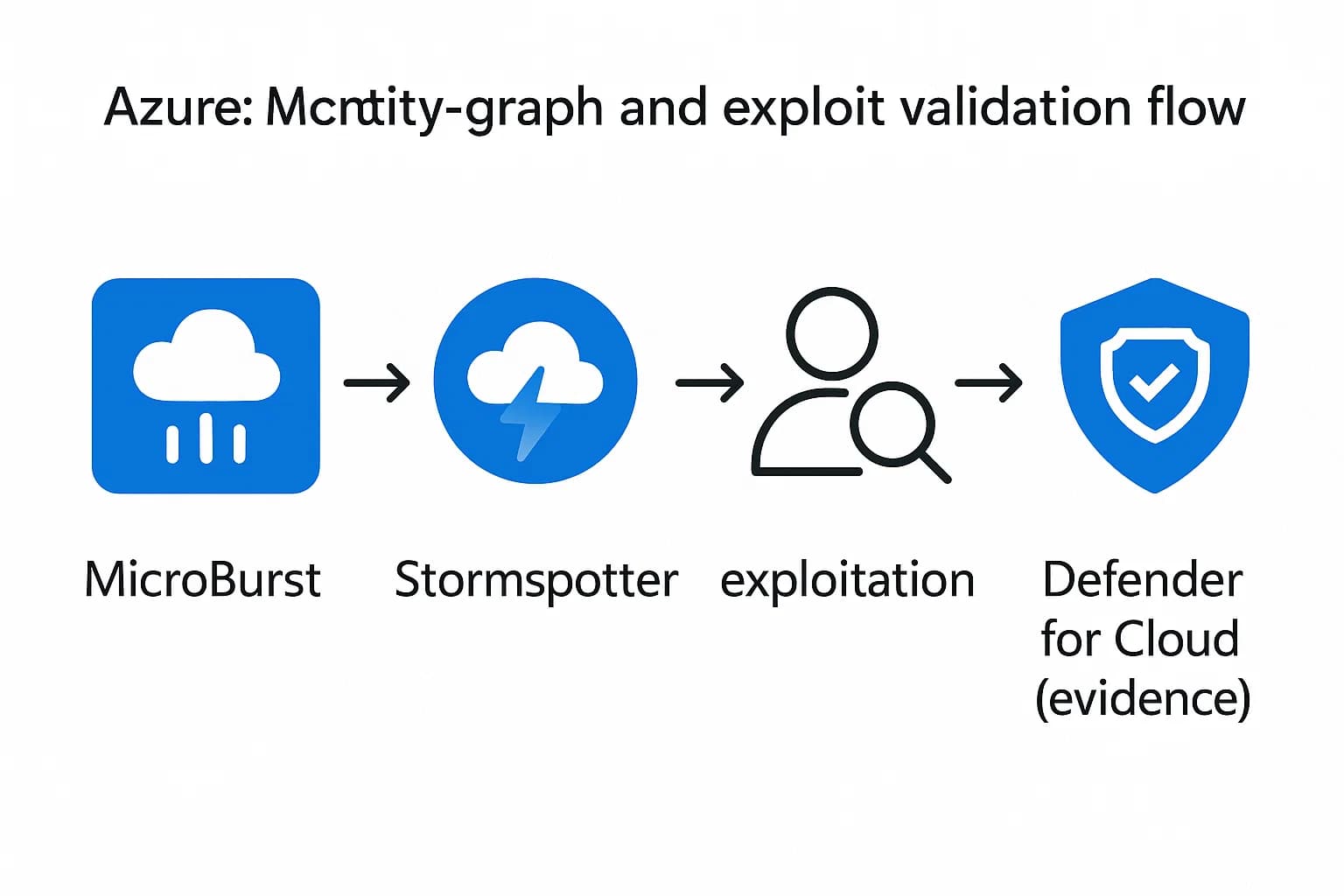
On Azure, use MicroBurst to gather information on Azure AD and resources. Start by enumerating user roles and permissions via AzureAD or MSOnline modules, then check for weak configurations e.g. no MFA on highly privileged accounts. Next, Stormspotter Azure AD attack graph to automatically map identity paths shows how a user could jump between apps, roles, and subscriptions. With these paths in hand, attempt exploitation for instance, simulate credential dump via a compromised VM using MicroBurst functions, or exploit an App Service by injecting malicious script remembering Azure Pentest rules!.
Through collecting Defender for Cloud findings Microsoft’s Defender for Cloud CNAPP can run agentless scans of VMs Defender for Servers and check Azure posture automatically. Compare before/after e.g. an open management port flagged by Defender, then closed after fix. Finally, use the Defender compliance reports which include CIS/Azure benchmarks as audit evidence that your remediation satisfies policies linking to Azure’s built in compliance center.
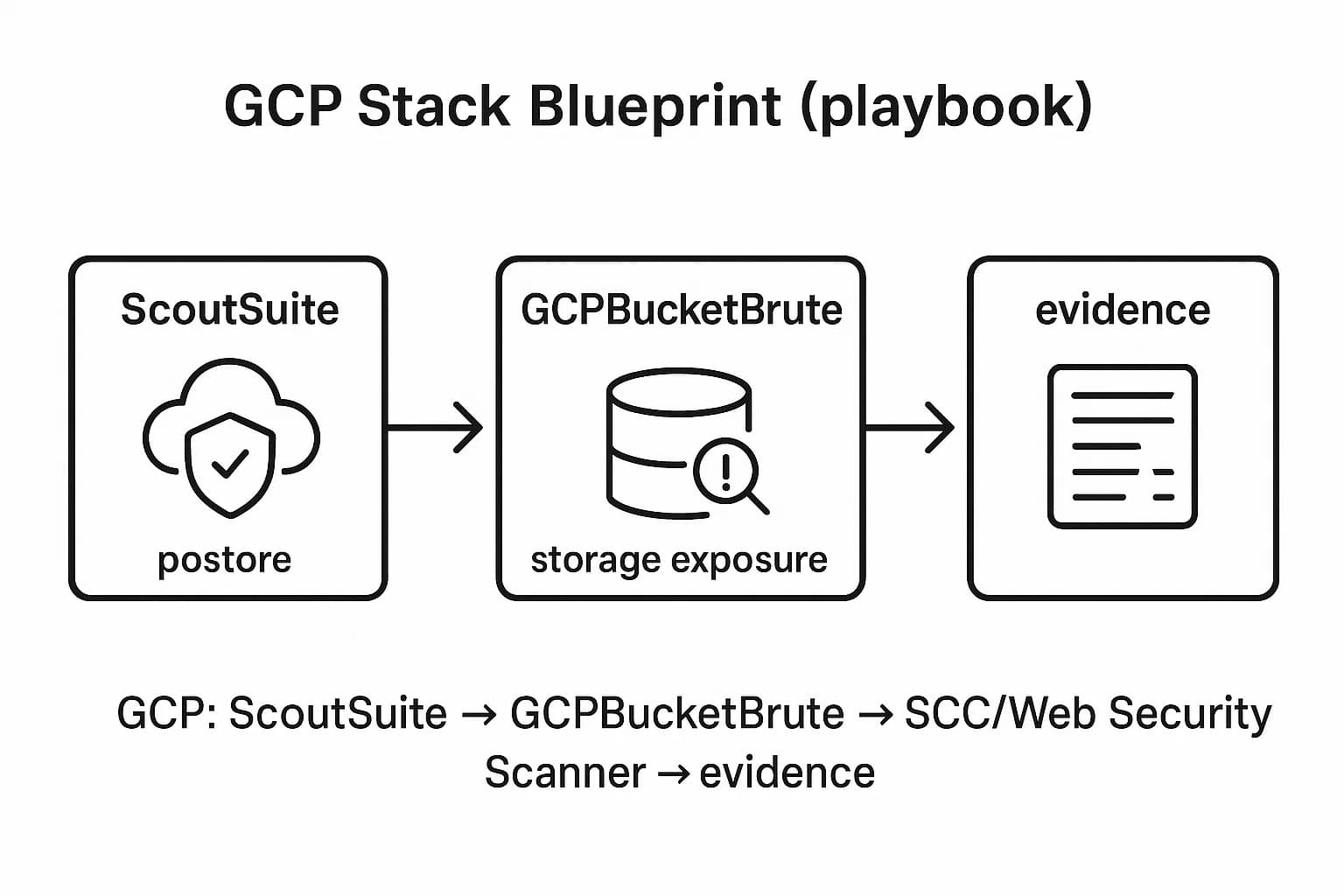
For Google Cloud, begin with ScoutSuite to snapshot the GCP project. It will report on IAM bindings, firewall rules, open Cloud Storage, and more across GCP.
Identify risky resources, public buckets, broad roles on service accounts, enabled APIs, etc.. Next, run GCPBucketBrute to actively discover misnamed Google Storage buckets and test your access permissions on each. For example, if ScoutSuite shows an empty bucket name field, use BucketBrute to enumerate it. Each discovered bucket should be tested for ACL or IAM weaknesses, the tool can automate TestIamPermissions calls. Capture the output if BucketBrute finds a writable bucket, that’s a clear exploit path.
Finally, review Google’s Security Command Center findings of its native SCC or Google Cloud Web Security Scanner if web apps are present to correlate scanner alerts with your manual finds. Document remediation by saving ScoutSuite reports before/after fixes, and showing fixed bucket access with a new scan.
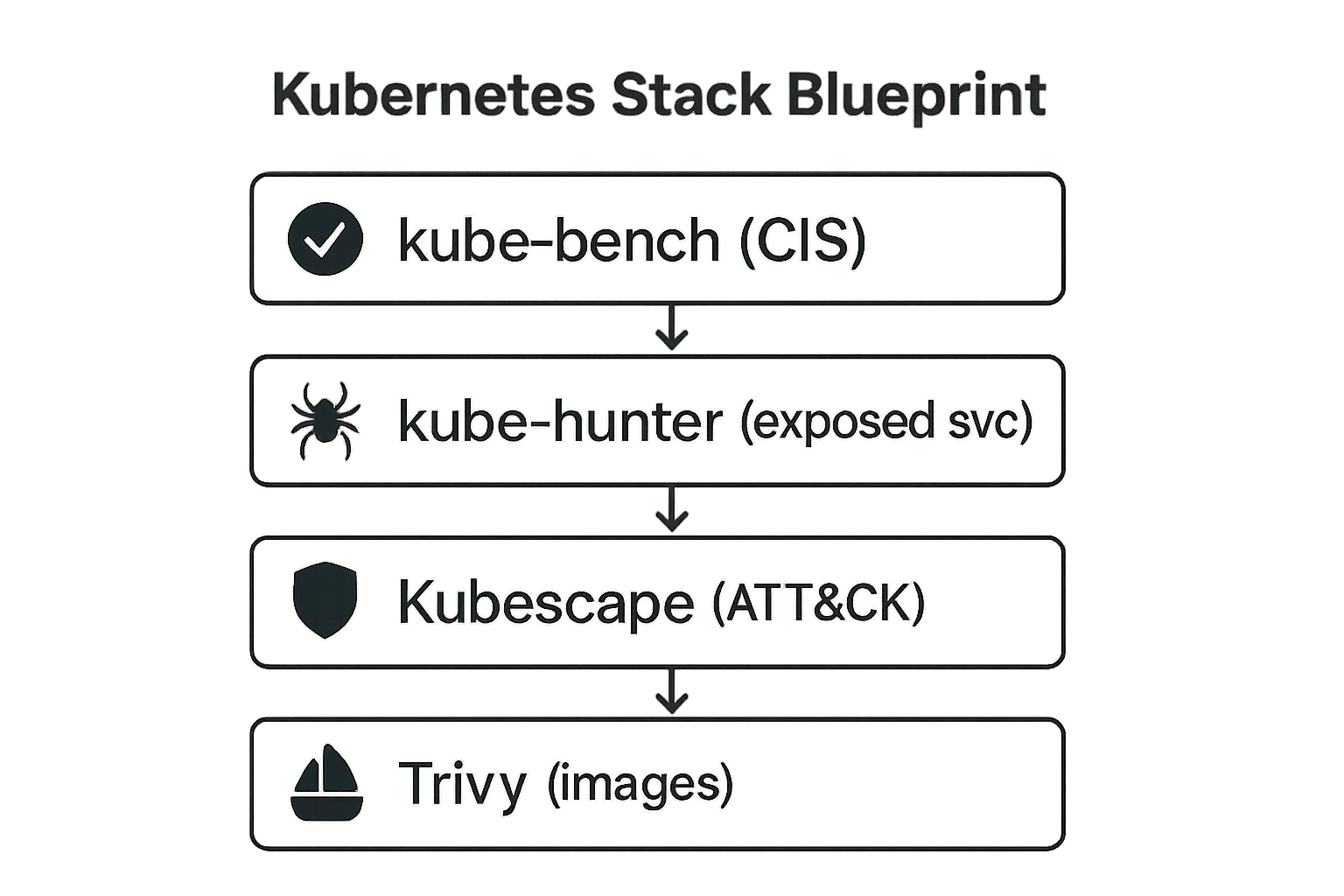
For Kubernetes workloads EKS/AKS/GKE, we recommend a layered approach first, using a kube bench to verify CIS Kubernetes benchmarks on the cluster control plane and nodes. If kube bench flags issues e.g. Pod SecurityPolicy not defined or Allowed privileged containers, remediate them and retest, capturing screenshots of the reports.
Next, run kube hunter from outside the cluster it will simulate an attacker searching for exposures, open dashboards, kubelet ports, etc.. It generates a summary of high risk findings e.g. kubelet is unsecured, logs these and fixes accordingly.
Finally, use Kubescape or similar CSPM to perform a full posture check against frameworks like MITRE ATT&CK or NSA/CIS controls. Kubescape will output JSON/HTML results for any remaining misconfigs.
Each tool’s output kube bench summary, kube hunter report, Kubescape findings becomes part of your evidence pack. By following this stack benchmark recon compliance scan, you ensure clusters start hardened and stay monitored over time.
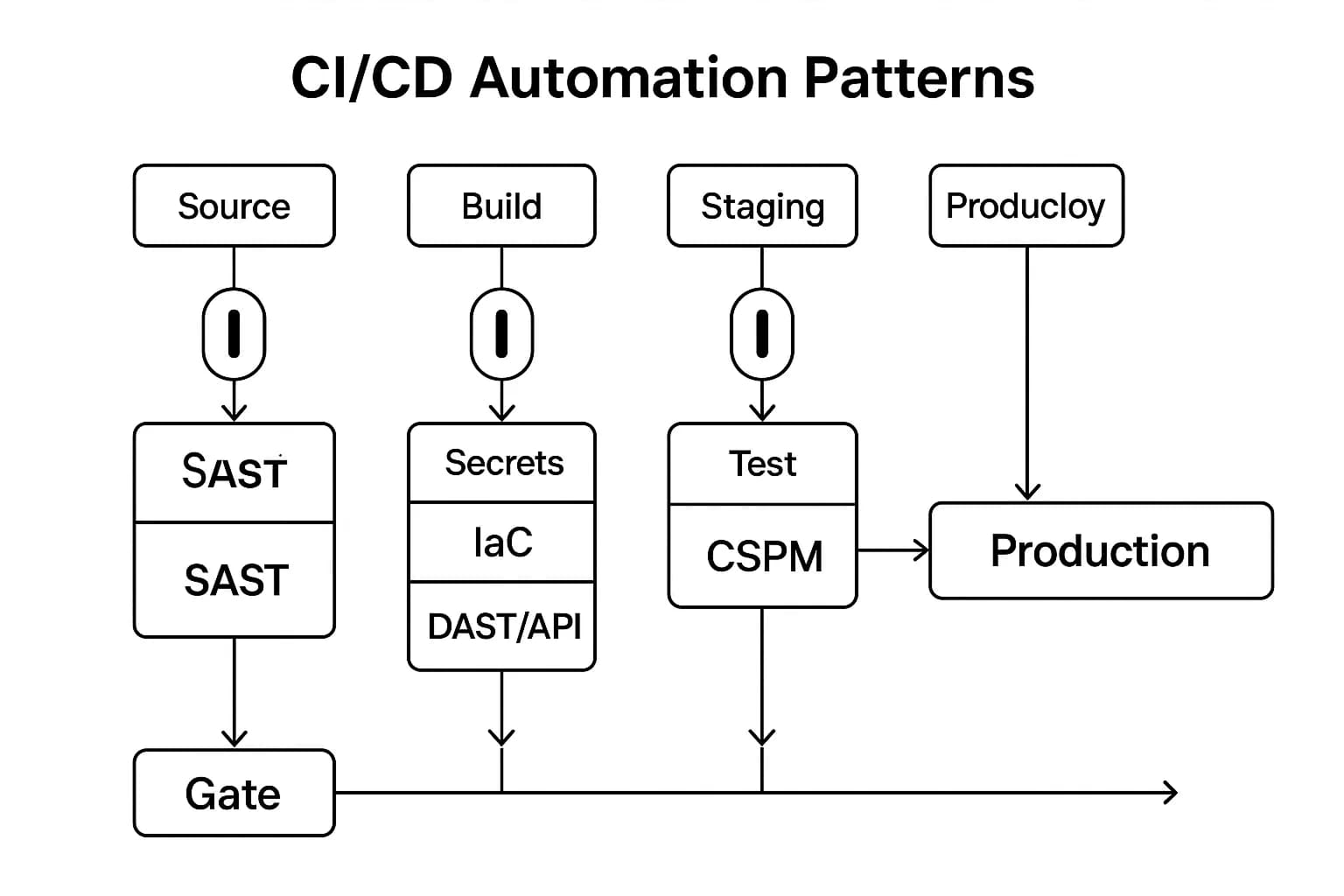
Cloud security must fit into DevOps pipelines. Here are common automation patterns and tools:
Pre commit/PR gates:
Pre deploy IaC:
Staging DAST/API tests:
Post deploy continuous CSPM:
Shifting left is crucial. As advised, Automated security scans can be incorporated into the CI/CD pipeline. allowing for immediate feedback on potential security issues.
In practice, developers love actionable pipeline feedback PR comments with fix hints, automated tickets for hotspots, or even pre-built remediation snippets in code reviews.
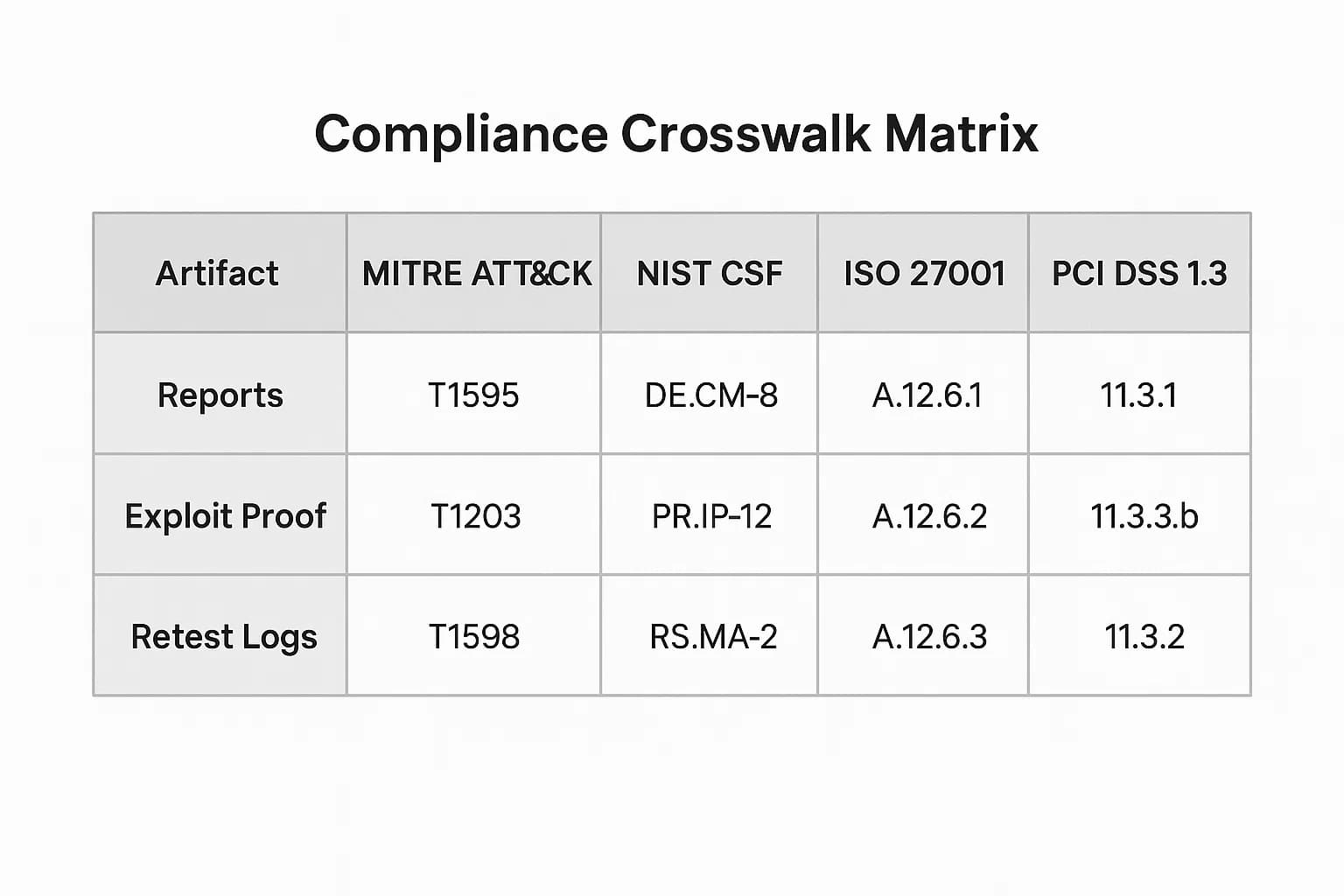
Pen tests and scans should map to frameworks to aid reporting and audits. Here’s how to correlate tools with common frameworks:
MITRE ATT&CK Cloud:
NIST CSF Identify/Protect/Detect/Respond:
ISO 27001 / PCI DSS 11.3:
For example, a CSPM scan report from Defender for Cloud or Prowler could be used as proof of compliance checks. See our SOC 2 penetration testing requirements and FedRAMP pentesting guide for specifics on cloud audit mapping.
In essence, collect evidence packs raw scan outputs JSON/HTML, tool generated Excel worksheets, command logs and screenshots of fixes, and a narrative of the test scope ROE, tool versions.
This makes compliance smoother and demonstrates that you tested the right things by alignment with NIST/ISO/PCI controls.
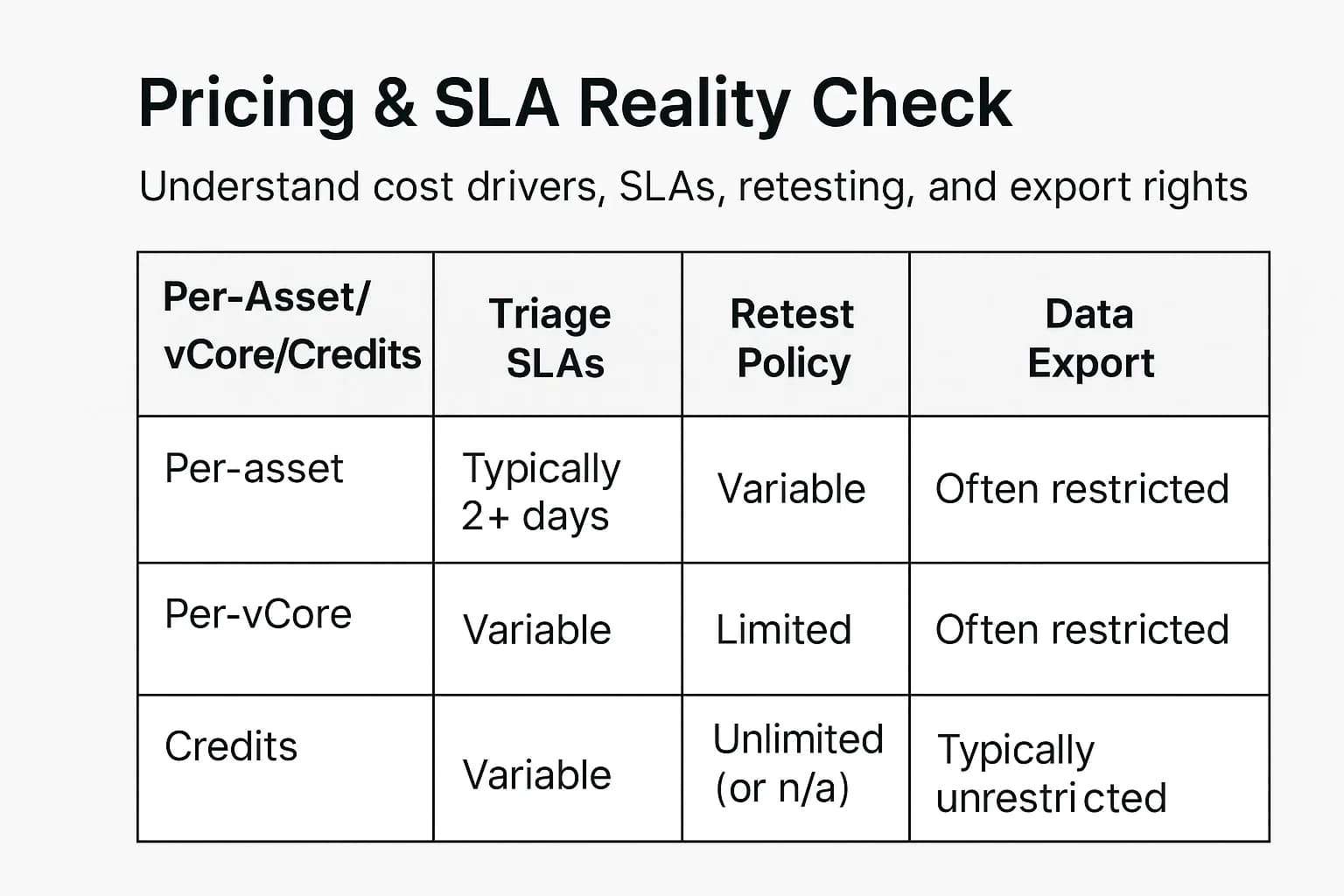
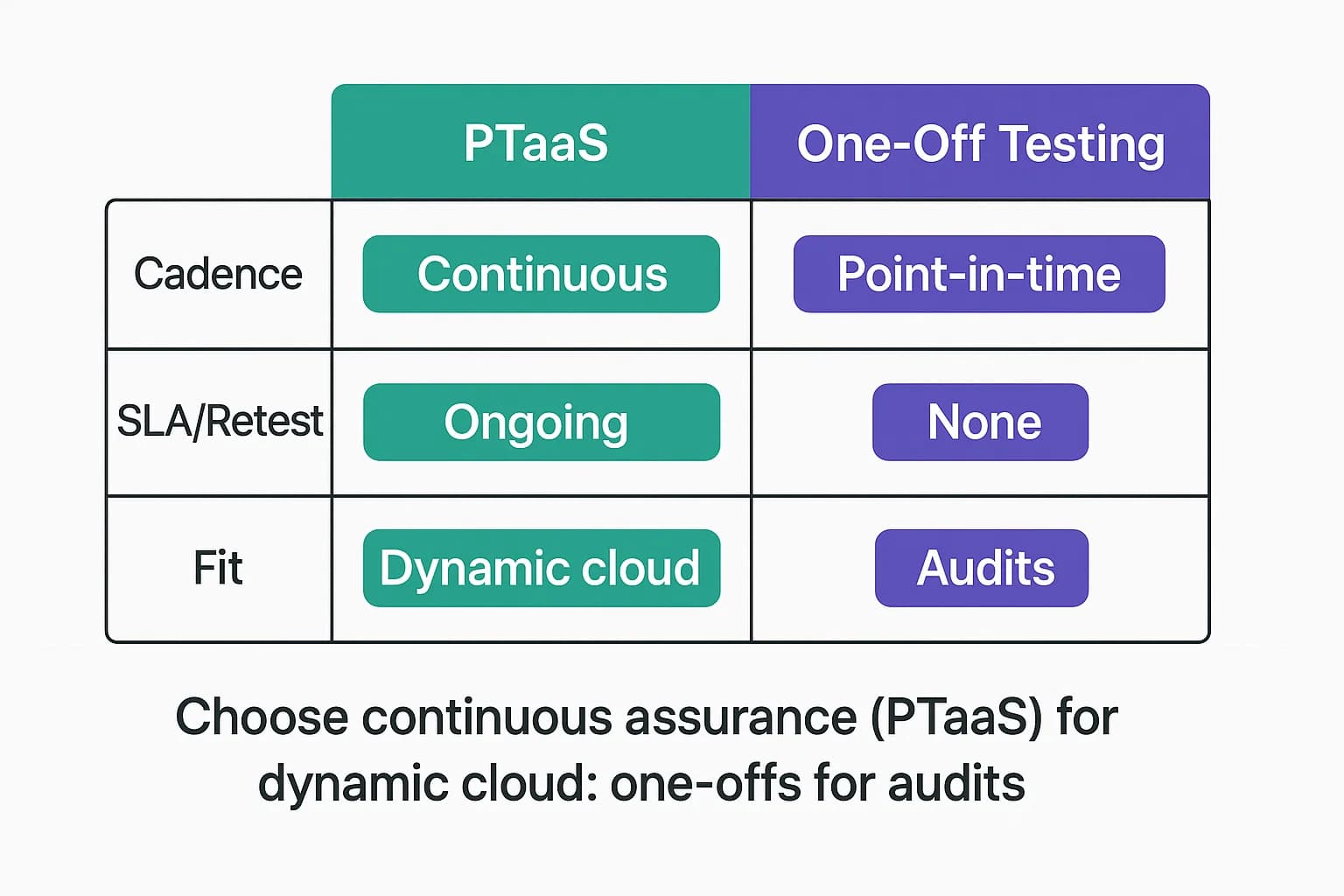
Modern teams often choose between one off pen tests and Penetration Testing as a Service PTaaS subscriptions. Key differences:
Pricing models:
On demand vs scheduled:
Deliverables & SLAs:
When to use which? Point in time pen tests fit compliance cycles or large yearly reviews e.g. before SOC 2 audit, run one thorough test.
PTaaS suits agile orgs needing continuous assurance DevSecOps shops or high change environments. Many organizations combine both a PTaaS subscription for continuous monitoring, plus a red team style one off for deep dive.
SLA / ROE Checklist:
Cloud environments demand specialized testing. With this guide’s strategies and tools, your team can validate AWS, Azure, GCP and K8s defenses effectively.
Always think identity first poke IAM roles, APIs, and dynamic assets. Integrate scanning early in DevOps, and tie results to frameworks like MITRE or NIST for clarity. The threats of 2025 demand more than just awareness, they require readiness.

Ready to strengthen your defenses? Our DeepStrike practitioners are here to help. Explore our penetration testing services to see how we can uncover hidden risks before attackers do. We provide clear, actionable guidance to protect your business in the cloud era Drop us a line anytime.
About the Author: Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
CSPM Cloud Security Posture Management is automated, continuous monitoring of cloud configurations against best practices. It continuously checks for misconfigurations like open ports or unencrypted storage and alerts teams.
Cloud penetration testing, by contrast, is human driven, it attempts to exploit vulnerabilities to demonstrate real impact data theft, privilege escalations. CSPM finds issues, while pentesting proves exploitability. They complement each other CSPM flags risks early, and pentests validate whether those risks are truly exploitable in your environment.
Not exactly. Vulnerability scanners commercial or open source will automatically scan for known issues CVEs, missing patches and report findings. True penetration testing goes further, it involves human or advanced scripts chaining exploits across systems to mimic an attacker.
Sometimes automated pen testing marketing means a platform that schedules periodic scans with manual review, it is not purely a one click scanner. Think of scanners as one leg of the stool vuln assessment, whereas pentesting simulates real attack scenarios. For critical assets, you’ll usually want both automated scans for breadth, and expert pentesters for depth. See also vulnerability assessment vs penetration testing.
AWS, Azure, and GCP have their own native tools and a growing ecosystem of cross platform tools. For AWS, top picks are Prowler CIS auditing, Pacu exploitation, pMapper IAM analysis and AWS Inspector vuln scanning. For Azure, consider MicroBurst PowerShell attacks, Stormspotter Azure AD graphing, and Microsoft Defender for Cloud built in CSPM/vuln scans.
For GCP, ScoutSuite multi cloud audit and GCPBucketBrute storage enumeration are key. Many tools like ScoutSuite, Prowler, and kube hunter work across clouds. In practice, pick tools that are cloud native.
MITRE ATT&CK Cloud categorizes attacker tactics. To align tests: first identify which ATT&CK techniques your tools cover. For example, testing AWS IAM abuse Techniques T1078.004, T1531 can be done with Pacu modules that try credential reuse or metadata hacks.
Data exfiltration via cloud storage T1530 can be demonstrated by reading a misconfigured S3/GCS bucket using cloud SDK or tools like GCPBucketBrute. Create a table mapping each pentest step or finding back to ATT&CK IDs. This not only shows coverage of known attack patterns, but also helps SOC teams integrate the findings. Detailed mapping is often part of an evidence worksheet in audits.
Yes, with precautions. Prowler and ScoutSuite perform read only API calls, they don’t exploit or change resources. They are generally safe to integrate. For example, you can trigger ScoutSuite on each commit to inventory your cloud accounts or run Prowler nightly to check for new misconfigs. That said, be mindful of API rate limits and permissions use a service account with least privilege needed for reading configs.
Also, filter scope in CI e.g. only prod account on release commits. Many teams run these tools in a staging environment or on cloned credentials to avoid hitting production limits. In short, treat them like automated auditors, they’ll catch misconfigurations without breaking anything. Just double check the latest tool docs for any special flags, none modify resources by default.
Auditors usually want proof that you ran the scans and fixed the findings. Acceptable artifacts include full scan reports CSV/HTML/JSON output from your tools, screenshots or logs of execution, network diagrams, and any remediation evidence. For PCI DSS 11.3, an official scan report from an accredited scanner is typical.
For ISO 27001, provide a mixed CIS benchmark output Prowler/ScoutSuite, filtered vulnerability lists, configuration change logs, and a summary document or spreadsheet linking each control to your evidence. Also include your testing methodology scope, tools, ROE and timelines. The key is traceability of each flagged issue and its fix should be documented. We provide an Evidence Mapping Worksheet XLSX to help collect everything in one place for audits.
Neither is inherently better, it depends on your needs. A yearly or quarterly pen test is useful for formal reviews or compliance, it’s a deep dive with a fixed scope and final report. However, the environment may change rapidly after the test.
PTaaS offers continuous testing and on demand re testing. As PentestPeople notes, traditional pen testing provides a snapshot
PTaaS offers continuous, real time testing. For fast moving DevSecOps teams, PTaaS can quickly validate new code or cloud changes without waiting 6-12 months.
That said, PTaaS can be more expensive over time if you don’t use it fully. Many organizations use both a baseline pen test annually for audit and PTaaS in between for agile security. Evaluating ROI PTaaS is worthwhile if your attack surface or code changes often.
CSPM vendors usually charge per cloud resource VM, bucket, etc. or per user/node. To estimate, inventory your assets count your AWS/GCP projects, number of EC2 instances, S3 buckets, Azure subscriptions, etc.
Ask the vendor’s calculator, many have one or spreadsheet for your usage.
Watch out for rapid scaling e.g., container orchestrators can spin up nodes quickly. Also consider data egress or API call costs if the tool is agent based. A safer approach trial the tool on a sample environment to see how usage and credits scale.
Testing a SaaS you don’t own is tricky. Always check the vendor’s policy. Many cloud providers forbid aggressive testing on shared infrastructure. For multi tenant apps, focus on application layer tests only OWASP DAST, auth checks and avoid DoS or low level exploitation.
Use non production accounts, stay below API rate limits, and coordinate with the SaaS provider if possible. Essentially, treat it like any third party pen test, scope it carefully, get permissions maybe a bug bounty program instead of a full pentest, and use only approved methods to avoid impacting other customers.
At minimum, define your scope clearly which accounts, services, subnets, include testing windows to avoid maintenance periods, and specify communication paths for discoveries. Require that testers use whitelisted IPs or VPNs and respect rate limits. The ROE should cover permitted techniques e.g. can’t brute force cloud APIs and confirm the owner’s authorization.
Also include data handling to say how long scan data is kept. A simple rule if in doubt, ask the cloud provider and restrict tests to non peak hours. We offer an SLA/ROE Clause Pack with example language to start from.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us